Let’s buy more licenses for VPN!
Let’s open up RDP port 3389 from anywhere to office PCs!
Let’s turn off multi-factor authentication so we don’t have to train users that may have difficulty with it!
EUC and Security-focused IT professionals know these are usually very poor choices for IT organizations. Yet these are some of the panicked thoughts that may cross your mind in this time of crisis.
Make positive decisions in a time of crisis

Easier said than done, I know. What’s happening in the world right now is unprecedented. The situation with COVID-19 Coronavirus pandemic is fluid and changing daily. It’s okay to panic. It’s okay to make mistakes. It’s okay to be human.
Uncertain times and WFH (work from home) business pressure can lead to rash decisions that do more harm long term than good, however. I’ve talked to a lot of enterprises in recent weeks and have seen a trend recently where the decision process starts with a focus on the short term due to the initial panic of the situation without empirical knowledge of long term implications. That’s just human nature, solve for the problem causing you the most pain. My intent with this post is not to find fault in anyone’s organizational decisions during a time of crisis or tell you what to do comprehensively, there are many factors that lead you to a decision and you have to find the best fit for your company. Some of these decisions may not be ideal under normal circumstance and that’s okay, do what you need to do. I just want to offer a few suggestions to ease what your organization, employees, and their families are facing that will improve their user experience and help you maintain your company’s security posture during this unprecedented global event. If you’re an EUC or Security Engineer/Architect/Leader and being told to do something that feels wrong from your years of experience, raise your hand. Educate your leadership teams on concepts they may not be aware of. Don’t run in the wrong direction. Run toward a positive long term business outcome.
Remoting environments – stop beefing up VPN
Pretty much all Fortune 500 enterprise organizations have remoting environments for Windows virtual app and/or virtual desktop delivery in some capacity. In a nutshell, the ability to securely stream the screen of a Windows virtual machine running in a data center or cloud over the Internet down to a user sitting at home without having to bridge your networks with a VPN. It’s just like Netflix, you watch a movie in Netflix’s data center that is streamed to you over the Internet but you don’t VPN into Netflix’s data center in order for this streaming to occur. You don’t keep the movie just like you don’t keep the virtual desktop that you are interacting with, it was just being presented to you over the Internet when you needed it.
You can easily scale your remoting environment to BOTH virtual desktops AND physical desktops. YES, physical desktops and laptops that were left running in the office under or on a user’s desk can be accessed remotely without the need for a VPN! You own this capability if you are a Citrix or VMware customer already – yes the same license allows you to launch physical machines in your office over the same secure remote display protocol once the agent is installed. Citrix guidance here and VMware guidance here. Better performance on stressed public networks than VPN. VPN also has a lot of considerations around split-tunnel vs. full tunnel that doesn’t often work well with cloud-based SaaS apps and content delivery networks (CDNs) in the modern world, which many of my peers are finding out for the first time and venting their frustrations on Twitter. Using Citrix HDX or VMware Blast Extreme remoting protocols adheres to a better Zero Trust security strategy that doesn’t expose your business network like VPN. Everyone talks about using network segmentation to segment VPN connections off from the rest of the business network in its own security zone but in practice, almost every VPN configuration out there I’ve seen can ping every desktop and server on your network from the user’s home network because it’s an easier configuration with less friction with end-users. That’s a big problem. Think through buying licenses or hardware for VPN technologies in the short term you may not recoup costs from and eventually have to pull user access and decom once your organization’s Security leadership realizes the true security impact.
I’ve had a long career in the Fortune 100 space. My first VPN replacement project was in the early 2000s for a very forward-looking security conscious company that saw the value of investing in virtualization and remoting protocols when home users didn’t have fiber running to their houses and bandwidth was at a premium. It was done to conserve bandwidth and for better security posture from both insider threats and intellectual property theft (data exfiltration). That has not changed in all this time. There are some reasons where VPN or per-app VPN are still necessary but for most enterprise use cases, remote display protocols encrypted over TLS are superior. Invest in scaling these technologies more so than VPN.
Your on-prem EUC control plane is antiquated
A lot of companies were caught off guard as far as capacity or regions they needed on-premises end-user computing control planes and associated infrastructure in. Please do try to move to cloud control planes that are vendor managed as a subscription-based platform-as-a-service (PaaS) like Citrix Virtual Apps & Desktops Service, VMware Horizon Cloud, or Microsoft Windows Virtual Desktop when cycles permit. I personally moved to a cloud control plane service in late 2017 managing both my on-prem and cloud workloads in a hybrid fashion and have never looked back. On-prem Citrix, VMware, and Microsoft control planes for end-user computing are now legacy in 2020. They cannot compete with the pace of change in information technology nor the world in general so begin to consider these on-prem control planes End of Life, use them now to get you through your immediate needs but plan to decom soon. If you are a technology leader and find yourself having to beef up your on-prem control planes and gateways, now is a good time to pivot to a service that will be much faster than what it will take your teams to stand up new infrastructure. Your EUC (end-user computing) teams cannot run a service comparable to the aforementioned services as much as you would like to believe they can. That’s been the reality of the EUC industry for the last several years. But your EUC teams can consume one of these services and be agile to fit the ever-changing needs of your business.
Cloud burst capacity is a real thing
Many organizations are finding out how nice it was they invested in Microsoft Azure ExpressRoute, AWS Direct Connect, & Google Cloud Interconnect circuits with some presence in a public cloud right now. Some that didn’t embrace hybrid cloud architecture when they should have are now suffering trying to buy, rack, stack, and cable equipment in their data centers. Some are activating portions of their BCP (business continuity planning) environments in an effort to find additional resources if they were running old active/passive methodology. Unproven beyond tabletop exercises and now being pushed into active/active methodology by force which presents a slew of other problems. Use Microsoft Azure, AWS, and/or GCP clouds for burst virtual desktop/session host capacity, resiliency is key. It’s pay-as-you-go so no capital investment is needed for temporary periods like this when greater capacity is needed. Azure especially has made tremendous moves to improve resiliency in the last 6-8 months behind the scenes that has been impressive. Microsoft, Amazon, and Google run a better data center than your company can and the ‘pay for only what you use’ model is better than any collocation data center deal you have signed in the past. This is ideal for compelling events and instant scale/capacity.
Issuing $3000 laptops to home users isn’t easy
Home users don’t have newer PCs? Just hand them cheap IGEL UD Pocket thin clients and they’ll love you for it because technically the whole family can use some of the features on it for things like schoolwork without compromising the remote business environment. It’s a 2-in-1. This is so much more cost-effective and secure than deploying $3000 laptops that may not have embraced modern desktop management like Windows Autopilot with out-of-box setup capability to everyone that didn’t have one before. Or replacing a laptop. A friend working from home had her work laptop die this week and the laptop manufacturer won’t send a service tech to repair onsite due to Coronavirus concerns so she can’t work from home anymore. Understandable and I’m 100% agreeing with said laptop vendor as it’s the right move to protect their employees. However, a UD Pocket that requires no pre-provisioning and can fit in an envelope mailed to my friend that she can use with any old host computer laying around can easily solve this problem.
Remember how you kept hearing identity was the new perimeter?
Leadership teams are now understanding this wasn’t marketing fluff. The walls of your office building don’t define work. Work can be done anywhere Internet-connected as long as the user can authenticate since pretty much everything from SaaS apps to Windows apps and virtual desktops are now fully “webified” and accessible via a browser. Move to a cloud identity provider like Microsoft Azure AD or Okta UD if you haven’t done so already. Yes even for your legacy on-prem appliances that don’t understand modern authentication. AAD and UD are both backwards compatible with legacy RADIUS.
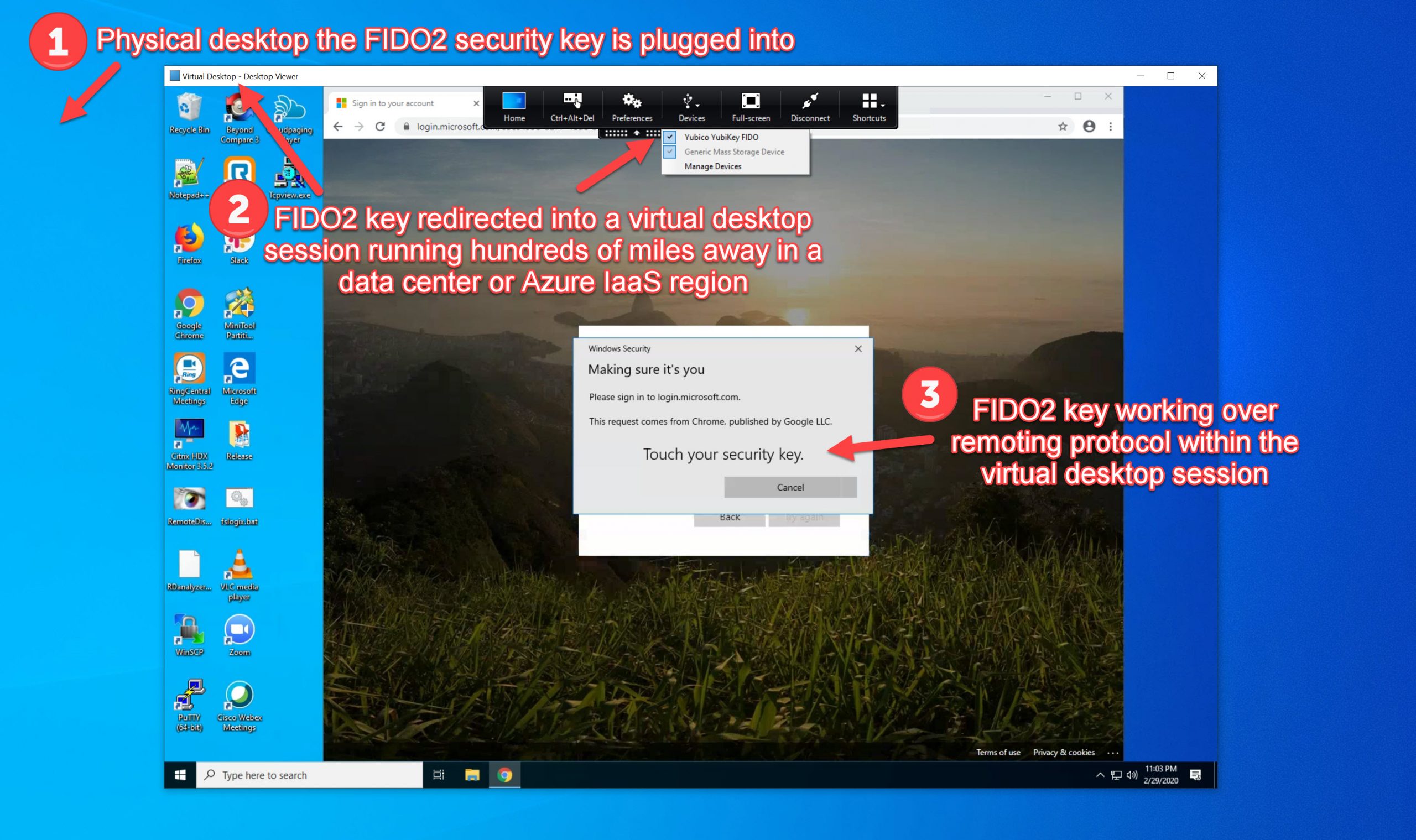
For the collective sanity, enable MFA (multi-factor authentication) for everyone and leave it enabled! Never ever disable enterprise security posture for convenience. You want convenience + security then use Azure AD and Microsoft Authenticator passwordless phone sign-in and FIDO2 security keys, literally checkboxes to enable. So convenient it feels like cheating when you login. Users trying them for the first time will turn to you and ask, “That’s it?”. Now, more than ever, leadership teams are realizing what many like myself have been saying for years, your user’s identity is the perimeter and not some firewalls in your datacenter.
Your human capital is more important than any IT service or system
Be realistic about your human workforce capability. Each of your IT personnel is under extreme stress experiencing a multitude of potentially unique problems in their lives different than you or others. Children at home, partner with no income stream, partner or family members on the front lines, older family members, extended family members, family members that have tested positive and recovering, death of a loved one, etc. You can’t possibly know the situation of each person because you’re dealing with your own reality and coping as best you can right now. And things are still changing daily for you and all these people in your life.
You don’t have to boil the ocean when you have a limited IT workforce. You may have existing investments in much of this without needing some emergency CFO budgetary approval. If you don’t, many of these are subscription-based services so no large capital expenditures. Many IT vendors are even giving you free temporary access or discounts to their products and services in this time of need thankfully. Just deliver some of the simpler changes now that are easy for your org with whatever investments and personnel you have, some later. Adopt a continuous improvement and delivery mindset where you accept nothing is ever perfect. Stay calm and keep making positive changes in your enterprise thinking long term business outcomes. Work will always be there so allow your teams to prioritize taking care of family first and foremost. Stay positive, stay empathetic to your fellow humans, & stay safe.