Why haven’t you gone passwordless yet? I stopped using passwords with my virtual desktop environments, physical machines, Microsoft 365 (Office 365), and anything protected with Azure AD for what feels like ages ago now. Going passwordless means strong authentication into the services you use daily. I use a biometric to login every day, and you can too with either your thumbprint or face much like you may already do on your iPhone or Android phone. I’ve covered passwordless authentication for your enterprise work life and your personal life in multiple articles and events before. You can accomplish this with virtual desktops and web-based services using FIDO2 security keys or Microsoft Authenticator passwordless phone sign-in. And now there’s a 3rd option which is the focus of this article. 🙂
With the Microsoft Windows 10 version 2004 build, Microsoft has extended the passwordless capability of Windows Hello and Windows Hello for Business to web browsers! This also means Windows native applications that are protected with Azure AD and open up a web view with Edge for authentication are also supported! Previously Windows Hello being a platform authenticator could only be used within the Windows OS itself. With this new capability, your laptop’s built-in fingerprint reader, built-in infrared webcam, or external USB webcam (Logitech Brio for example) can be used with your web browser just like external authenticators can. Basically, any peripheral that is supported with Windows Hello can be used with web browsers just like you use FIDO2 security keys today. Remember that Windows Hello for Business is a certified FIDO2 authenticator so fingerprint readers and IR cameras built into your laptop can be used for FIDO2 authentication just like physical FIDO2 security keys can.
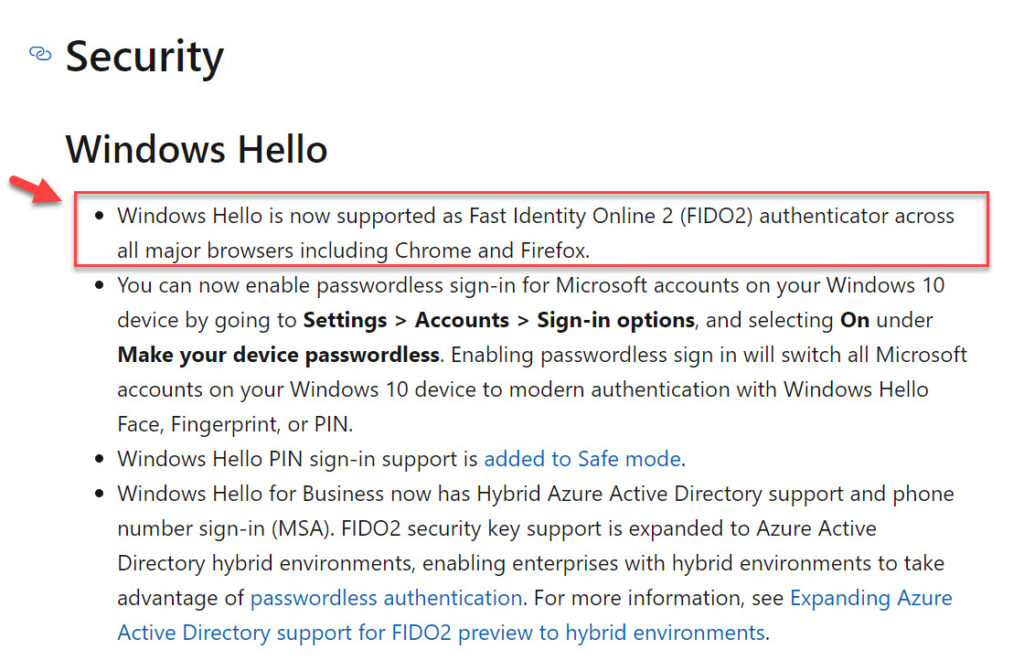
This is such an important feature for the industry and Microsoft knows it. This Windows Hello capability is the #1 feature listed for Windows 10 version 2004 in the release notes above everything else: https://docs.microsoft.com/en-us/windows/whats-new/whats-new-windows-10-version-2004
- Windows Hello is now supported as Fast Identity Online 2 (FIDO2) authenticator across all major browsers including Chrome and Firefox.
- You can now enable passwordless sign-in for Microsoft accounts on your Windows 10 device by going to Settings > Accounts > Sign-in options, and selecting On under Make your device passwordless. Enabling passwordless sign in will switch all Microsoft accounts on your Windows 10 device to modern authentication with Windows Hello Face, Fingerprint, or PIN.
- Windows Hello PIN sign-in support is added to Safe mode.
- Windows Hello for Business now has Hybrid Azure Active Directory support and phone number sign-in (MSA). FIDO2 security key support is expanded to Azure Active Directory hybrid environments, enabling enterprises with hybrid environments to take advantage of passwordless authentication. For more information, see Expanding Azure Active Directory support for FIDO2 preview to hybrid environments.
Want to enable it?
- Update your laptop or desktop to Windows 10 2004 (aka May 2020 Update): https://support.microsoft.com/en-us/help/4028685/windows-10-get-the-update
- Protect your SaaS apps and virtual desktops using Microsoft Azure AD as the identity provider. Don’t worry, even the Azure AD FREE version can be used for this if you’re broke 🙂 : https://azure.microsoft.com/en-us/pricing/details/active-directory/
- Enroll your authentication methods. I’ve written many articles on these but to summarize:
- FIDO2 security keys on https://myaccount.microsoft.com for your company’s Azure AD
- FIDO2 security keys on any consumer website you use that supports FIDO2
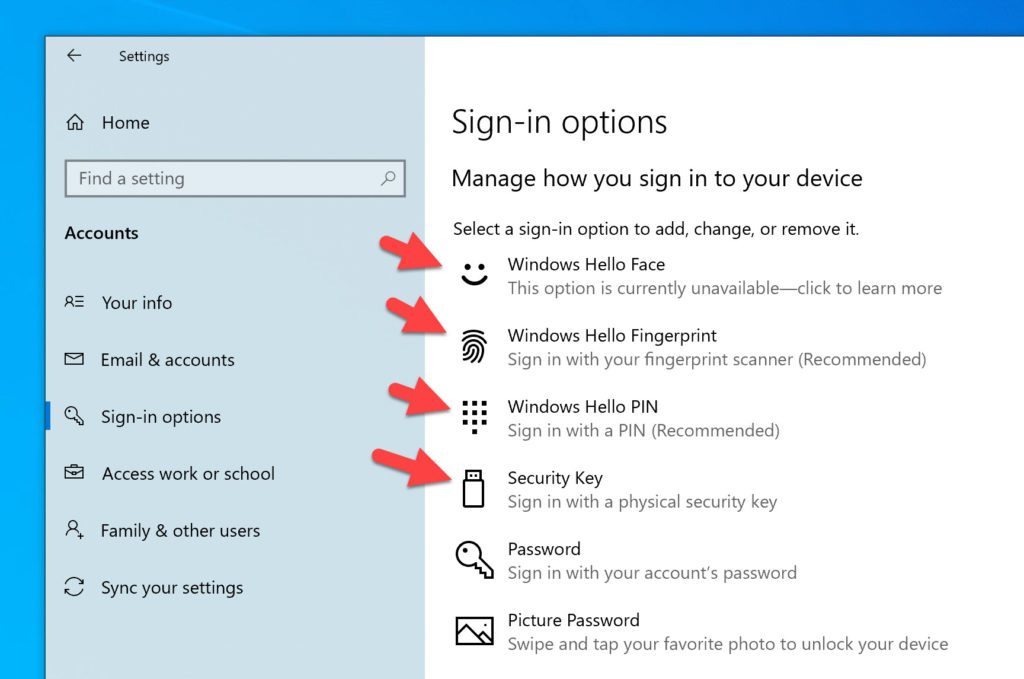
- Windows Hello for Business on your company laptop (Start > Windows Security > Account protection > Manage sign-in options)
- Windows Hello on your personal laptop (Start > Windows Security > Account protection > Manage sign-in options) ***Note this is a convenience PIN, fingerprint, face, and not the enterprise Windows Hello for Business which is truly passwordless and creates the device trust with Azure AD.
Azure AD will prompt sign-in options differently depending on your device’s capabilities
Azure AD will prompt you to sign-in differently depending on your device’s capabilities. This is something that I often have to explain to people starting out with passwordless because their screens don’t always match my screenshots in many of my articles precisely.
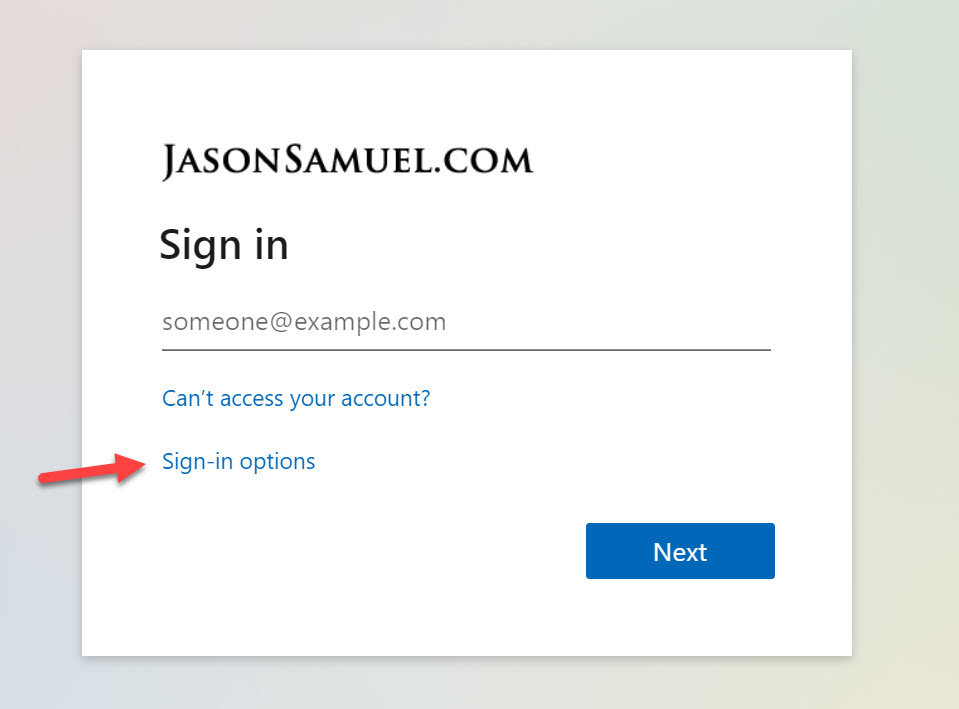
First, you go to any website protected by Azure AD and you’ll see the usual password option first. Passwordless is buried behind the “Sign-in options” link at the moment but I do hope to see it brought front and center matching the Windows 10 login screen. I do expect we will see passwordless become more visible front and center with time, but for now, click “Sign-in options”:
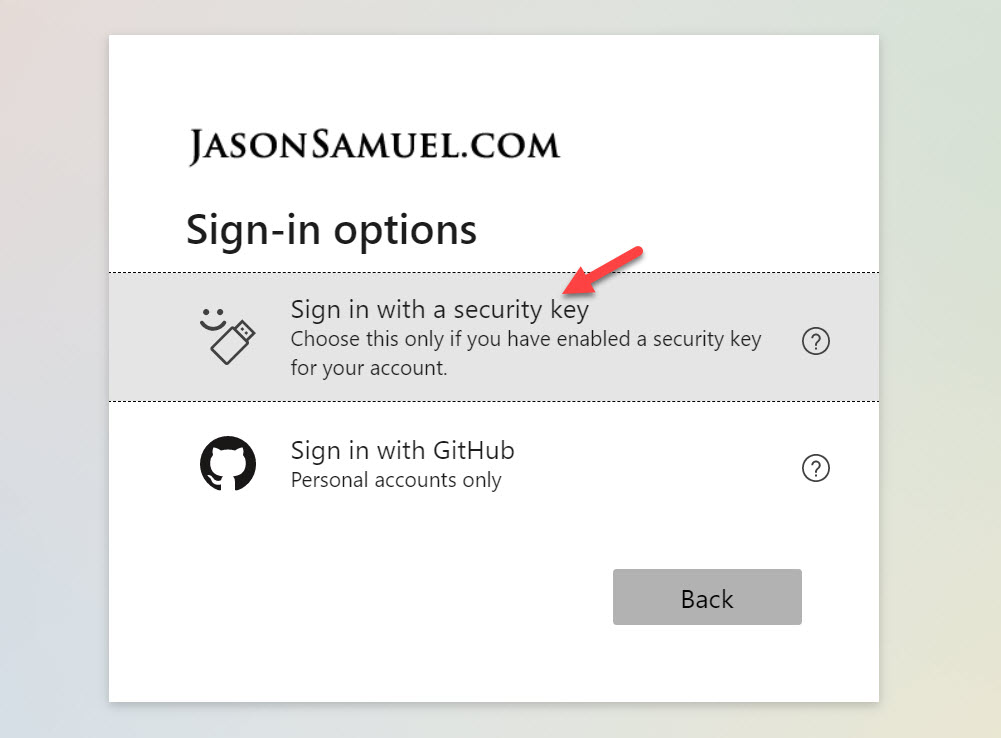
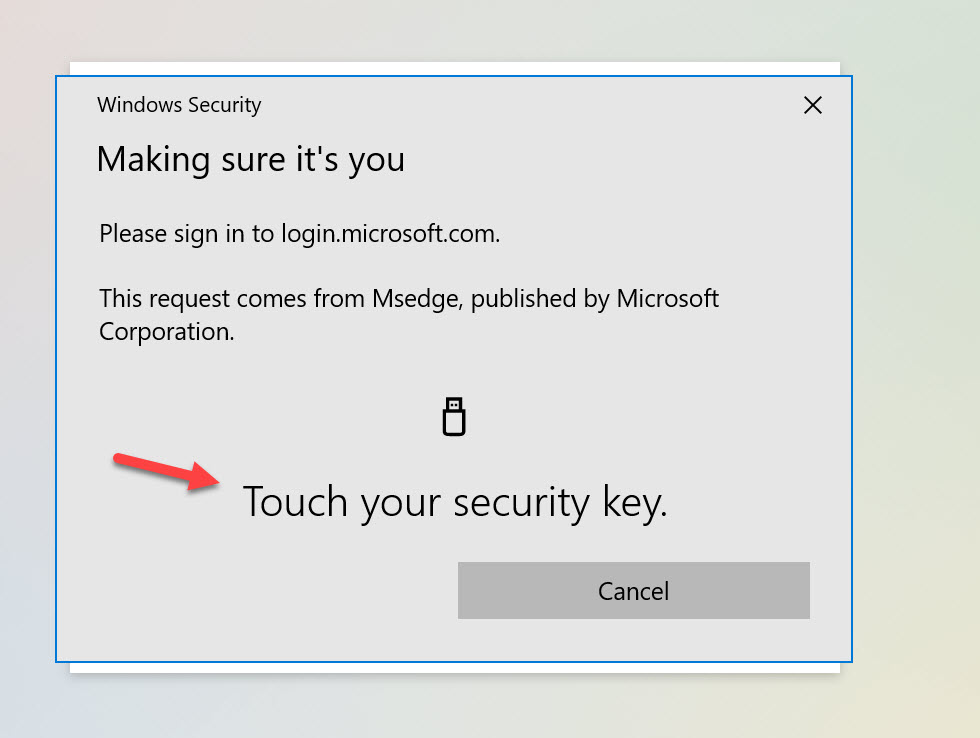
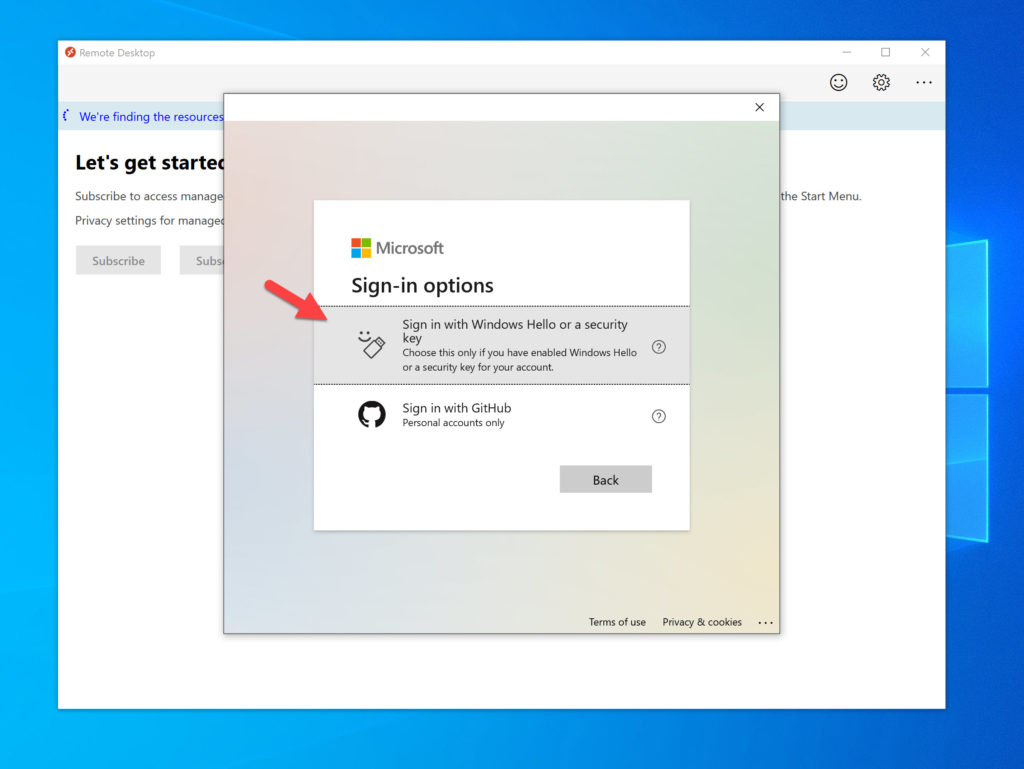
When on an unmanaged Windows 10 desktop with no Windows Hello or FIDO2 key, the prompt will look like this asking you to “Sign in with a security key”. It knows the machine doesn’t have any Windows Hello capability so your FIDO2 key is the only option:
At this point, if you plug-in a USB FIDO2 key and click to proceed, you will see this prompt:
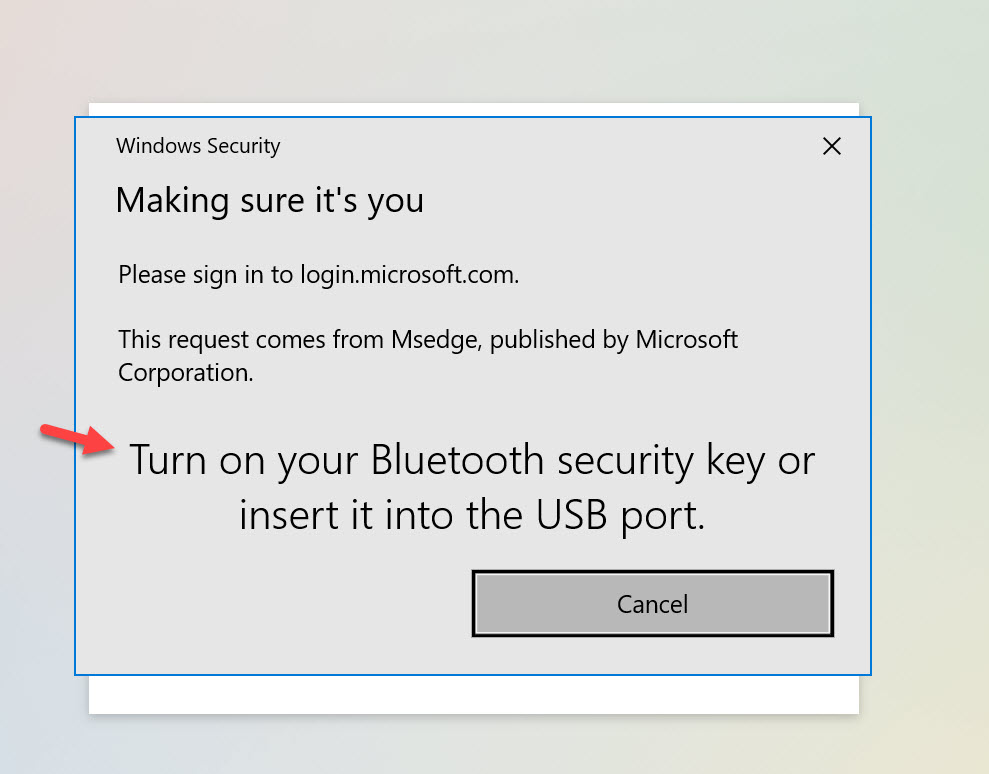
If you have paired a BLE (Bluetooth) FIDO2 security key with your computer, then the web browser will detect that capability and will prompt like this:
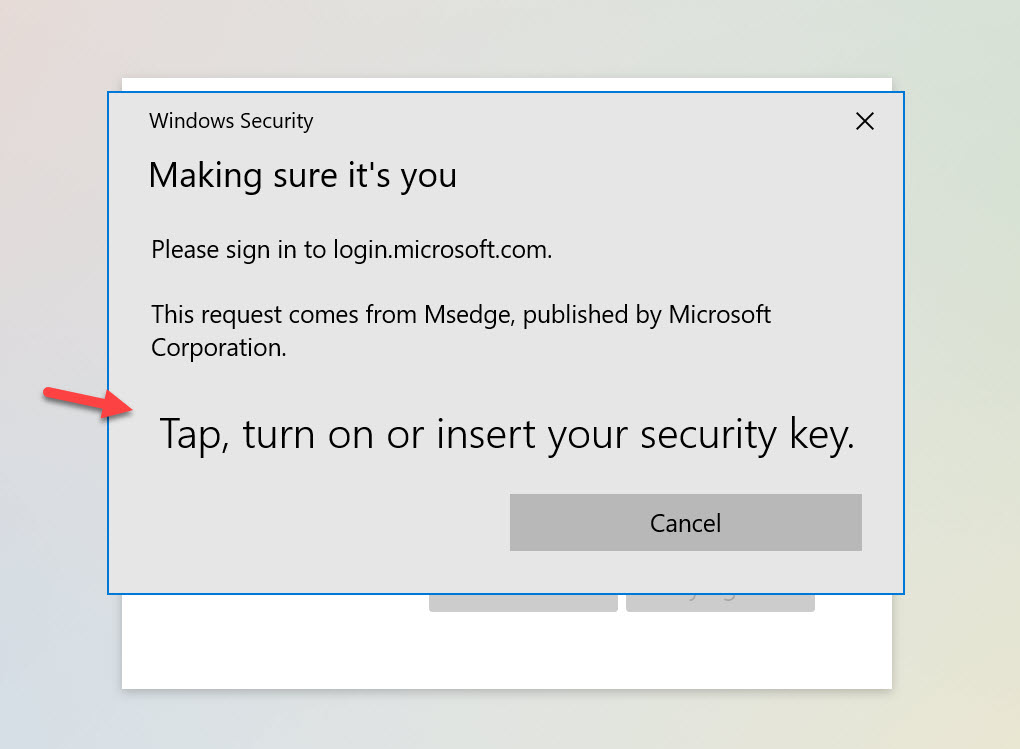
If you have an NFC FIDO2 card like the HID C2300 and have an NFC USB reader like the HID OmniKey contactless reader plugged in, then you will see this prompt to tap the card on the card reader:
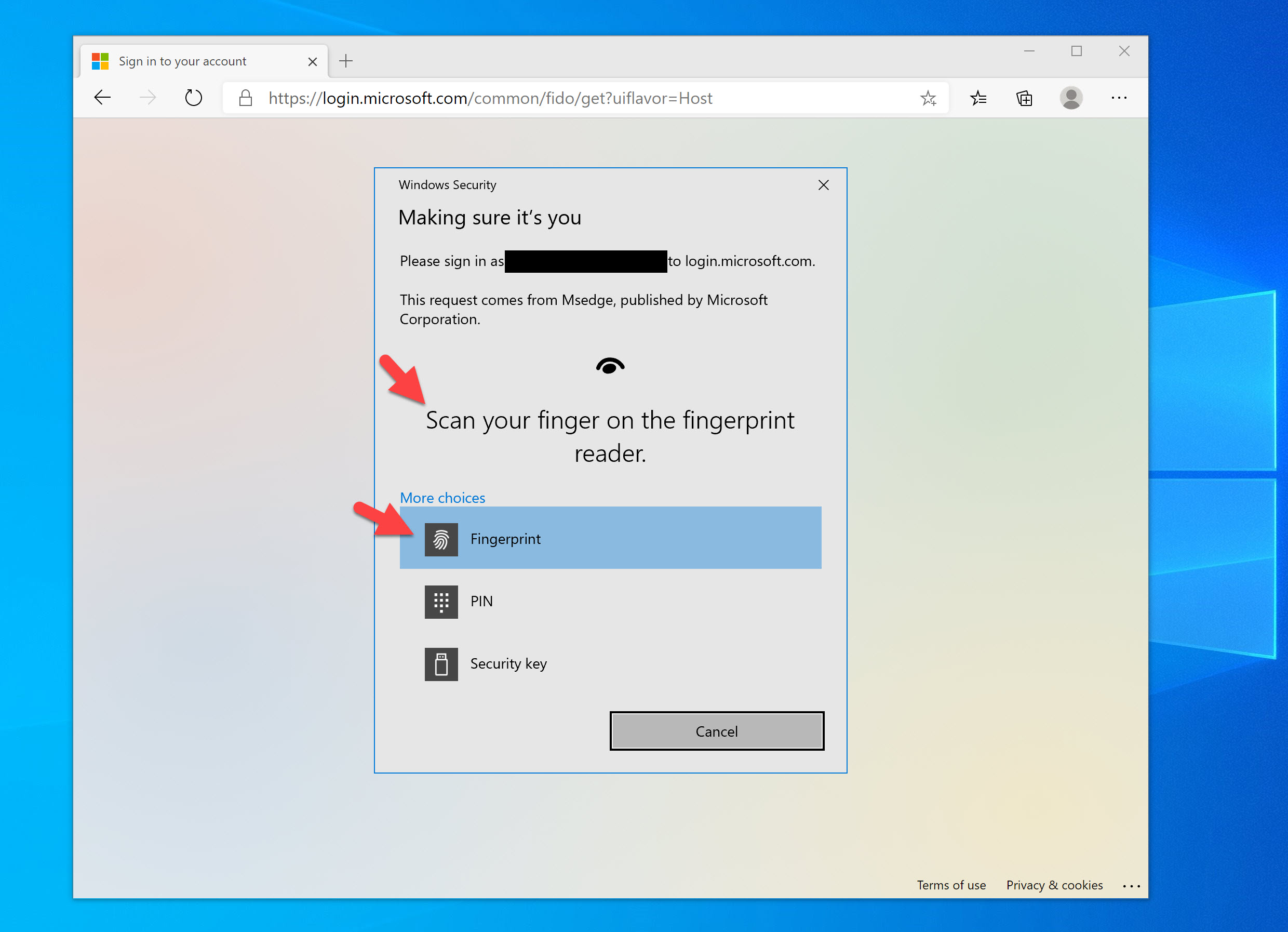
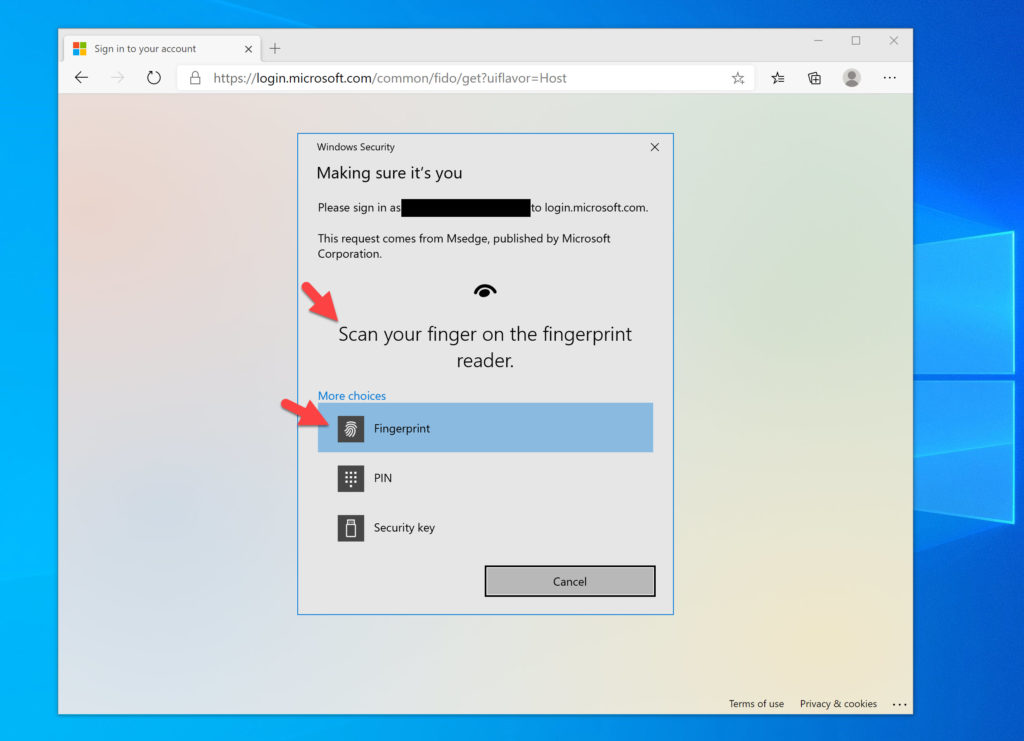
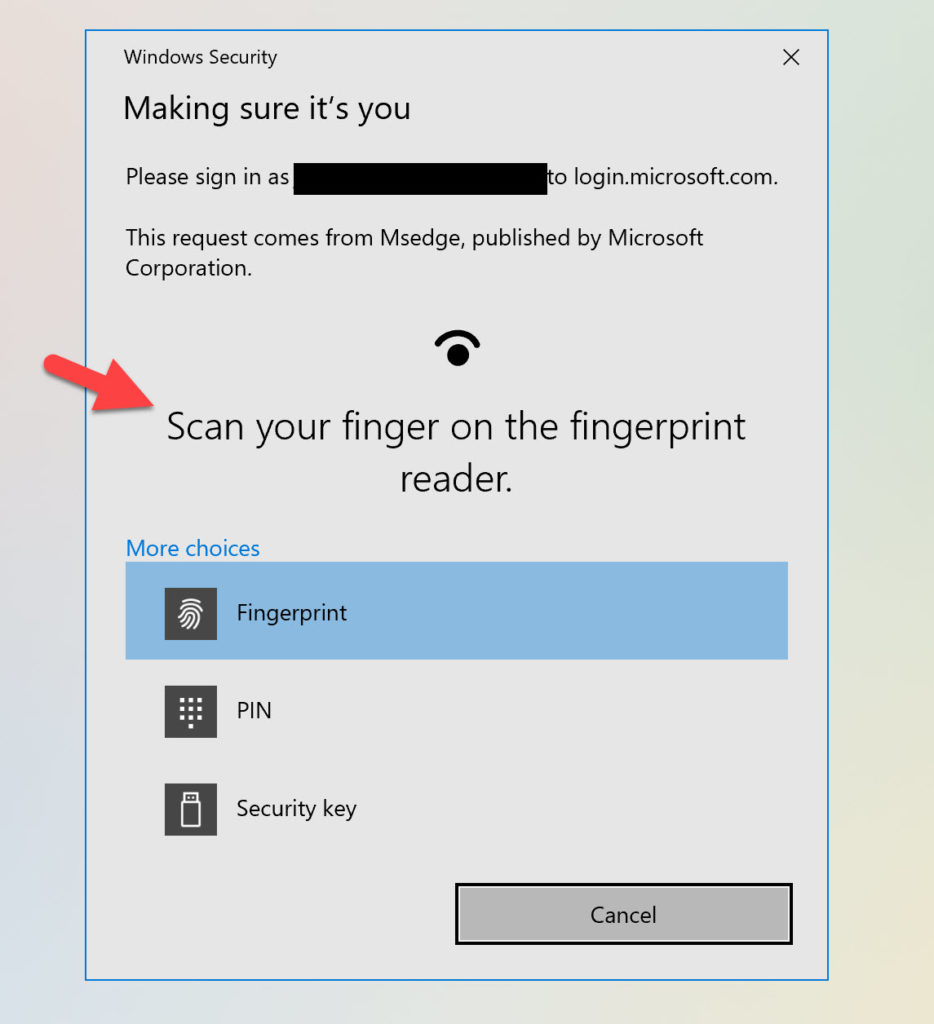
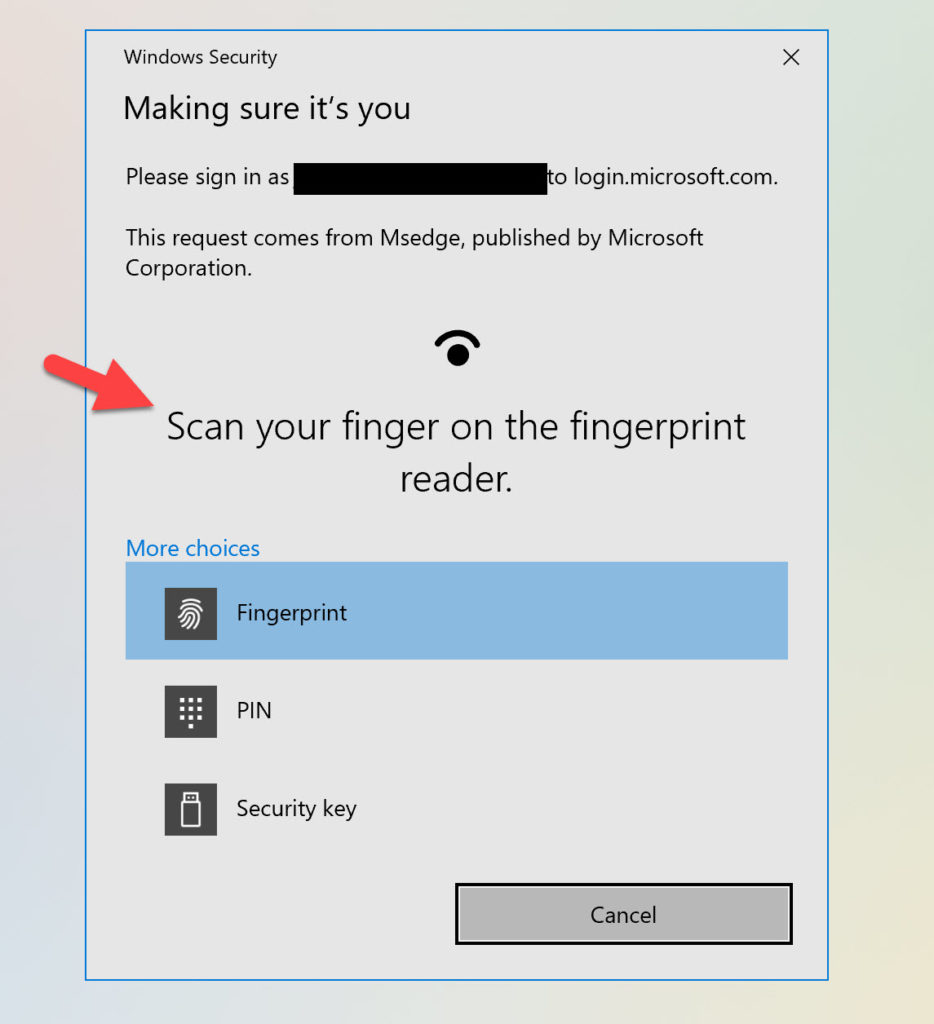
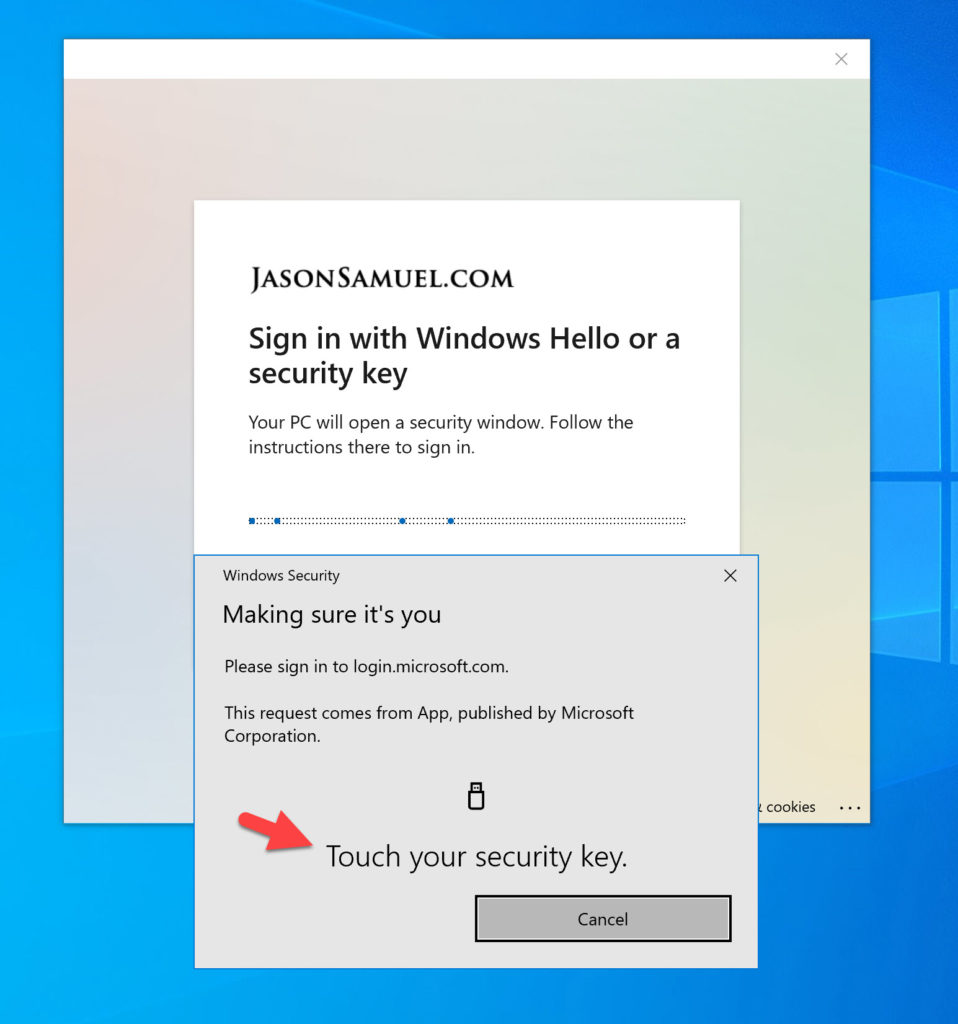
Drumroll, now if we go to our Windows Hello capable laptop and try this, you will see Windows Hello available as an option through a web browser! Here is my fingerprint reader on my laptop showing up as an authentication option as well as the Windows Hello PIN option below it:
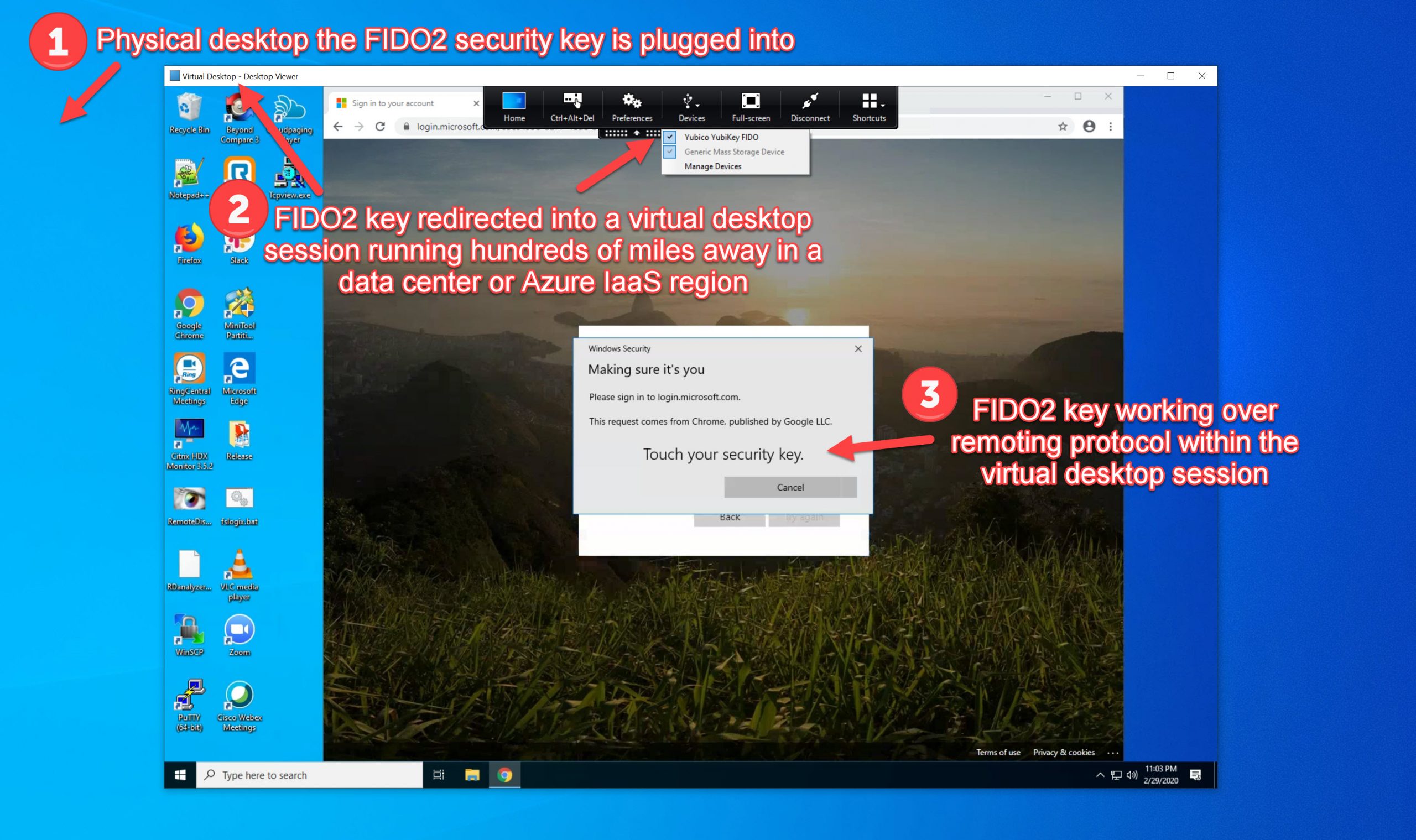
How Windows Hello and FIDO2 capability works with the Microsoft Windows Virtual Desktop (WVD) client
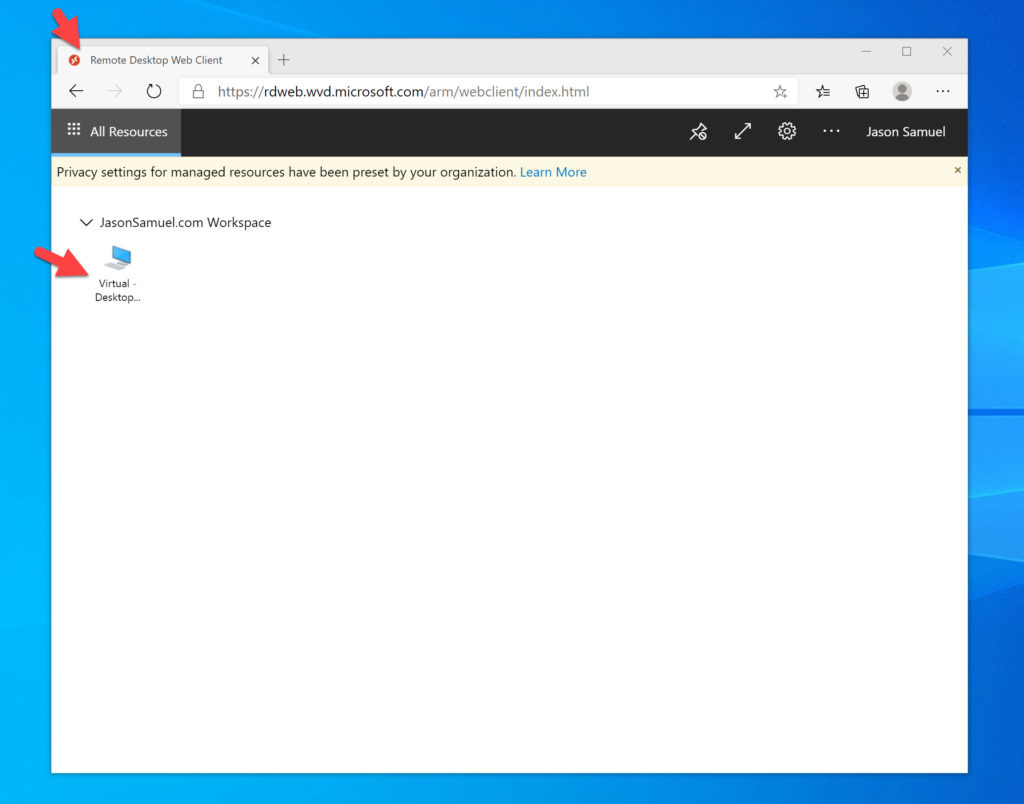
Using any modern web browser, you will get this experience when attempting to login at the WVD web client URL (https://rdweb.wvd.microsoft.com/arm/webclient). Look at that! I can use my laptop’s Windows Hello fingerprint reader or any of my FIDO2 security keys with WVD on this machine:
Once I scan my finger, I then see my WVD virtual desktops and RemoteApp virtual apps:
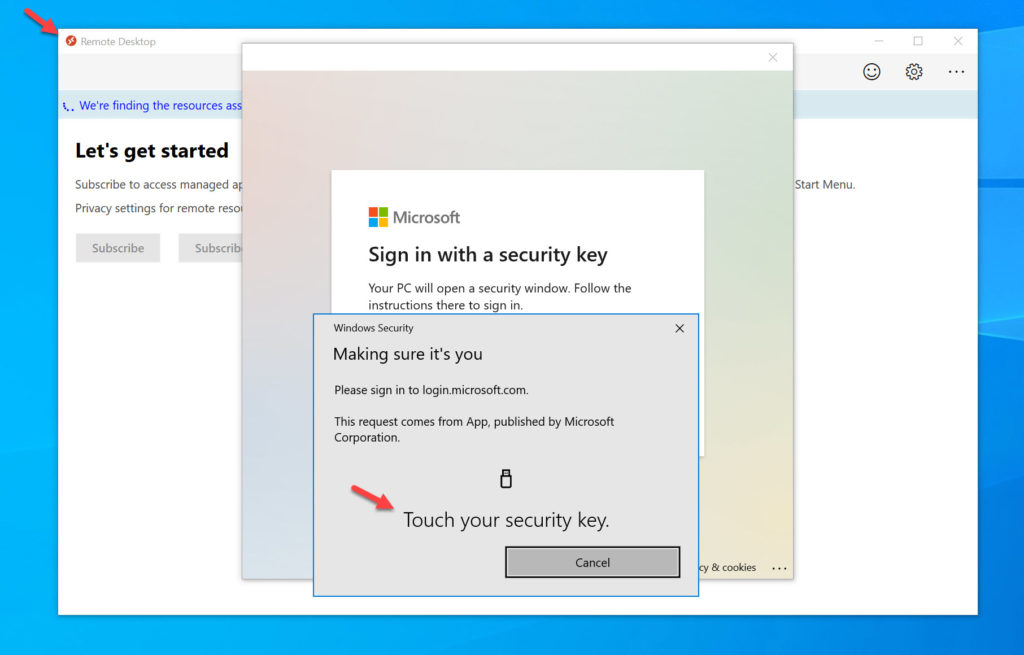
Here’s how it looks with the WVD Windows client on this same laptop. I’ve used this on WVD client version 1.2.1104 onward just fine and the option for both Windows Hello and FIDO2 come up like this:
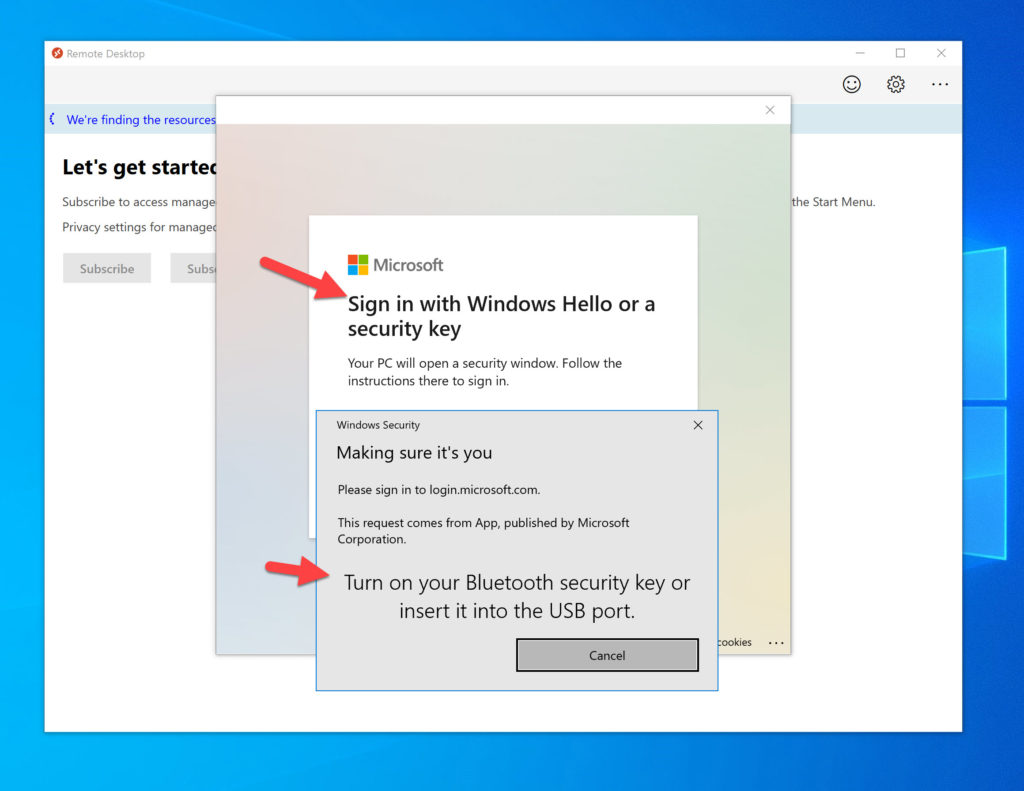
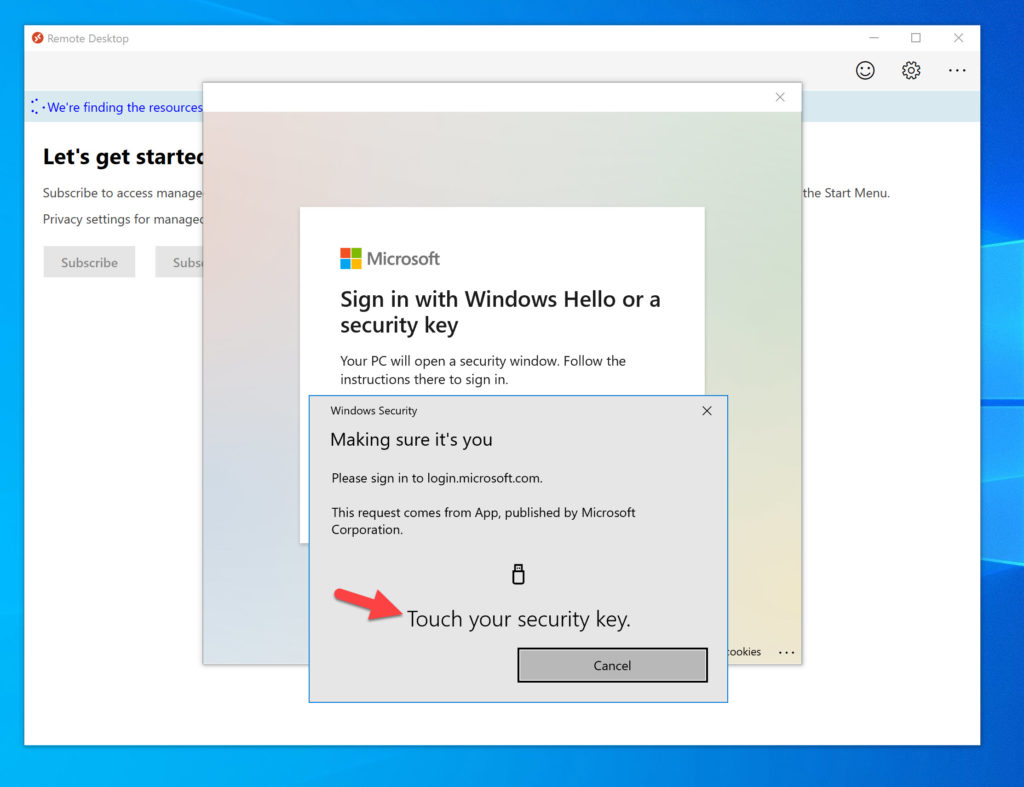
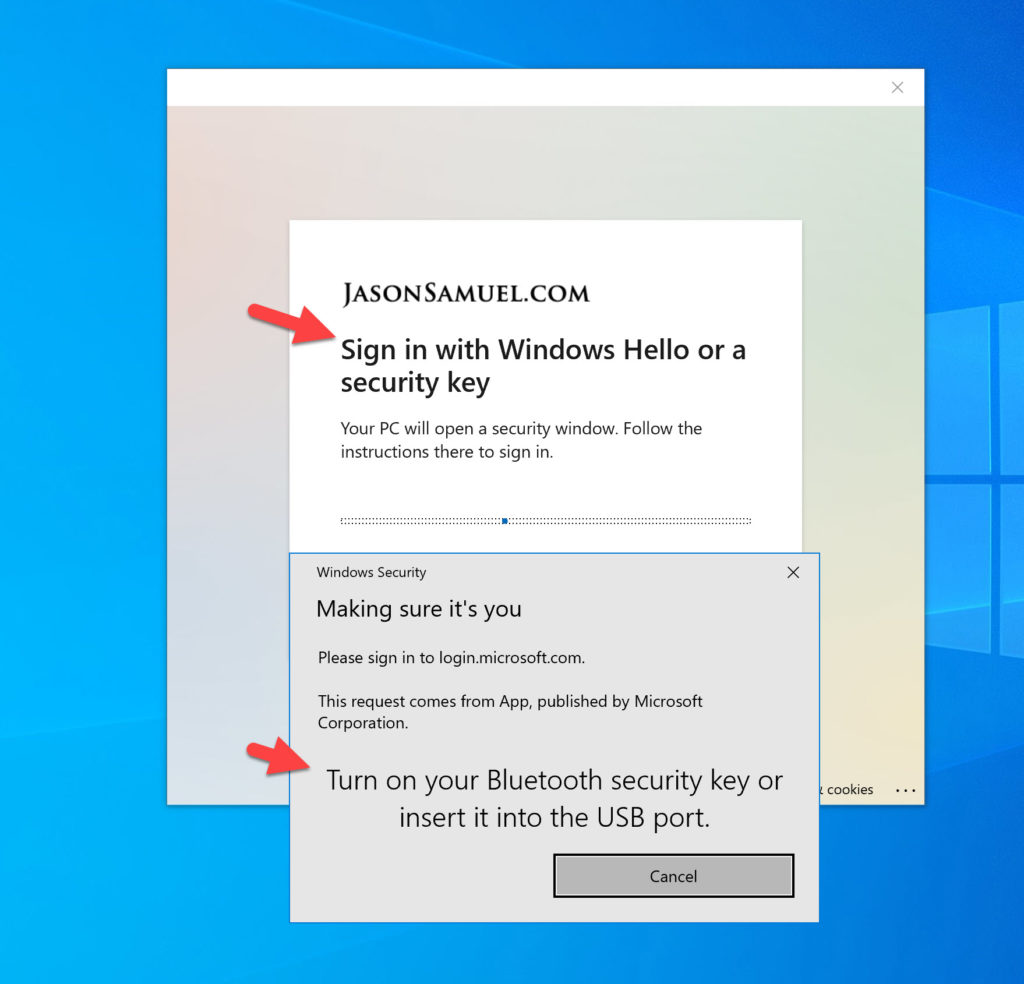
However, you must note that Windows Hello doesn’t actually prompt even though you’re using a web view. Only FIDO2 is supported at this time even with the most current WVD client in my testing. If you unplug your FIDO2 key and try to get a prompt from Windows Hello, you won’t. Instead it will tell you turn on your Bluetooth FIDO2 security key (if you’ve paired one in the past with your laptop as I have done) or ask to plugin your USB FIDO2 key:
As soon as you plugin your FIDO2 key, then you can use it as normal. Don’t worry, I think it’s just a matter of time before we get Windows Hello capability for the WVD Windows client as well:
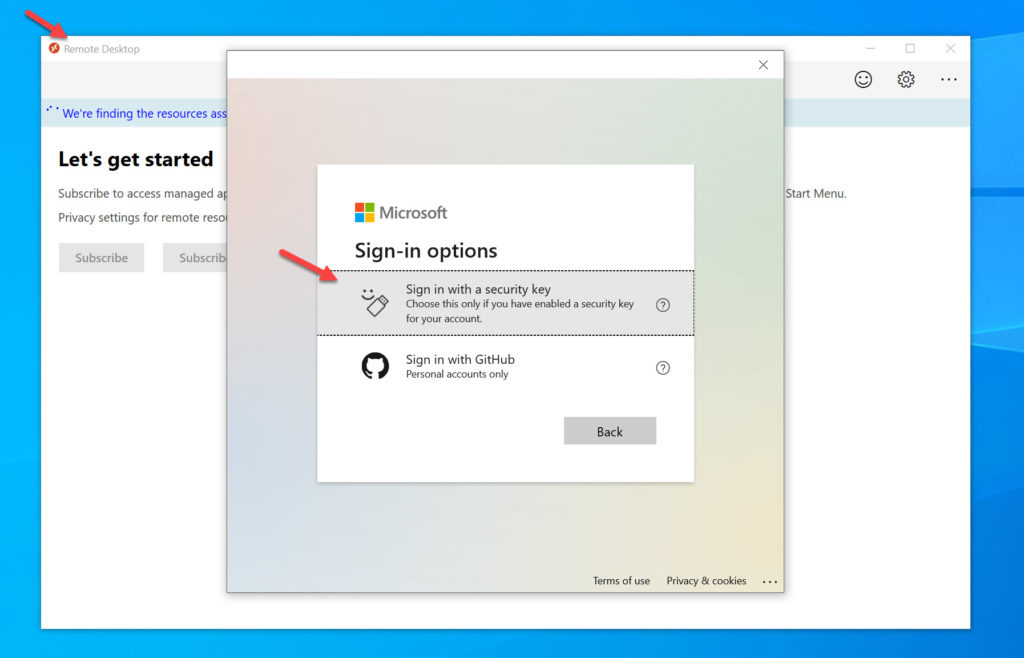
You may try this on your desktop and wonder why the Azure AD prompt doesn’t show the Windows Hello option and only references a security key. As I covered earlier, that’s because it knows what auth methods you have available to you and will change the screen dynamically based on the device you are coming from. On my desktop, I only have my FIDO2 key plugged in. So from Azure AD I only get the option to sign-in with my FIDO2 key and don’t see the Windows Hello part in this verbiage like my screenshots above:
And of course, from here I can use my FIDO2 key to login and complete the feed enumeration for my WVD virtual desktops and RemoteApps as you would expect:
If you are using a company laptop that is Hybrid Azure AD Joined and enrolled in Windows Hello for Business, you will also not be able to use Windows Hello to scan your fingerprint just yet. But you can definitely use your FIDO2 key no matter the type and upon completing auth, your WVD ARM (Spring Update) based virtual desktop is available for launch immediately.
How Windows Hello works with the Microsoft Teams client
If using the Teams web client, just navigate to https://www.office.com in your favorite web browser and begin the sign-in flow as I showed above and it will work fine with Windows Hello for Business or your FIDO2 key. Any Microsoft 365 (Office 365) service will work with both Windows Hello for Business and FIDO2 security key through a web browser since they are protected with Azure AD:
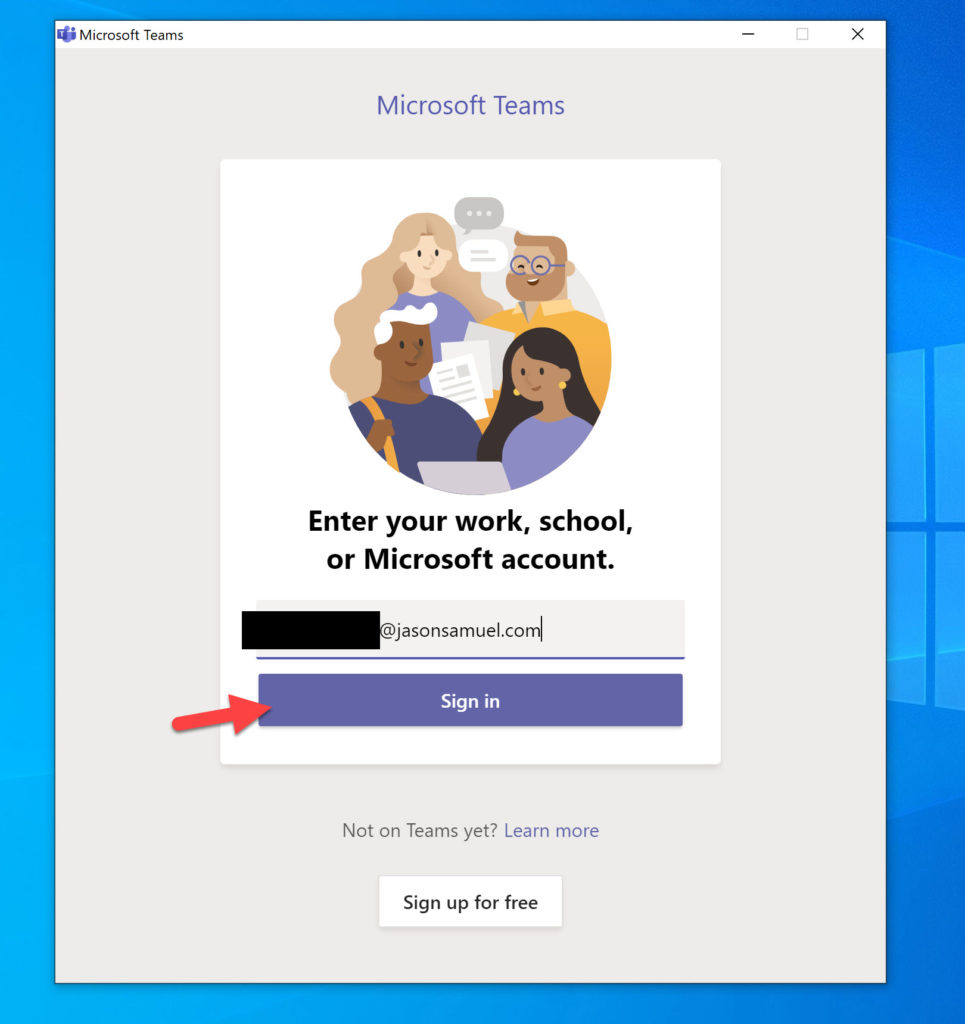
The Teams Windows client is a little different since the first screen you type in your email address is not the typical Azure AD-based web view. If you are on a BYO device or company device that is not HAADJ/no Azure AD PRT, you may likely see this screen and need enter your email address here:
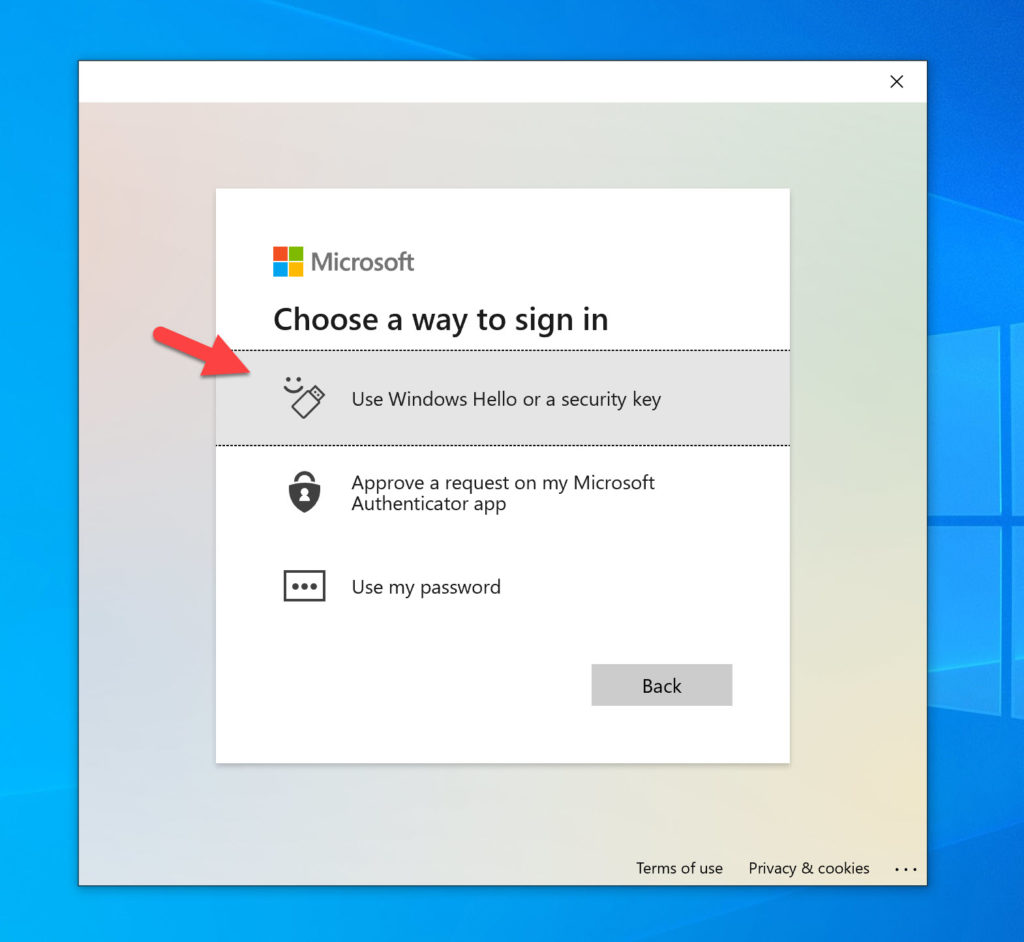
and then you’ll get the webview from Teams. Go ahead and use your FIDO2 key:
Just plugin your FIDO2 key even though it says you can use Windows Hello. It will not detect Windows Hello yet similar to the WVD client so your FIDO2 key is the only way to login for the moment through the native client. Since both WVD client and Teams client are behaving the same way, we likely just need a Windows 10 OS update to get Windows Hello to kick in for native Windows app web views at some point in the future:
Go ahead complete auth with your FIDO2 key:
then you will see Teams complete loading and you’ll be in ready to use it like this just like you saw earlier with Teams through a web browser:
How do you track if your users are using Windows Hello to sign-in?
Easy! With Azure Monitor Log Analytics. I wrote a guide on how to track your FIDO2 and Microsoft Authenticator passwordless phone sign-in here:
How to report on Microsoft Authenticator password-less phone sign-in & FIDO2 security key usage using Azure AD & Azure Monitor Log Analytics
Well, guess what? Windows Hello for Business is now in the Azure AD sign-in logs as well! Just add “WindowsHelloForBusiness” to my KQL query and they will all populate.
Final Thoughts
I hope this info helps you understand how monumental the Windows 10 2004 update really was for strong passwordless authentication capability for both the enterprise and personal services you may use. Extending Windows Hello to web browsers makes FIDO2 capability available to everyone with a Windows 10 device that can support it. Let me know how your experiences go!


sarosh
August 3, 2022 at 8:40 AM
Hi Jason, Thanks a ton for this great article!
I have a question on this specific section/verbiage of your article:
“Drumroll, now if we go to our Windows Hello capable laptop and try this, you will see Windows Hello available as an option through a web browser! Here is my fingerprint reader on my laptop showing up as an authentication option as well as the Windows Hello PIN option below it”
When you say “Windows Hello capable laptop” what kind of device are you referring to here? A personal device that has no registration whatsoever to Azure AD/HDAAJ/on-prem AD OR a laptop device owned by Enterprise (registered/joined to on-prem and/or Azure AD.
Appreciate if you could clarify please.