I’ve covered how to deploy Microsoft Azure MFA with Citrix NetScaler Gateway in the past. I’ve also covered the Azure MFA User Portal in depth where the user can choose their MFA method most convenient to them. You can skim through those guides here:
How to deploy Microsoft Azure MFA & AD Connect with Citrix NetScaler Gateway:
http://www.jasonsamuel.com/2015/09/18/how-to-deploy-microsoft-azure-mfa-ad-connect-with-citrix-netscaler-gateway/
How to deploy Microsoft Azure MFA User Portal on separate servers in the DMZ:
http://www.jasonsamuel.com/2017/03/06/how-to-deploy-microsoft-azure-mfa-user-portal-on-separate-servers-in-the-dmz/
The easiest methods users opt to use are a push notification from the Microsoft Authenticator app, phone call, or text message. But what happens when the user’s phone is in Airplane mode but they still have WiFi for their laptop and want to authenticate against the NetScaler Gateway so they can get some work done?
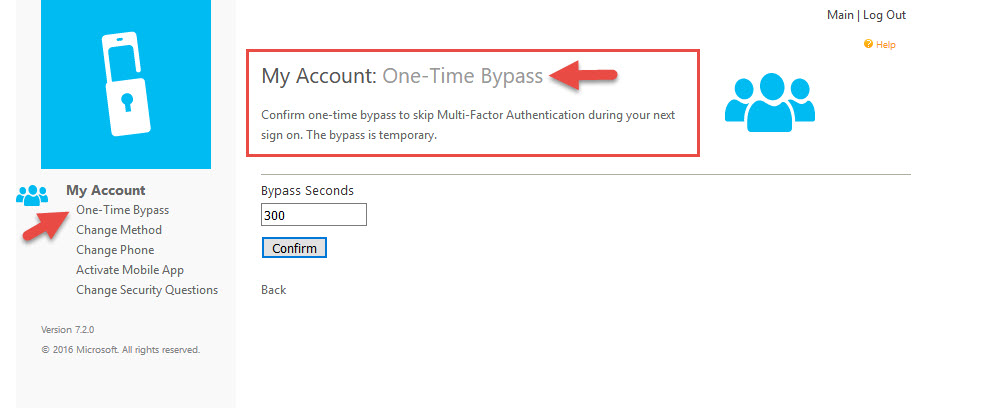
This is a scenario many people face when flying. They purchase WiFi access for their laptop from the airline but their phone is still in Airplane mode. In order to use WiFi for the phone they would have to purchase WiFi access for that as well which most people don’t typically do. So when the push notification, phone call, or text message are attempted, they don’t reach the phone. The user can navigate to the Azure User Portal and initiate an OTB (One-Time Bypass) prior to their flight but in my experience most organizations choose to turn this feature off as they consider it a security risk to allow users the ability to do this. In some orgs I’ve seen them give this ability to users that travel a lot (typically executives) or allow the Help Desk to initiate an OTB so they can bypass a user that calls in once they verify their identity and their situation:
And easier option in this scenario with the least amount of risk in my opinion is to enable OATH tokens for the Authenticator app. Normally when a user enrolls a mobile phone to allow for push notifications, they scan a QR code in the User Portal and then the account appears in the Authenticator app like this:
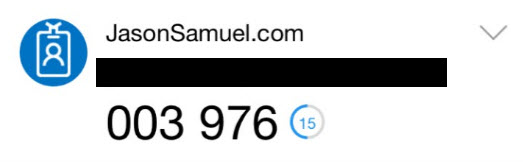
When you enable OATH tokens, when the user scans the QR code the account will appear like this:
This gives the user a 6 digit code that refreshes every 30 seconds. It is essentially a soft token (OTP or TOTP aka time-based one-time password) that the user can use when in offline mode, such as the flying scenario I described above.
Enabling OATH tokens doesn’t mean already enrolled users will automatically be able to use it. For those users, you would need them to go back into the MFA User Portal and scan the new barcode which drops the token into Authenticator for them. For already existing MFA deployments, I tell admins you can enable this but don’t necessarily have to get all users using it. Just the ones that travel and have a need to use Azure MFA in offline mode (typically executives).
Here are the steps to enable OATH tokens for Azure MFA:
1. Open up your MFA console and navigate to the Mobile App section. Check the Enable OATH tokens check box:
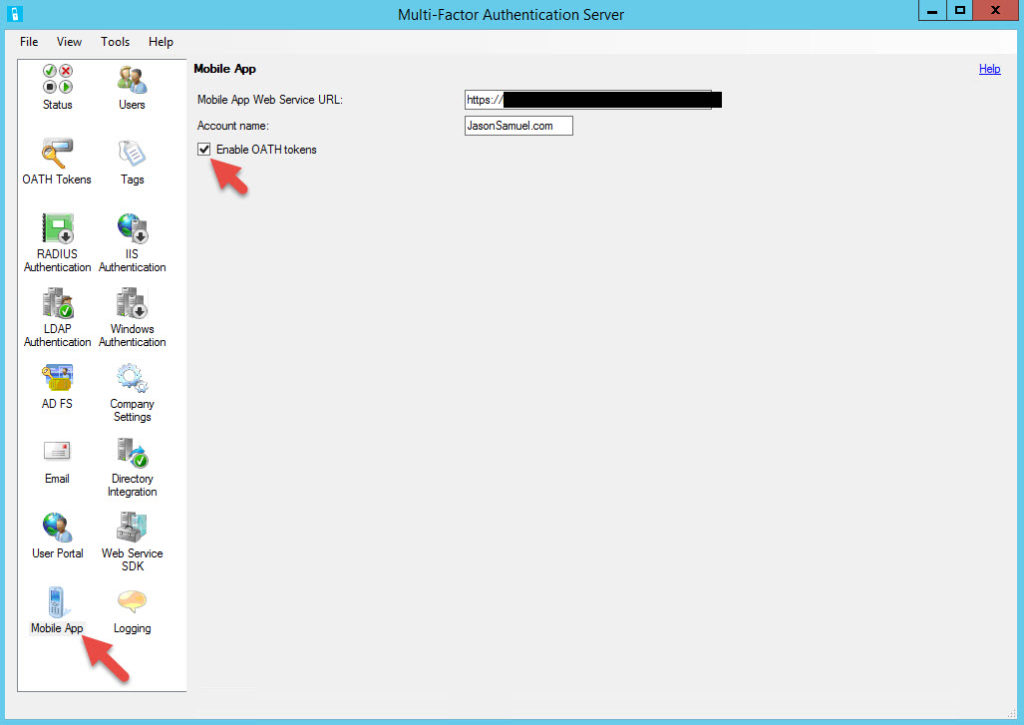
2. Go to the User Portal section and Allow users to select OATH tokens and use OATH tokens for fallback:
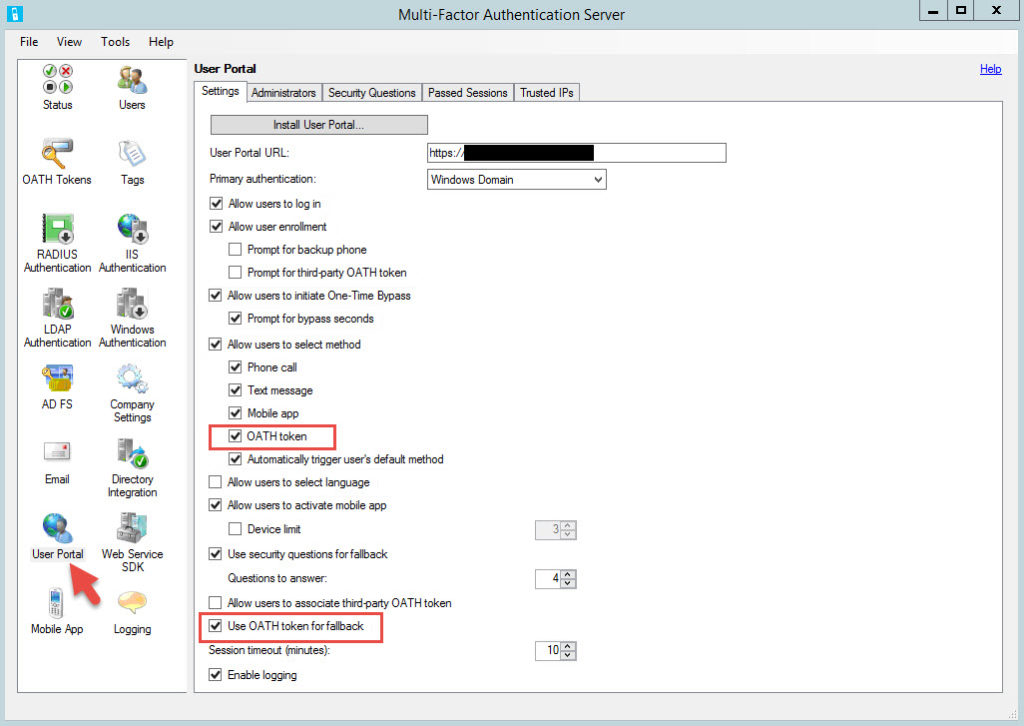
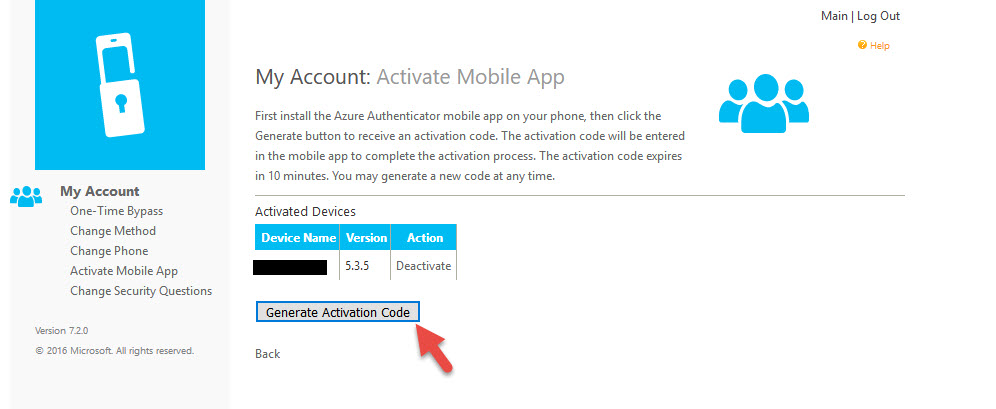
3. Now have the user login to the User Portal. If this is their first time setting up the mobile app it’s just the normal process. If they are already enrolled they will see their existing device here. There is no need to Deactivate it first. Just have them click Generate Activation Code.
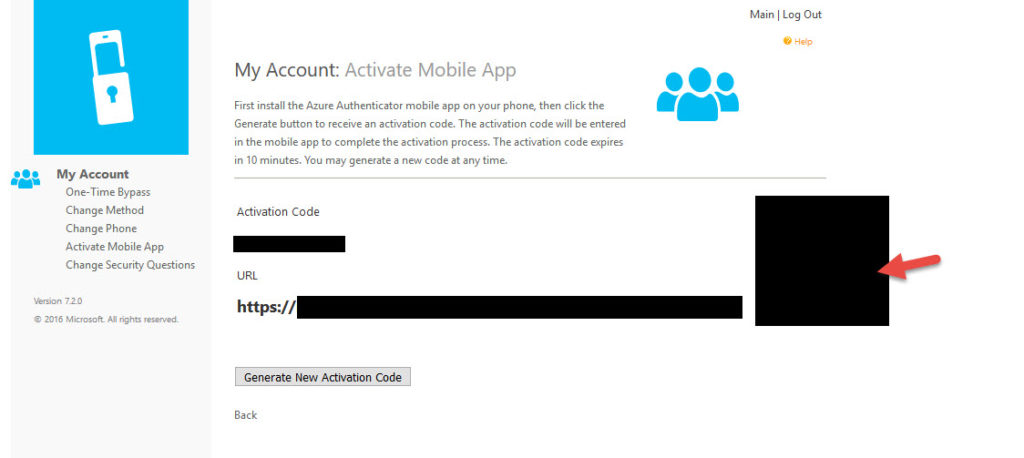
4. Now they will be asked to scan the QR code. Scan it.
5. It will update the existing account in their Authenticator app with the countdown code like this:
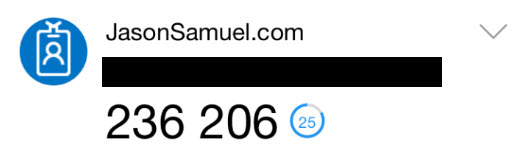
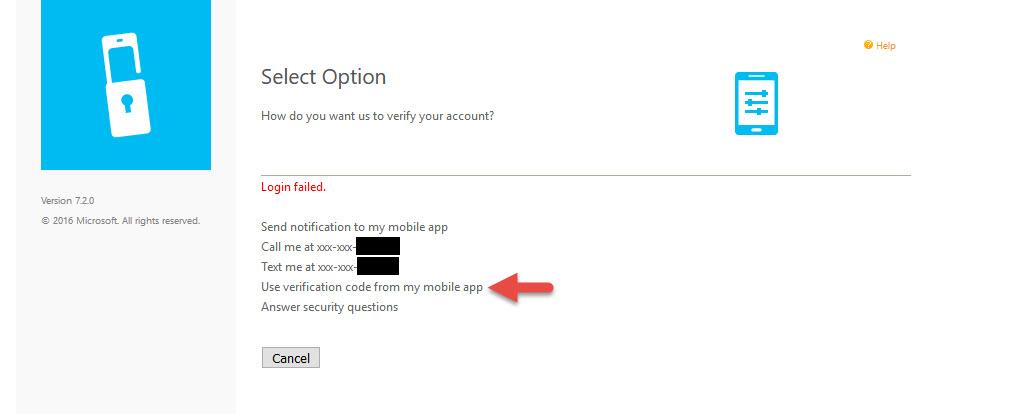
6. The user is good to go at this point. For testing, you can use the Azure MFA User Portal itself. Attempt to login and when you get the push notification, let it time out. After 55 seconds, you will get this prompt saying the login failed and asking you to choose a different way to authenticate:
Login failed.
Send notification to my mobile app
Call me at xxx-xxx-xxxx
Text me at xxx-xxx-xxxx
Use verification code from my mobile app
Answer security questions
Click the “Use verification code from my mobile app” option.
7. Now you can enter your code here and it should log you right in.
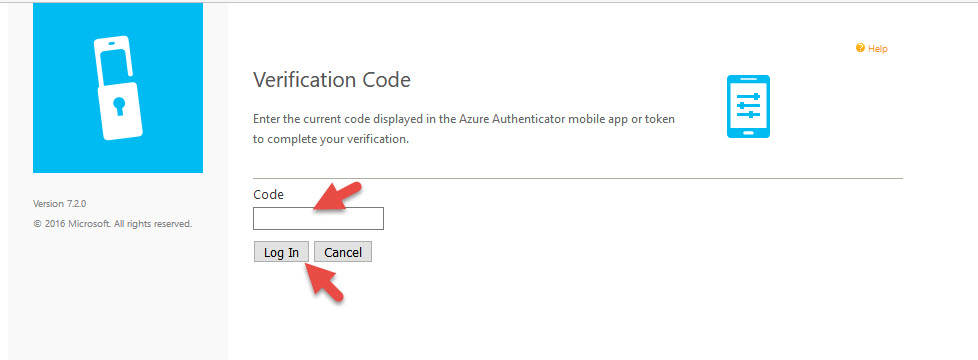
With this setup, the default method will be a push notification from the app. As a fallback, the user can use the code to enter once the initial authentication request has timed out. The default time out for the 2nd factor is 55 seconds now. In the past when I have tested this it was 2 minutes (120 seconds) so I suspect Microsoft has changed this recently due to user requests to lower it. 2 minutes is pretty high for a factor to time out, users don’t have the patience for that. This time out value is from the MFA cloud service and is set in the cloud control plane in Azure. It is not a setting you control or can change yourself. You have to call Microsoft Support and ask them to change the value if you need something less than 55 seconds.
Now keep in mind, this is not going to work when using NetScaler Gateway/Unified Gateway with LDAP or LDAPS and Azure MFA. You must use RADIUS. There is no mechanism for the Azure MFA server to talk back to the NetScaler and prompt a different form of authentication when using LDAP or LDAPS so the user will get an “Incorrect user name or password” message when the 2nd factor times out:
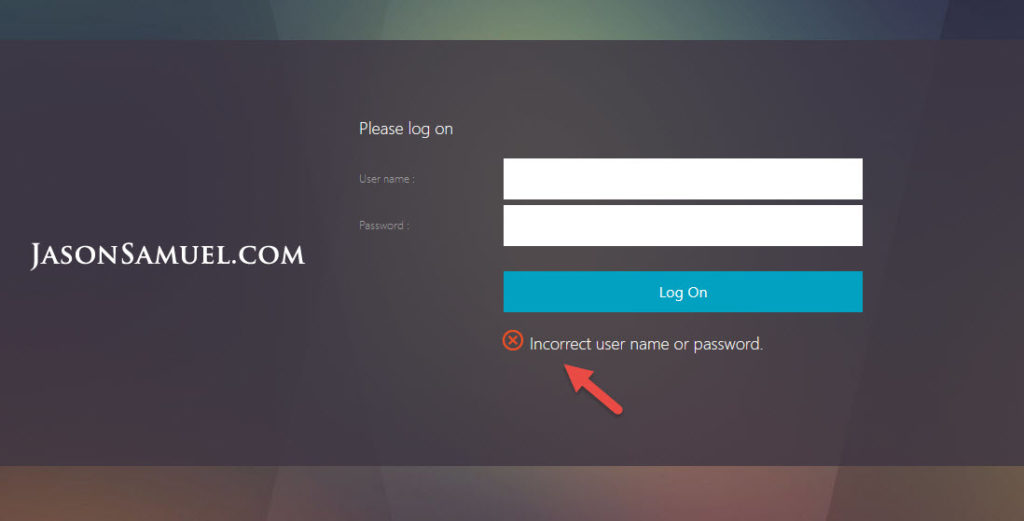
and your AAA debug will show Multi-Factor Authentication has failed:
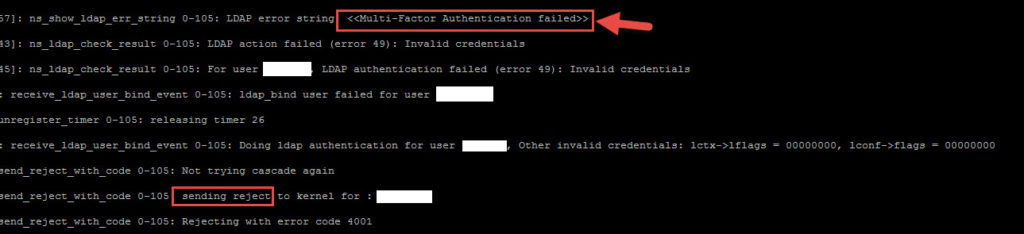
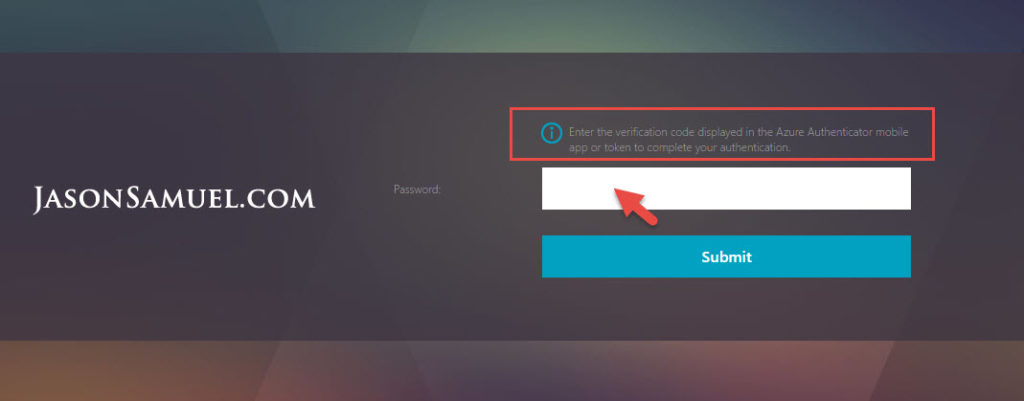
8. To get around this limitation, make sure you are using a RADIUS policy on your NetScaler. Then go to the Azure MFA console and check “Enable fallback OATH token”:
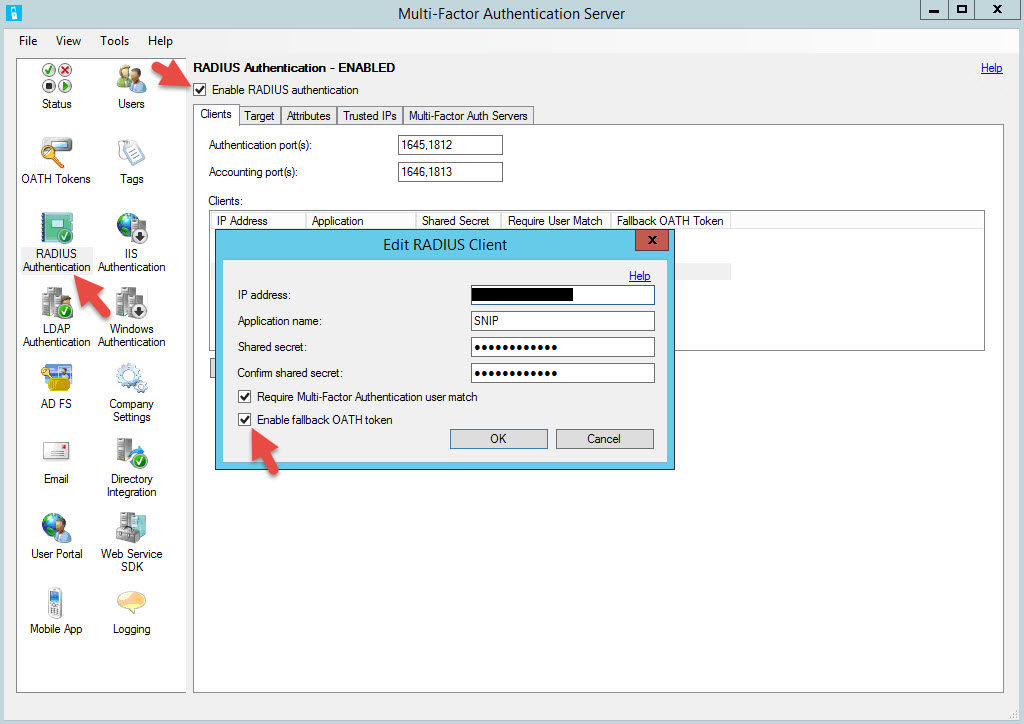
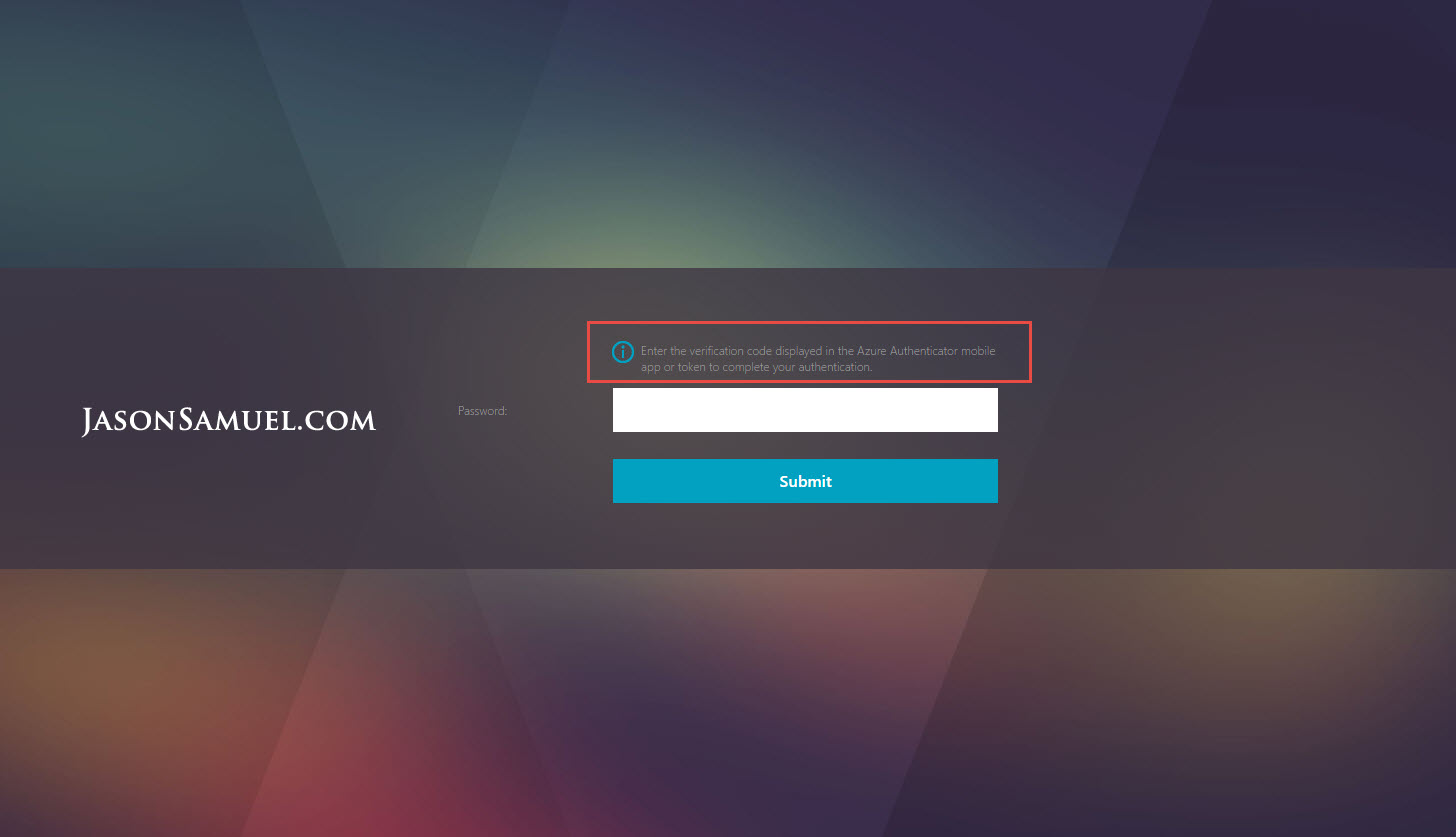
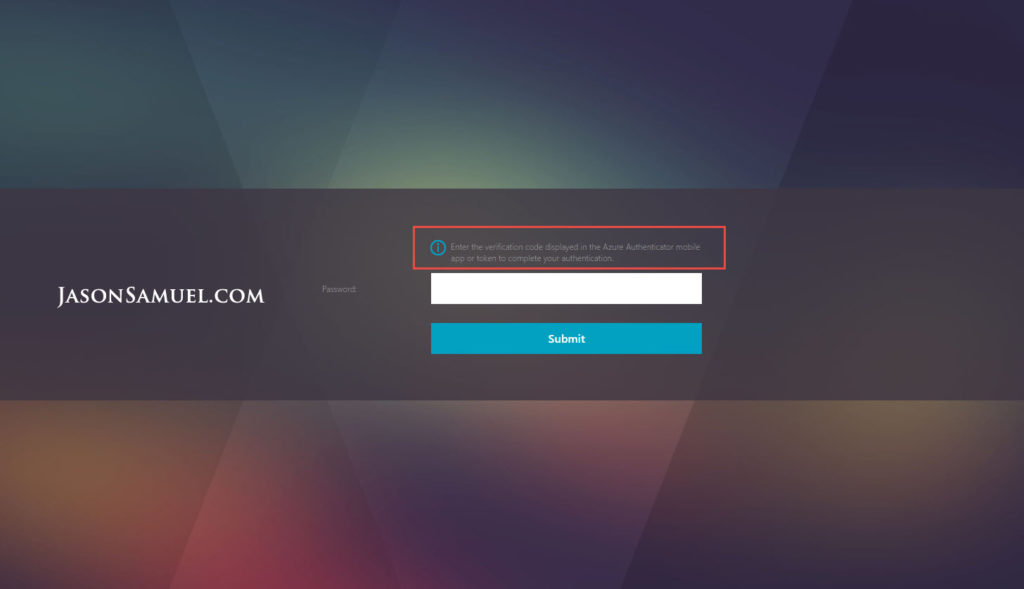
9. Also make sure your RADIUS policy NetScaler timeout is set much higher than 55 seconds. You don’t want your NetScaler timing out before the first authentication request times and and the user has the opportunity to enter the second authentication request. You should get a message saying:
Enter the verification code displayed in the Azure Authenticator mobile app or token to complete your authentication.
10. Alternatively, you must use AD FS and a SAML policy to take advantage of this feature. Take a look at my guide on this, I feel like it’s a much better user experience, especially when using Azure MFA:
Using AD FS 4.0, Server 2016, Azure MFA, Citrix FAS, Single FQDN, & Single Sign On with Citrix NetScaler Unified Gateway
http://www.jasonsamuel.com/2017/05/01/using-ad-fs-4-0-server-2016-azure-mfa-citrix-fas-single-fqdn-single-sign-on-with-citrix-netscaler-unified-gateway/
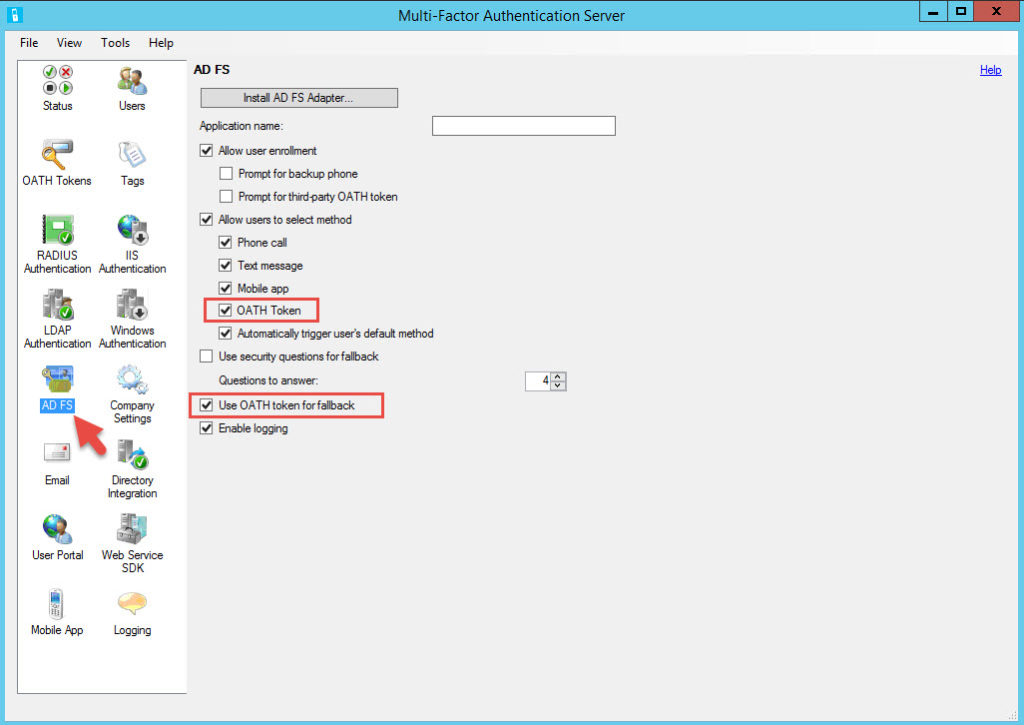
If you use AD FS make sure you enable OATH tokens and allow the use of OATH token for fallback on the AD FS Adapter settings in the MFA console. You’ll notice that the AD FS settings also allow for user enrollment. You can do almost anything you need within AD FS, without even needing to deploy the User Portal. Just something to consider for simple Azure MFA deployments. Once that change is done you will get the ability to use the verification code:
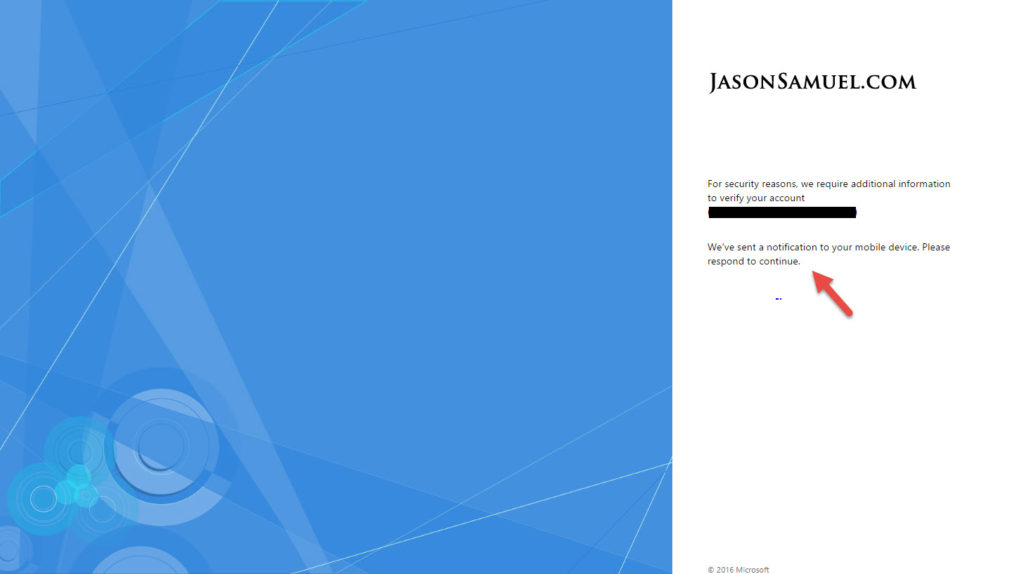
11. You can test now against your NetScaler Gateway/Unified Gateway. It should redirect you to the AD FS login page. Let AD FS time out:
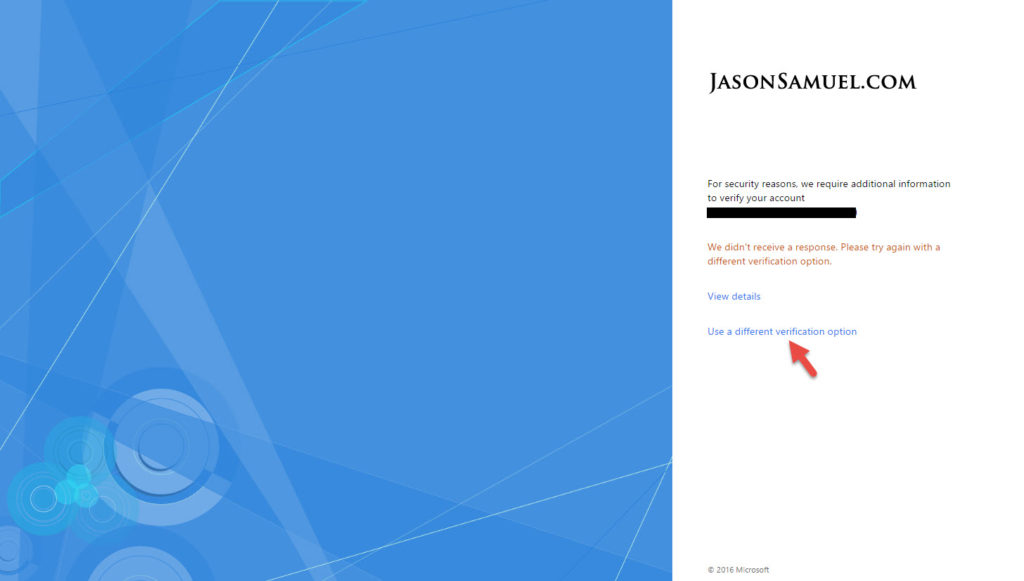
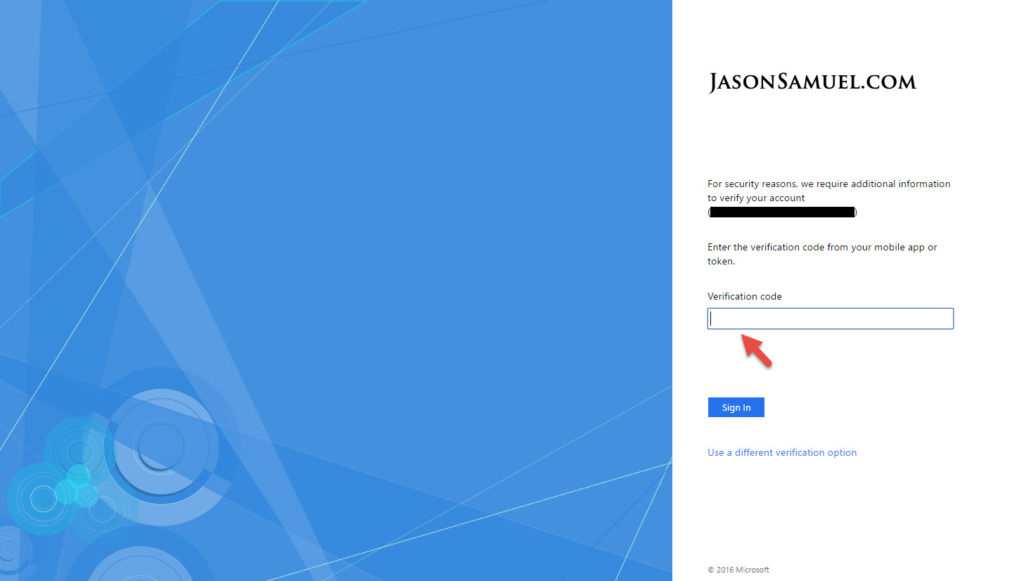
12. Choose “Use a different verification option”:
13. Choose “Use verification code from my mobile app”:

So to reiterate, you must use RADIUS or SAML (AD FS) with your NetScaler Gateway/Unified Gateway to be able to use OATH tokens for fallback and I’ve proven both methods out above. The timeout from the MFA service has decreased to 55 seconds now but if you want it even lower, contact Microsoft Support. I hope this helps your users that travel often or have spotty phone coverage. Please leave a comment below if you have any questions.



Shantanu Padhye
February 7, 2018 at 11:50 AM
Awesome article sir.
Do you provide lab access by any chance or tips on how to set up your home lab
Jeff Brixhamite
January 15, 2020 at 10:03 AM
Great article, do you have any preference between using google authenticator and microsoft authenticator ?