The future state of password-less authentication for Microsoft Windows enterprise environments will be a combination of 3 options:
- Windows Hello for Business
- Microsoft Authenticator
- FIDO2 hardware security keys
Of these, FIDO2 is the non-proprietary method and can be used with other IdPs (identity providers), non-Microsoft environments, as well as many consumer web services which means all-around security for your users. In the upcoming years, your company will undoubtedly be migrating to a combination of these access management solutions if not already using them.
This capability in now in Public Preview for all Azure AD customers as of July 2019. Congrats to the team on delivering this capability and a BIG thanks to Swaroop Krishnamurthy (Principal PM Manager at Microsoft) and Libby Brown (Senior Program Manager, Cloud Authentication Team at Microsoft) for letting me give some early feedback.
What is FIDO2 and why should I care?
FIDO2 is a new open authentication standard for both consumer services and enterprises. It is a joint effort by the Fast IDentity Online Alliance (FIDO Alliance) and the World Wide Web Consortium (W3C) who had a mission to make web authentication stronger in an era where passwords are the biggest vectors for compromise in both our personal and corporate lives. They wanted to actualize the death of the password. The FIDO2 authentication standard is the result of many years of work. FIDO2 is actually composed of two different components, WebAuthn and CTAP2.
The W3C worked on the WebAuthn web authentication standard which forms the core of FIDO2. It was officially made a web standard on March 4, 2019, to great fanfare in the identity and access management community. WebAuthn creates a standard for web-based applications and web services to use public-key cryptography. Everything from identity providers like Microsoft and Okta to consumer services like Twitter, GitHub, etc. are already using WebAuthn with many more services becoming compatible with this new standard every month. Web browsers need to be able to support WebAuthn as well in order to use these services obviously, so only modern web browsers will work. I’ll let you know the specific versions later on in this write-up.
The FIDO Alliance worked on the other half of the solution called CTAP (Client to Authenticator Protocol). There are two versions of CTAP, CTAP1 and now CTAP2 which made its debut in 2018. CTAP2 is the protocol that hardware security key manufacturers need to conform to in order to use the FIDO2 standard. CTAP2 is an evolution of the older FIDO U2F standard which used CTAP1. CTAP2 is compatible with WebAuthn while the older CTAP1 is not. Therefore, you should always attempt to purchase FIDO2 compatible keys for your organization and not the older FIDO2 U2F compatible keys.
Please do not confuse the older FIDO U2F (Universal 2nd Factor) standard with FIDO2. They sound similar but FIDO2 is the successor to FIDO U2F. FIDO2 offers full password-less authentication while FIDO U2F is designed to be used with a password as a traditional second factor only. Bottom line, only purchase FIDO2 compatible hardware security keys for your organization if you want to go password-less with identity providers like Azure AD. In my opinion, FIDO U2F should be considered deprecated and you should only be looking at FIDO2 going forward for your organization.
What is the FIDO Alliance and why should I trust them?
Pretty much everyone in IT knows who the W3C is, they were formed in 1994 and set the standard on how the World Wide Web works today. But the FIDO Alliance is much newer formed in 2013 to promote stronger authentication standards. You can read more about the alliance on their website at https://fidoalliance.org/. As of today, it is composed of over 260 members from what I can count on https://fidoalliance.org/members/ of which 40 are Board Level Members.
I decided to break down these 40 Board Level Member logos by their focus area in alphabetical order, simply because I was curious and my risk management mentality makes me do odd classification groupings in my head. A few of these logos, I had to research by going to their websites and just determining what they do because I had never heard of them:
Insurance Organizations
- Aetna
- USAA
Web and Technology Services
- Alibaba Group
- Amazon
- LINE
- Microsoft
- VMware
- Yahoo Japan
Financial Organizations
- American Express
- Bank of America
- BC Card
- ING
- Mastercard
- PayPal
- VISA
- Wells Fargo
Processor Chips & Electronics
- Arm
- Infineon
- Intel
- Lenovo
- NXP
- Qualcomm
- Samsung
- Synaptics
Security, Identity, Authentication
- Daon
- Egis Technology
- eWBM
- Feitian
- Hypr
- IDEMIA
- Nok Nok Labs
- OneSpan
- Onfido
- Raonsecure
- RSA
- Thales
- Yubico
Telecommunications
- NTT Docomo
If you scroll down further on the page of members, you will also see Sponsor Level Members which include some recognizable heavy hitters like:
- Chase
- Discover
- Duo
- eBay
- Fidelity Investments
- Fujitsu
- Goldman Sachs
- HID
- Hitachi
- Huawei
- JCB
- LG
- Mozilla
- NEC
- Okta
- Plantronics
- Symantec
- Vanguard
- Verizon
Under the Government Level Members, there is a really big one that should catch everyone’s attention. 🙂 :
- NIST
In summary, the FIDO Alliance Board Level Members alone may have a few logos you recognize and trust already. So that question of why you should trust them and FIDO2 is answered pretty quickly. If this many people at this many global companies can agree to something, they likely have a pretty secure and open standard on their hands that the world is going to adopt very easily.
What password-less authentication methods can you enable with Azure AD now?
Part of the delivery of FIDO2 in Azure AD involved, in my opinion, the far more important Authentication Methods feature. This feature allows you to target specific security groups in your organization with specific types of password-less authentication. At this time, you can select 2 types:
- FIDO 2 Security Key
- Microsoft Authenticator password-less sign-in
This is how it looks for admins and I’ll go into this greater further in the guide:
How does a user register their FIDO2 key with Azure AD?
They use the new converged registration portal which combines all forms of security-related registration to a single portal. Since it is in Preview right now, you have to enable it on your tenant and I will show you how to do this further in the guide. This is self-service portal that a user can register any of their authentication methods such as Microsoft Authenticator, FIDO2 keys, etc. on. At some point I expect the old https://aka.ms/mfasetup portal will be deprecated in favor of this new combined portal and perhaps Microsoft will set up a 301 Permanent Redirect on the old portal to help users in you organization transition to it easily if they have saved bookmarks or old documentation floating around.
Users can use either of the 2 new URLs during the Preview phase with option 1 below being the easier to remember for users in my opinion and what you should put into any end-user facing documentation at this time. Option 1 simply the overview page and redirects the user to option 2 anyhow for them to perform their security related actions:
1. https://myprofile.microsoft.com/
2. https://mysignins.microsoft.com/
Choosing a FIDO2 security key to use with Azure AD
FIDO2 is an open standard so if the security key meets this standard, it’s likely going to work with Azure AD just fine. You can use internal authenticators (secure hardware that is built into the computing device itself) or use external authenticators like hardware security keys. I prefer the latter because you are separating the computing device from the authenticator which gives a slight extra measure of security.
Additionally, hardware security keys are often multi-protocol so you can use FIDO2 as well as legacy authentication protocols while you get your apps and devices all compatible with FIDO2 over time. The “one ring to rule them all” strategy.

You may have seen me post on social media running around testing all sorts of FIDO2 keys earlier in the year:
Just got my #FEITIAN BioPass #FIDO2 Security Keys for testing password-less authentication with #Microsoft Azure AD! These have a built-in fingerprint reader for added #biometric security! Will take them to #CitrixSynergy if anyone wants to see them in person. #NoMorePasswords pic.twitter.com/3Ge0uUCfvX
— Jason Samuel (@_JasonSamuel) May 18, 2019
I’ve reviewed several FIDO2 keys from several manufacturers since then and I feel like Yubico and Feitian have FIDO2 compatible keys that are the way to go for the enterprise due to their small form factors. If you are an organization that uses smartcards, there is no need to lifecycle your existing smartcard deployment, but you can consider issuing the HID Crescendo cards to some pockets of users as they will offer the benefit of facilities access + modern FIDO2 authentication into Azure AD protected Windows 10 and web apps. I have personally been testing Yubico and Feitian with Azure AD but have not been able to acquire an HID card yet. As soon as I get one I’ll review it.
I encourage companies to provide small form factor USB FIDO2 keys to their employees and ensure they know the key is theirs to keep forever. FIDO2 keys can be registered with both enterprise and personal accounts in the user’s daily lives. By giving the keys to your users as part of their employment, you are encouraging them to practice good security hygiene in both their personal and enterprise lives. I do not recommend attempting to retrieve FIDO2 keys from your users upon termination of employment and attempt to re-issue them to other users. This can land you in a bit of a legal issue with users who have forgotten their keys are being used with their personal services and then attempt legal action to get the key back. Avoid this liability and encourage good user security by freely giving these keys to your users with no strings attached.
Yubico YubiKey 5 FIDO2 compatible security keys
I bought a Yubico YubiKey 5 NFC from Amazon (https://www.amazon.com/Yubico-YubiKey-USB-Authentication-Security/dp/B07HBD71HL) as my first FIDO2 compatible security key a while back. They are pretty much the only FIDO2 key that you can test immediately with Amazon Free One-Day delivery with no need to wait on your procurement department. At $45 the cost is negligible so just use your personal credit card and buy it for personal reasons. You don’t need to tie it to a company expense if you work in an organization that makes you jump through hoops to buy small things like this, just buy it for yourself, try it out, if you don’t find value then return it. The YubiKey5 comes in many form factors of which I’ve tested 3 out of the 5 now:
They all work perfectly so leave the choice of form factor to individual user preferences depending on their computing devices and daily workflow. I want to note that the gold disk on the YubiKey 5 NFC is NOT a fingerprint reader, it’s a simple copper plate that you touch and acts sort of like a button. You can touch it with anything wet and mimics a human finger really, I’ve completed the action of “touching the security key” using a moist Q-tip successfully just to help people understand this visually. My point is, there is no special enhanced security on the YubiKey 5 NFC vs. the others so choose the right form factor based on the system it is being plugged into. Biometric capability is something I would love to see Yubico add to their hardware security keys instead of users having to remember PIN numbers.
I also want to note that I purchased the NFC version thinking it would work with iOS on my iPhone. Unfortunately, Apple has been a bit slow to adopt FIDO2 so their NFC implementation could only scan and read an OTP from the key and do absolutely nothing with FIDO2. You could use iOS apps like AuthLite NFC to play around with this capability but it was mostly useless for enterprise needs. The YubiKey 5Ci with the Lighting connector + USB-C connector works but it’s not intended for daily authentication, no one wants to plug in a key into the bottom of their phone, it’s just not practical. The use case for the 5Ci is more of as a bootstrapping authenticator. In recent news, the upcoming iOS 13 will support FIDO2 and NFC so I’ve very excited to test out this capability. Yubico recently released a blog about this just after the September 2019 Apple iPhone 11 launch event last week: https://www.yubico.com/2019/09/yubico-ios-authentication-expands-to-include-nfc/. Now I’ll finally be able to use the key with my iPhone the way I pictured it in my head when I bought it! 🙂
Feitian BIOPASS FIDO2 compatible security keys
The Feitian BIOPASS K26 and K27 were the next FIDO2 security keys I received and I really love these for the fact they have a fingerprint reader built-in. This way you can use a fingerprint instead of a PIN. You are really using your fingerprint locally here before the key sends a “YES” to the system so it’s a nice little extra layer of security that uses a biometric to prove that you are you. I’ve tested the K26 and K27 with Azure AD so far. They are both priced at $60 each.

The K33 and K43 very interesting because they both use biometric + BLE (Bluetooth Low Energy) meaning you can use it with devices that don’t have NFC capability but have Bluetooth. The K33 comes in at $86.25 and I haven’t gotten my hands on one just yet but imagine it will work just as well as the USB versions. Authenticating from across the room sounds pretty enticing. 🙂 I don’t know what the pricing on the K43 is but imagine it will be a little more than the K33.
HID Crescendo FIDO2 compatible smartcards
The last item is the HID Crescendo C2300 series smartcards of which I’ve only ever had the opportunity to see a prototype of. Here is an image of the HID C2300 FIDO2 compatible smartcard with the default branding on it. Just imagine your headshot photo on it if you intend to use it as a name badge for physical access like many companies do:

I’ve never held a production HID FIDO2 compatible card in my hands yet so I can’t tell you about my experiences. The benefit here is using it for typical proximity card needs such as facilities access within your building (doors, elevator banks, lobbies, parking garages, etc) and also use the same smartcard for accessing Windows 10 physical devices, laptops, and of course SaaS apps using legacy PIV as well as modern FIDO2. This is obviously something very much aimed for enterprise devices with smartcard readers and not for personal (though they can obviously be used for personal devices as well if the user purchases an external smartcard reader from Amazon). I have no idea what the cost of these new cards is but knowing HID prices for regular smartcards, I imagine it will be pretty high. It will be a real investment to lifecycle your existing smartcards and move to these new FIDO2 compatible smartcards.
I feel like healthcare organizations will be able to take great advantage of these for “tap and go” type functionality for clinicians (doctors, nurses, etc.) where they have to go from room to room and use multi-user kiosk systems quickly using their name badge. These organizations have traditionally had to rely on expensive 3rd party password-less SSO solutions like Imprivata and Caradigm (now owned by Imprivata) to tap their badges on a badge reader and perform SSO into Windows. Now that FIDO2 is built right into the Windows 10 operating system and is far more secure than the password manager/credential stuffing approach, you may not need these types of 3rd party solutions anymore depending on what feature set you are currently using. When using FIDO2 + PIN it’s not quite “tap and go” yet but more like the traditional PIV based smartcard. When using FIDO2 + forms of biometric (not fingerprint though due to gloves), you can simulate “tap and go” capability using nothing but Windows 10 and no additional software. The possibilities to do many things are now there in the Windows credential provider with something as flexible as FIDO2.
I always urge people to move away from 3rd party SSO solutions when they are not paying maintenance or staying on top of upgrades as I’ve often experienced them holding EUC (End User Computing) environments hostage with a particular version meaning nothing else in that environment can get upgraded until the SSO solution gets upgraded. You’re either waiting on the ISV (independent software vendor) to come out with the latest version or some team within your organization to actually deploy that new version. There is nothing I loathe more in environments than middleware holding up progress in an organization. Now you can align your healthcare EUC environment lifecycle with Microsoft Windows since FIDO2 is supported for newer Windows 10 builds and beyond!
Enabling Authentication Methods and FIDO2 Security Keys for your Azure AD tenant
Microsoft fully supports everything delivered in a Public Preview so you can start deploying the feature now for production users if you wish. The only disclaimer I am aware of is that certain features may change or be added by the time of General Availability (GA). Nothing is going to get removed on you out of the blue. None of these changes or additions will impact anything delivered in Public Preview right now so you can safely begin deploying and testing these features in your company now. Please note that some of the screens may look a little different by GA and I will do my best to come back and edit this guide if there is anything major that changes you may need to know about.
Let’s get started on enabling FIDO2 in Azure AD as an authentication method.
1. With a Security Admin or Global Admin account, sign in to portal.azure.com and go to Azure Active Directory > User Settings > Manage user feature preview settings:
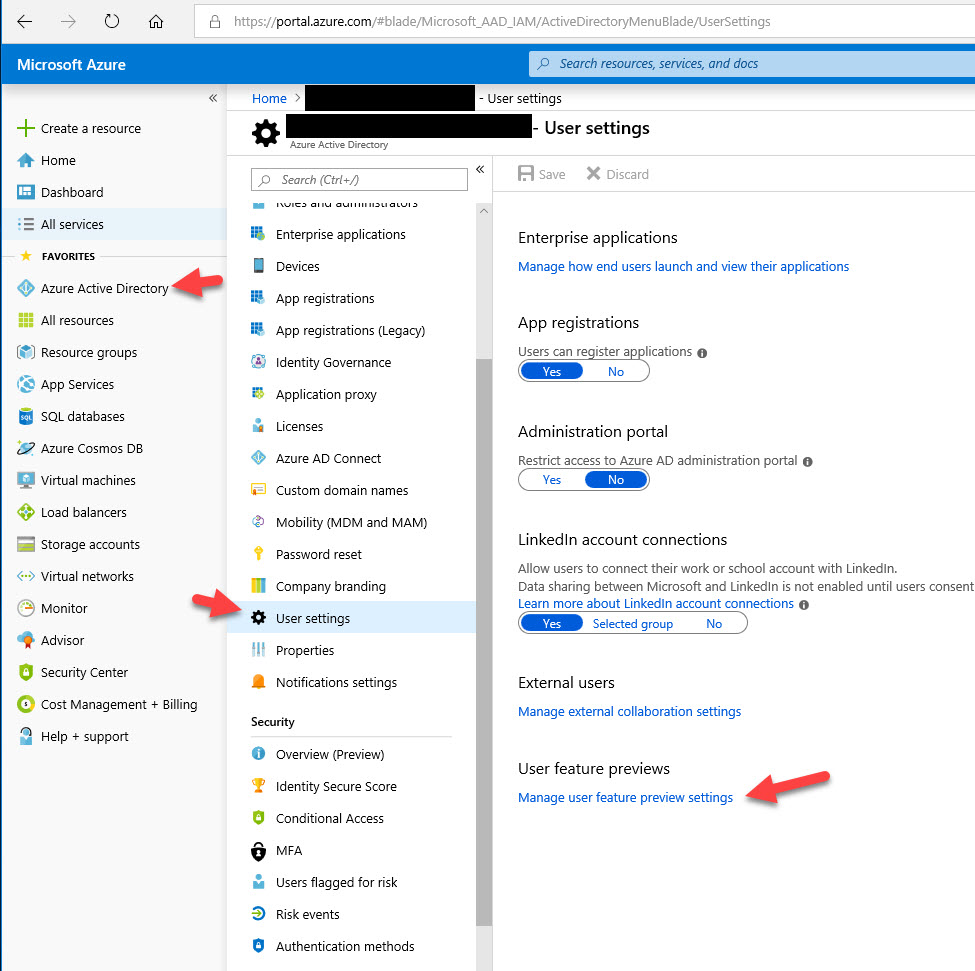
2. Under the “Users can use preview features for registering and managing security info – enhanced”, change it to All and then hit Save. What this does is enable the new combined registration page. End users cannot register FIDO2 hardware security keys with Azure AD any other way so you must do this step. This will become the default soon so no issues setting this to All for your organization:
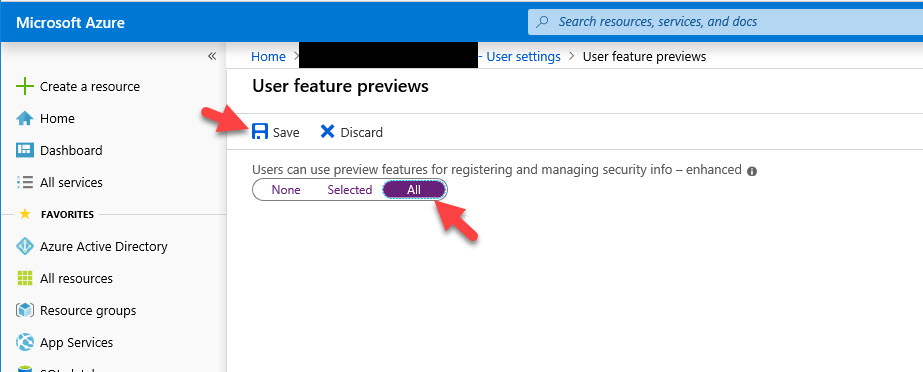
If you highlight over the little information icon, it will say “This will enable users to register and manage their security info for Multi-Factor Authentication and self-service password reset in a single experience”. I encourage all customers to begin enabling this feature as it will be the standard at some point:
3. Once you save it, it will show a green checkmark in the top right and say “Access Panel” settings have been sucessfully updated:
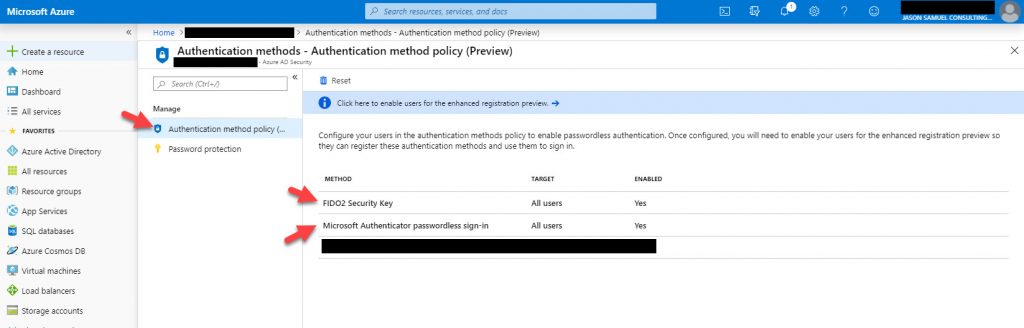
4. Now go to Azure Active Directory > Authentication Methods under the Security section:
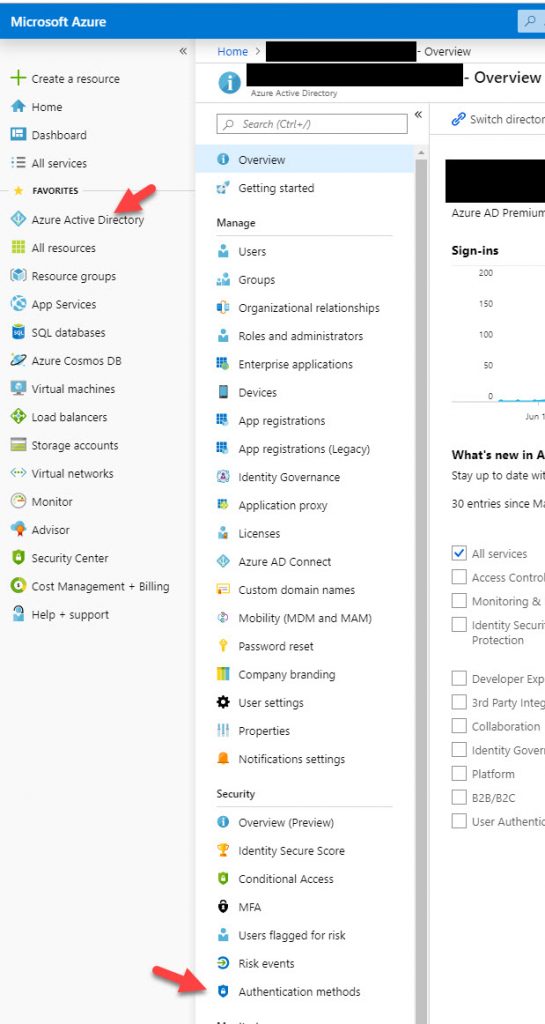
5. Click on “Authentication method policy (Preview)” and you will see the options to enable “FIDO2 Security Key” and “Microsoft Authenticator passwordless sign-in”:
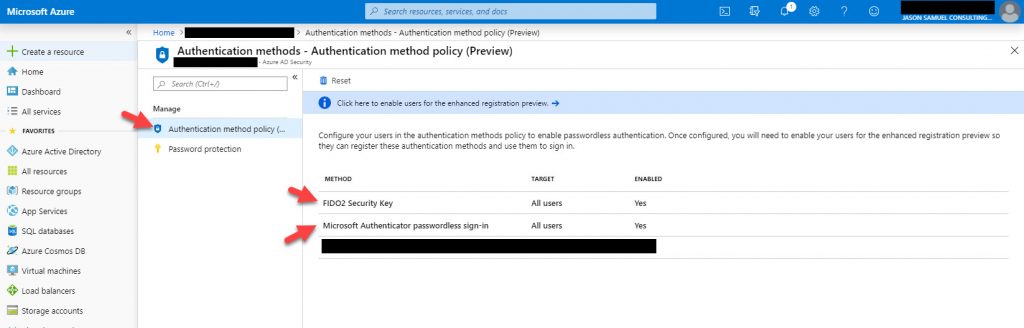
6. Click on FIDO2 Security Key, change the Enable dialog box to Yes, and then hit Save:
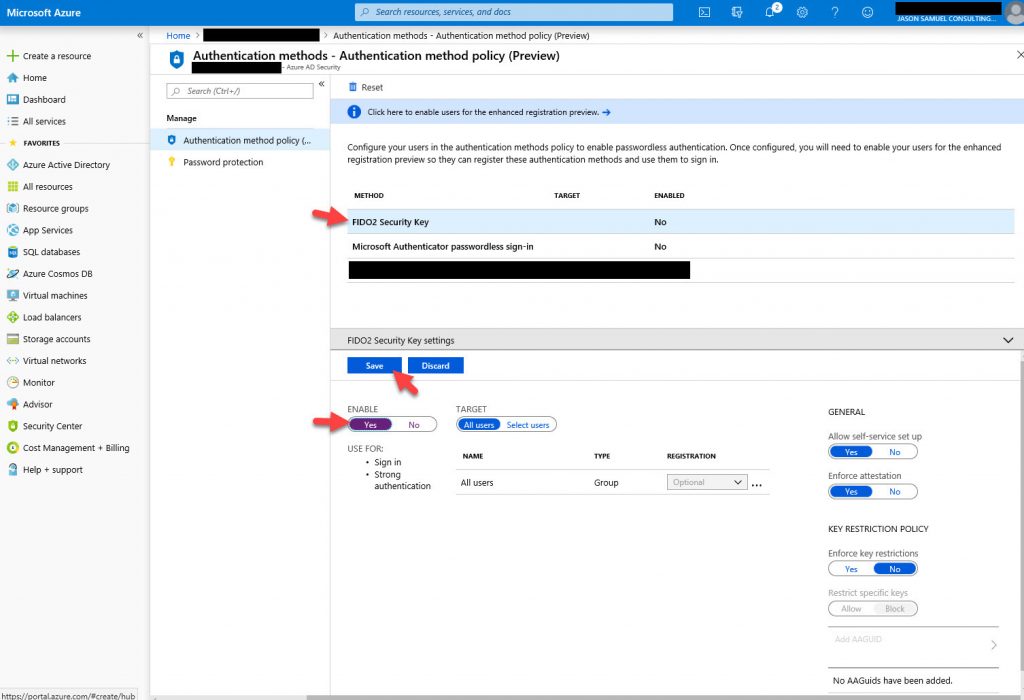
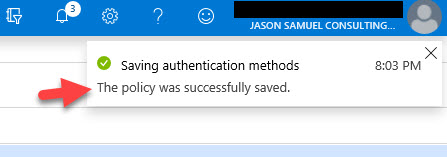
7. Once the authentication methods have been saved successfully, you will see a confirmation with a green checkmark in the top right section:
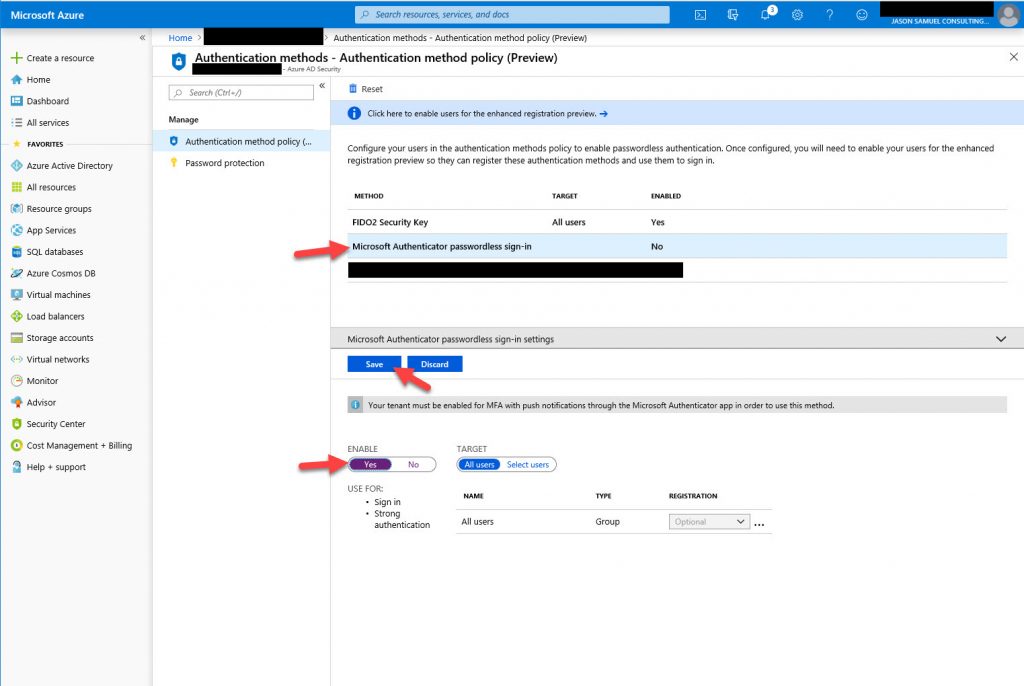
8. I also encourage you to enable Microsoft Authenticator passwordless sign-in for your users the same way. This eliminates the need for the tenant wide policy you had to enable PowerShell in the previous Public Tech Preview for this option. It also gives you much more granular control this way:
Enrolling your FIDO2 security key with Azure AD
9. Now comes the end user experience! With a regular user account, log into https://myprofile.microsoft.com. You can use a private session in your browser if you still have your Global Admin account logged into the Azure portal. Enter your email address for this account:
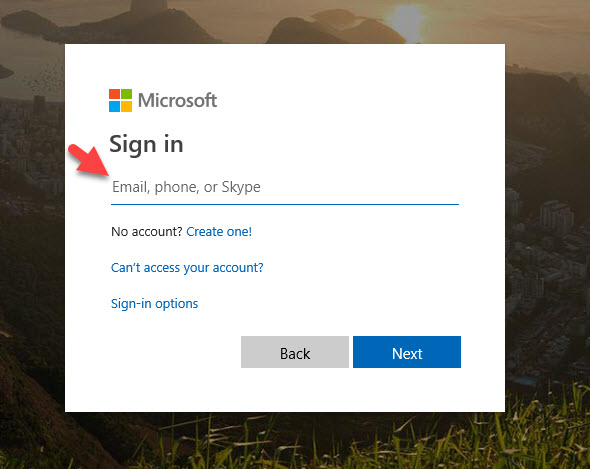
10. Now complete authentication. In my case, this account was already enrolled in the Microsoft Authenticator password-less phone sign-in so this user gets that experience already:
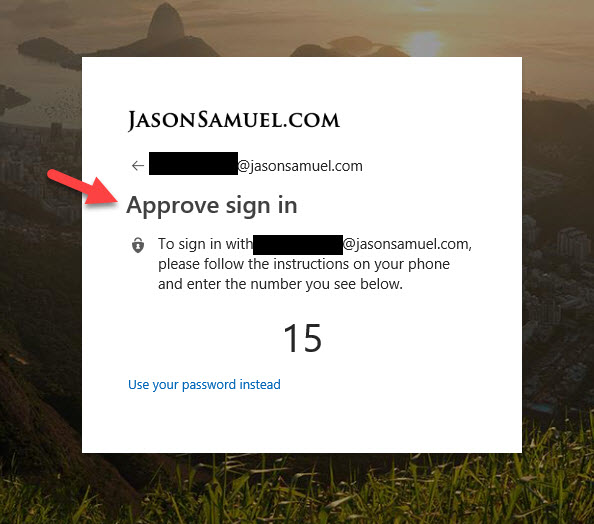
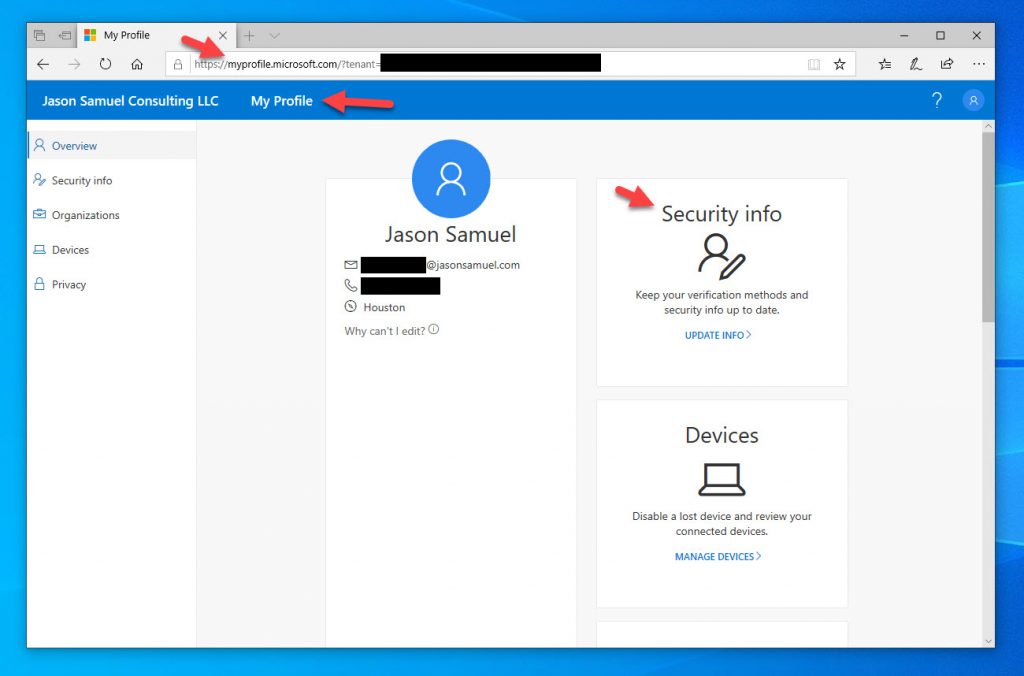
11. Now you will see the new combined experience on https://myprofile.microsoft.com. You will see a tile called “Security info”. Click on this tile:
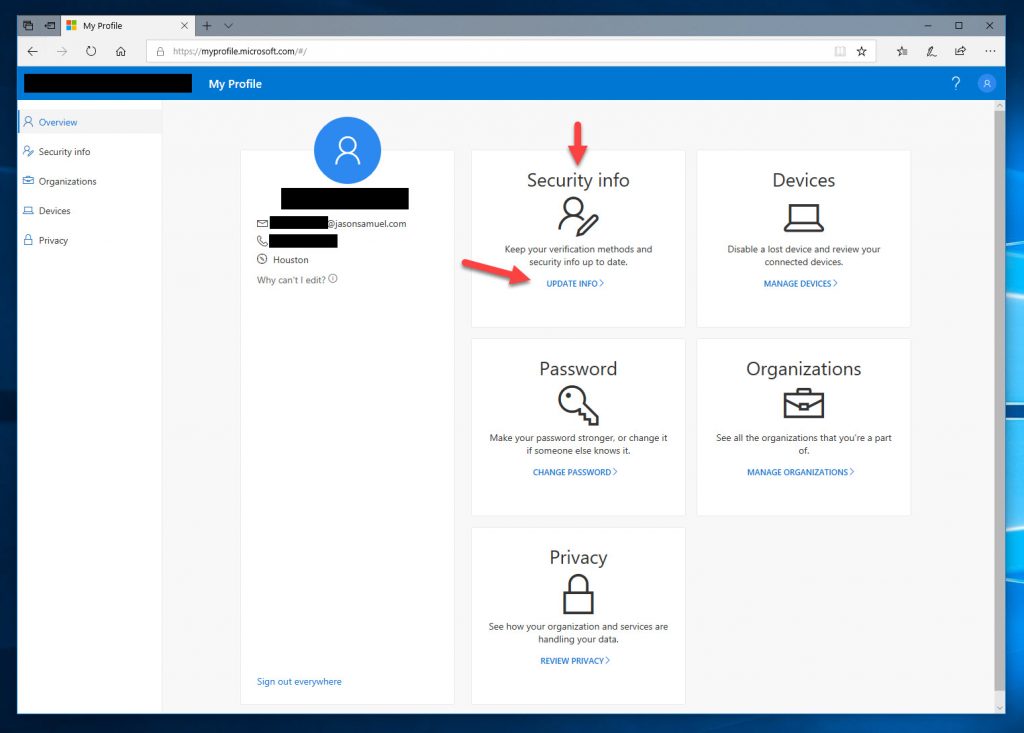
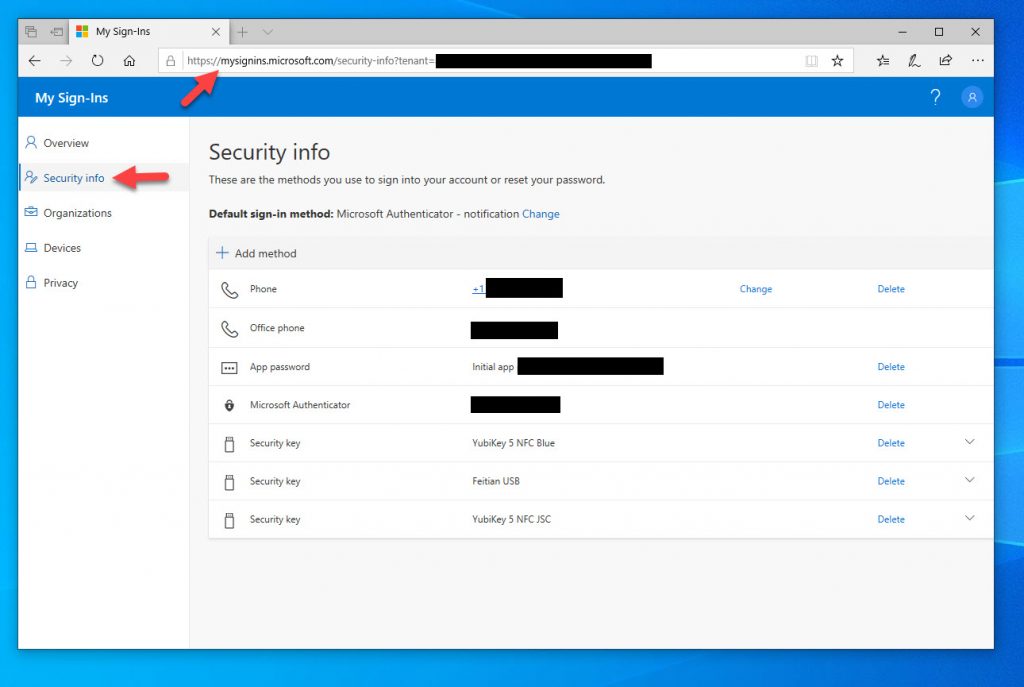
12. This will do a redirect you to the https://mysignins.microsoft.com portion of the website. I have noticed this website is considered more sensitive to your end-users so the timeouts and need to re-authenticate have smaller windows of time on this portion of the website, and with good reason. This page controls both Azure MFA options as well as anything security for your employees. You can see here since I am already enrolled in regular Azure MFA as well as password-less phone sign-in with Microsoft Authenticator those options are already shown here. If I wasn’t enrolled, I can simply Add them here and no longer need to visit https://aka.ms/mfasetup anymore. This is a much cleaner and uniform experience for your users so I encourage every company to begin using this. Go ahead and click “Add method”:
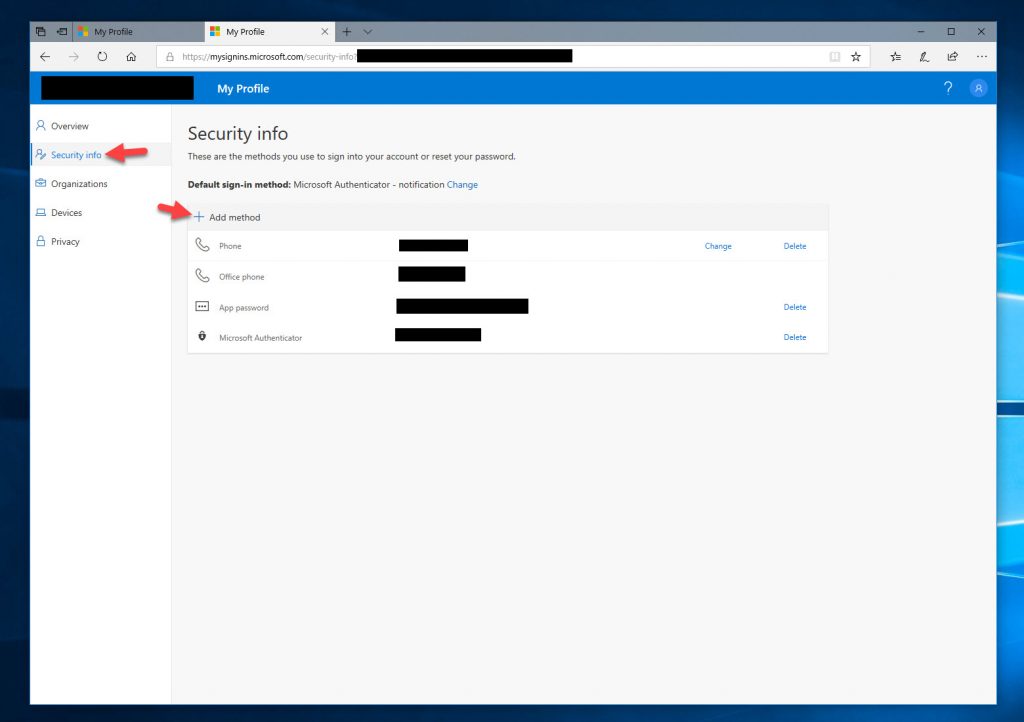
13. Hit the drop-down arrow and select Security key:
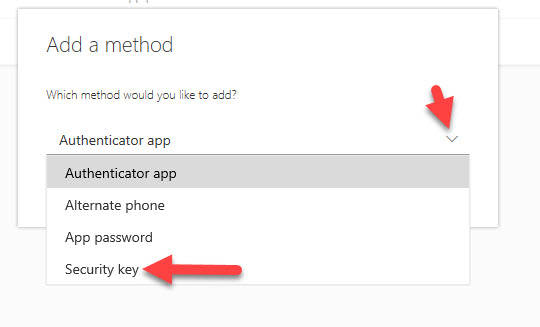
14. Now that Security key is select, hit the blue Add button:
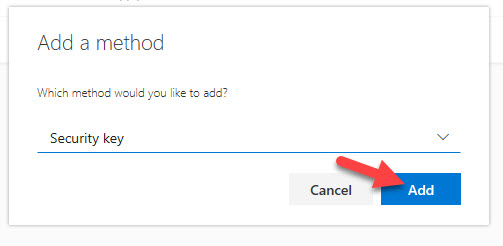
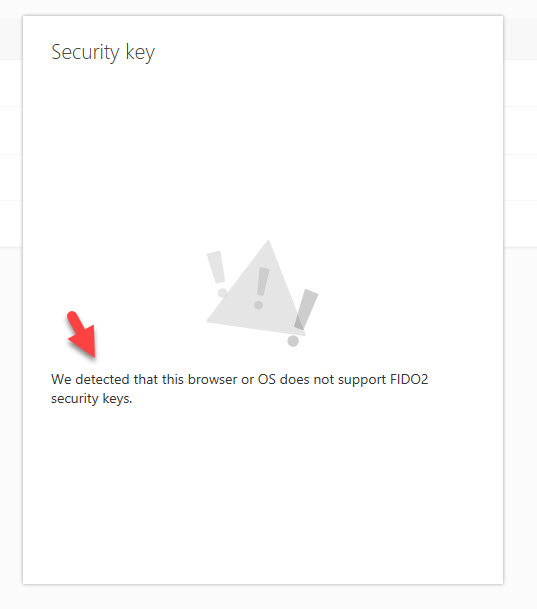
15. If you are using an OS older than Windows 10 1809 and the associated Edge browser, you may receive an error like this saying “We detected that this browser or OS does not support FIDO 2 security keys”.
You can do a number of things here to get around this:
- Run Windows Update and get on Windows 10 build 1809 with updated Edge. Windows 10 build 1903 from May 2019 gives you even more FIDO2 support for Windows 10 lock screen logins so try to shoot for that version if possible.
- Use Firefox version 67 from May 2019 or newer
- Use Chrome latest versions
I personally run Windows 1803 on one of my older systems with Chrome version 76 (76.0.3809.132 specifically) and use my FIDO2 key to login to Azure AD protected web apps just fine as well as the https://myprofile.microsoft.com portal. When I first started testing FIDO2 with Azure AD several months ago, support in Chrome was not there and I could not get it to work. It is now there and works just fine. I’m not sure which version started supporting FIDO2 and I can’t spot anything in the Chrome release notes on when they added support. Just use the latest version and you’ll be fine.
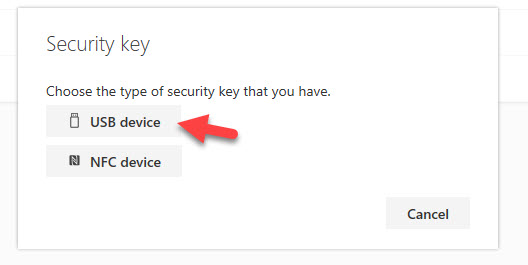
16. In this example, I am using Windows 10 1903 from May of 2019, and I get the options to add either a USB or NFC FIDO2 key in my Edge browser. I will select USB device here:
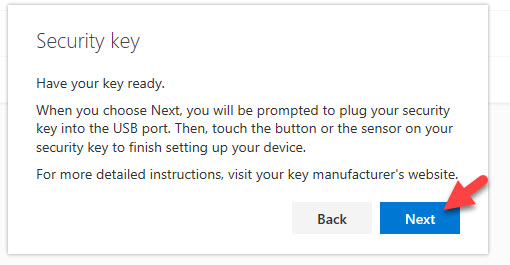
17. Ensure that your FIDO2 has been plugged into the USB port of your desktop or laptop, then hit Next. In my example I have plugged in a YubiKey 5 NFC into the USB port of my system:
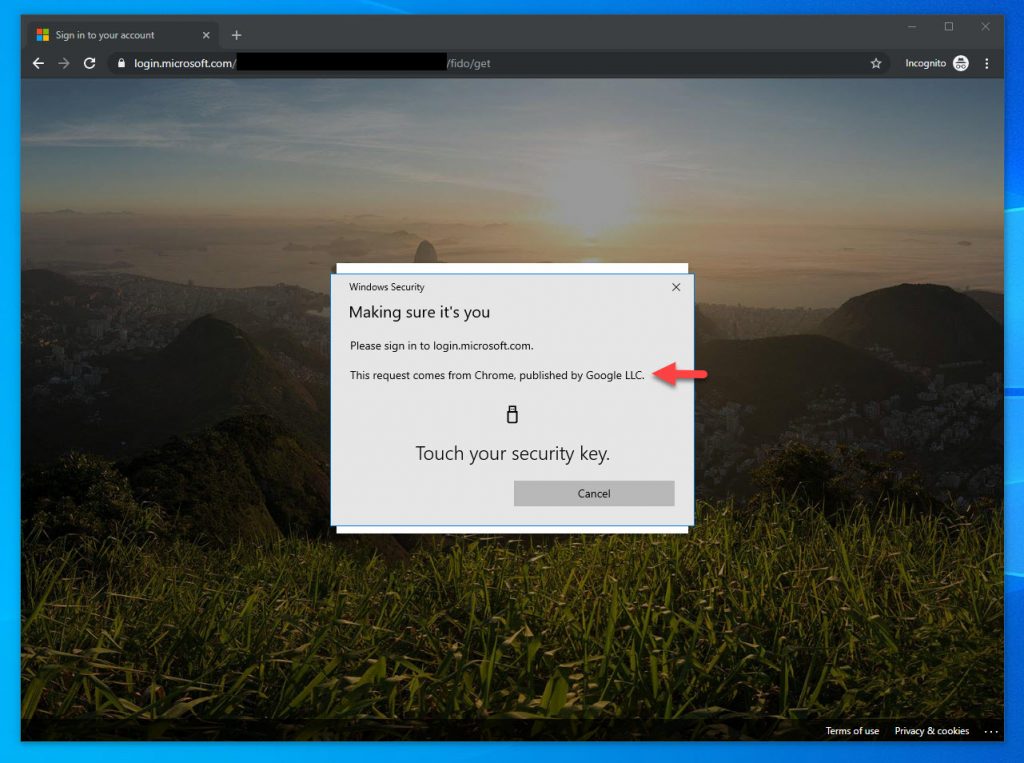
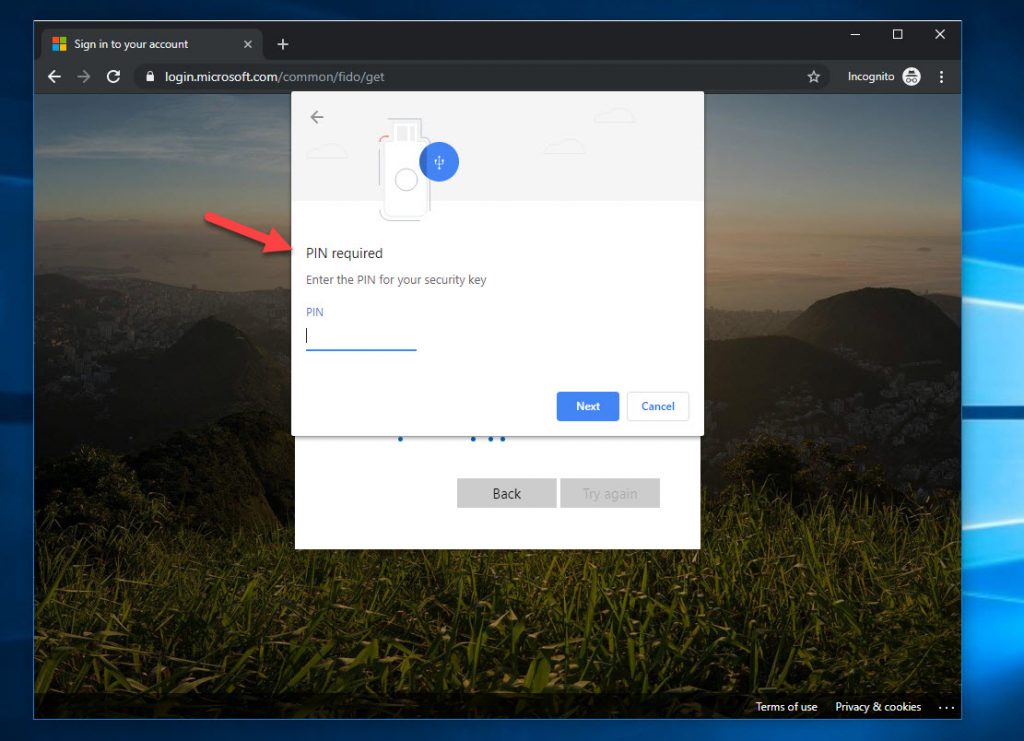
18. You will be redirected to the familiar Microsoft Azure AD login page and be prompted to create a PIN for the security key:
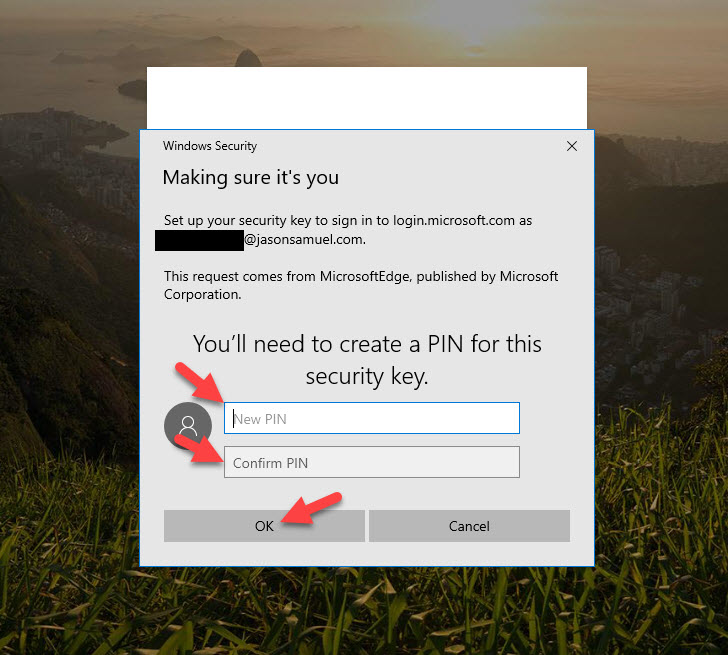
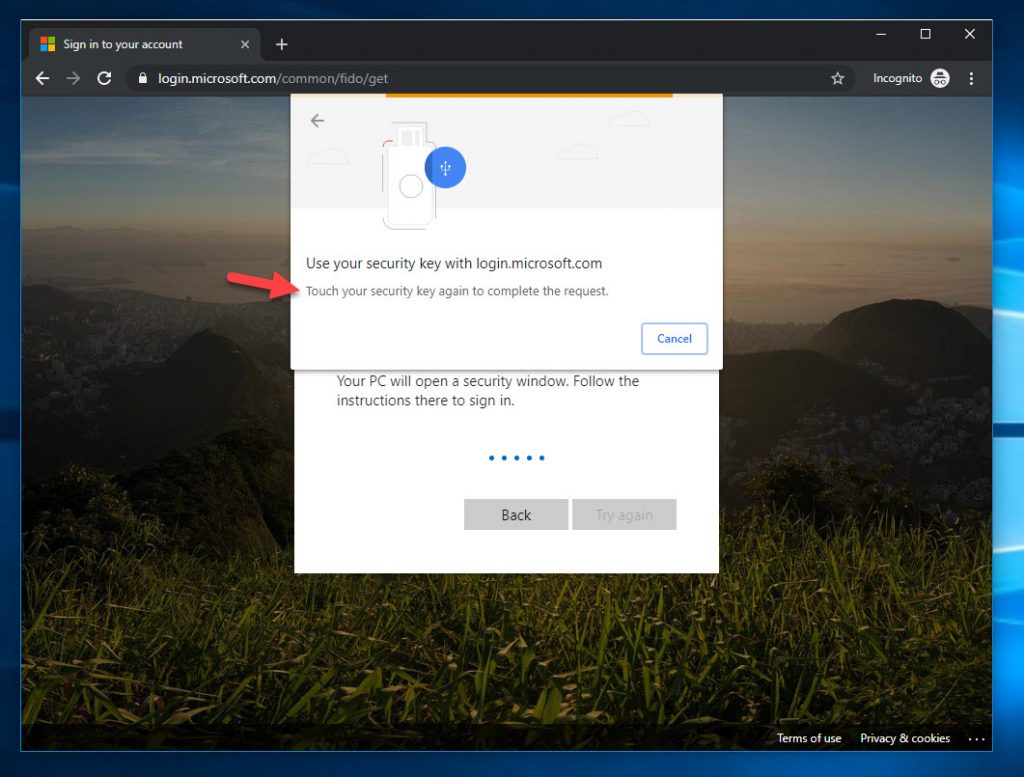
19. Now it will prompt you to perform an action on the FIDO2 security key. In the case of the YubiKey 5 NFC, I just touch the gold disc on the device:
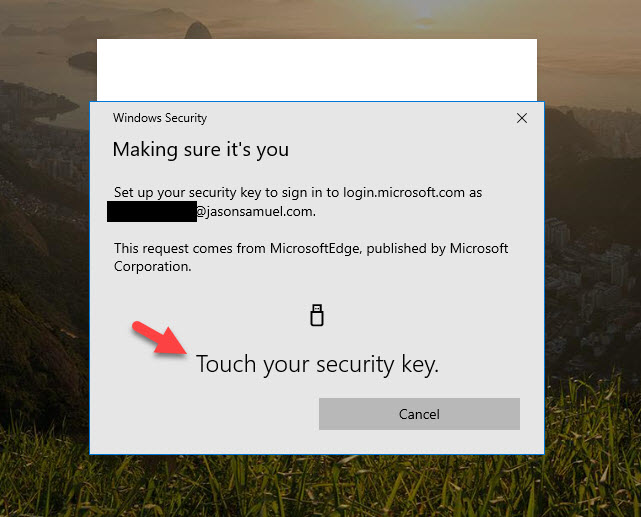
20. Now you will be redirected back to the https://mysignins.microsoft.com portion to complete your setup by giving your FIDO2 key an easily recognizable name. I love this feature because as someone that owns many FIDO2 keys, I have the power as the end-user to differentiate them easily here in a way that makes sense to me:
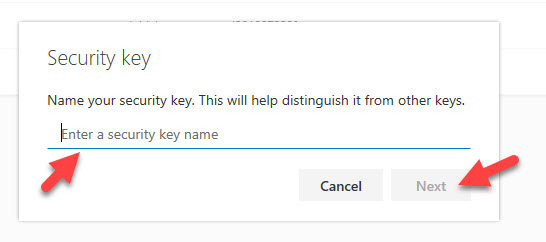
21. Once you name your key, hit the blue Next button:
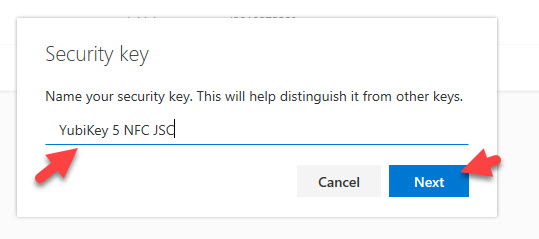
22. Now you will see a confirmation letting you know your FIDO2 security key has been registered with Azure AD!
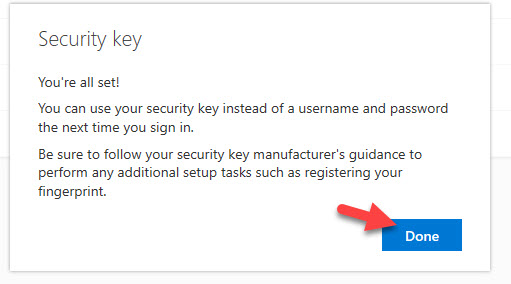
23. Under Security info, you will now see your FIDO2 security listed as one of your authentication methods. Your “Default sign-in method” should be set to “Microsoft Authenticator – notification”. There is no option for “Security key” here so don’t worry about changing this.
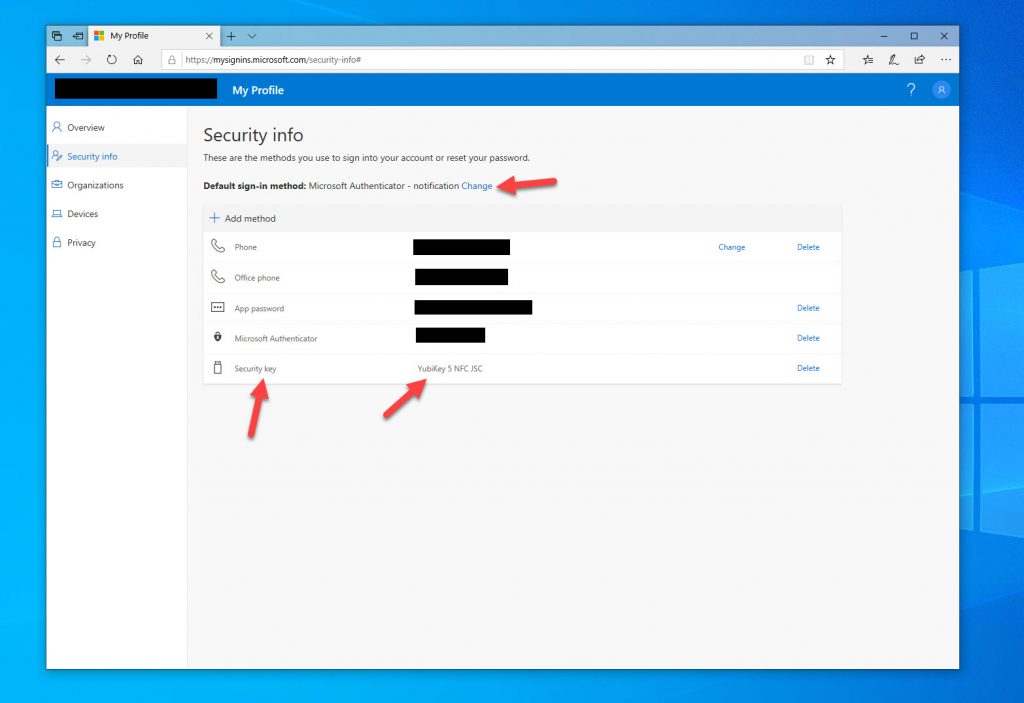
24. You can add as many keys as you wish. If you are using the Feitian BioPass FIDO2 keys with the built-in fingerprint reader, the portal will not prompt the user to read their fingerprint. It will show the same request to create a PIN during the onboarding process in step 18 above which will serve as my local gesture. The fingerprint reader will act as a regular touch-only mechanism just like the YubiKey in my testing. The BioPass won’t rely on fingerprint only anyway and will always require a PIN as part of its setup process. If your fingers are wet, wearing gloves, etc. that PIN is your backup in order for you to get into a system.
Testing your FIDO2 key for password-less login to SaaS apps in the Edge, Firefox, and Chrome web browsers
25. As I mentioned earlier you need one of the following:
- Windows 10 build 1809 or newer for the Edge version it has (but 1903 from May 2019 or newer preferred)
- Firefox version 67 from May 2019 or newer
- Chrome latest versions
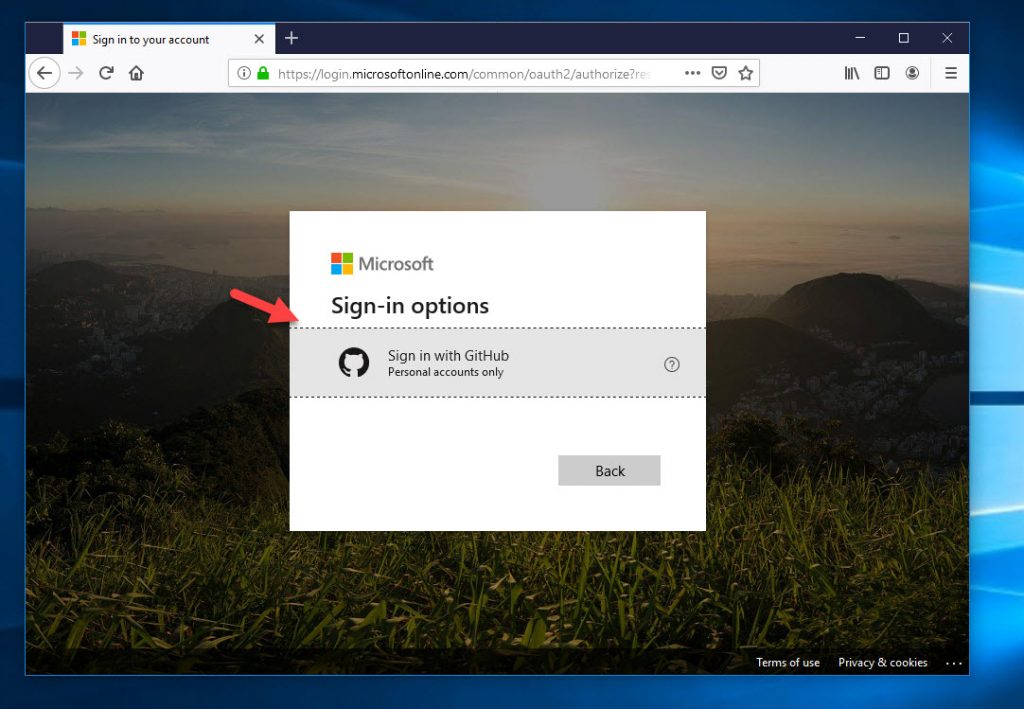
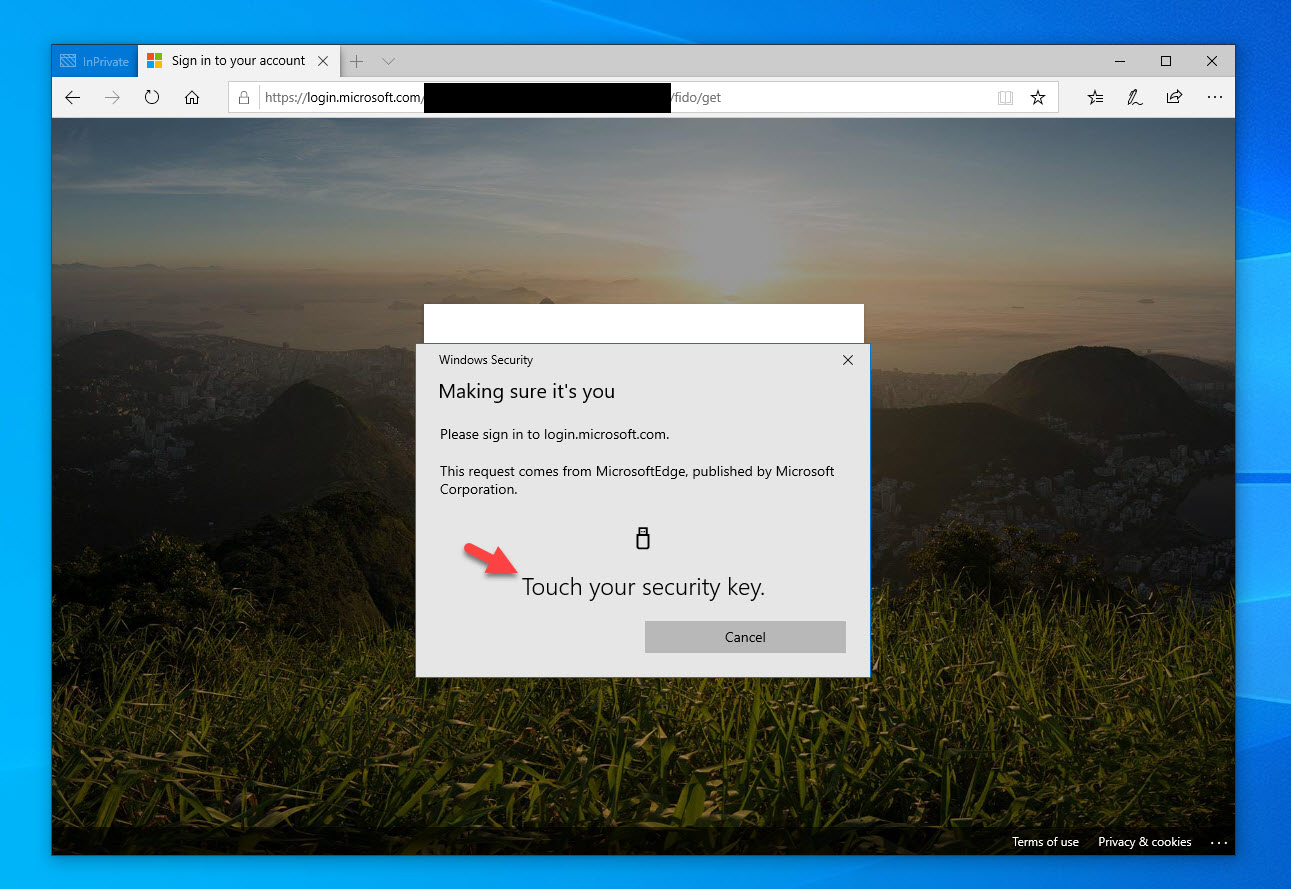
and you’re good to go. I use Azure AD to protect my Citrix Cloud based Workspace before I launch a virtual app or virtual desktop. Here is how the process looks in Edge using a FIDO2 key. Navigate to https://yourcompany.cloud.com which is your Workspace app URL and it will redirect to the IdP which in this case is Azure AD. Don’t put in your email address, instead just click on “Sign-in options”:
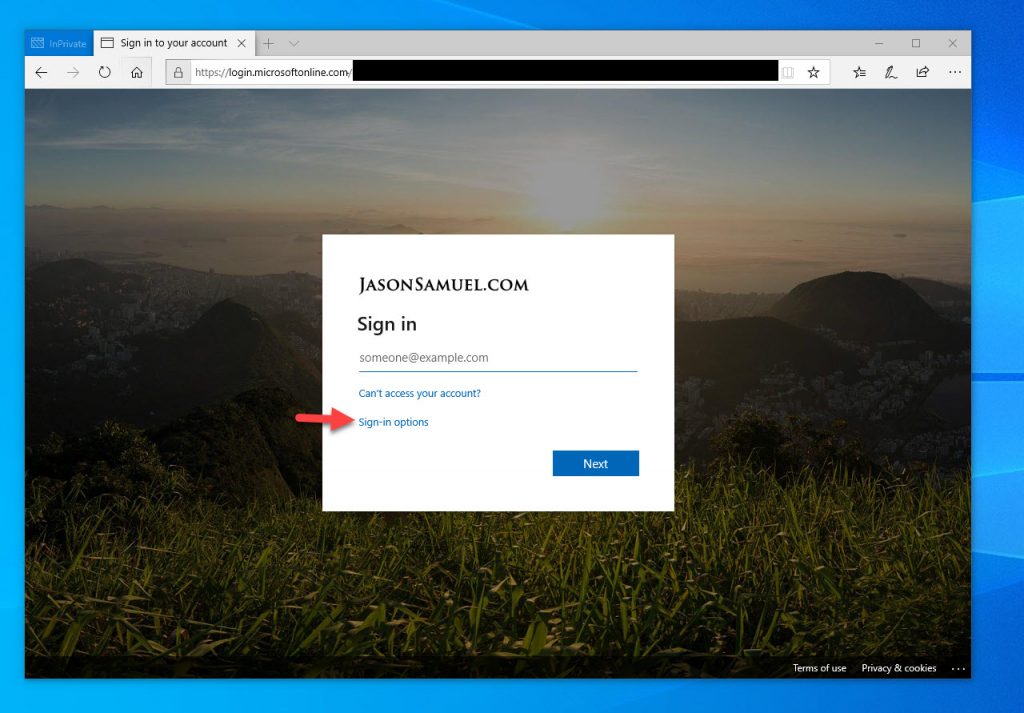
26. See that happy face next to a FIDO2 key, that’s how you should look when you login to your SaaS app without a password for the first time! Go ahead and click “Sign in with a security key”:
27. Now enter your PIN you created for your FIDO2 key:
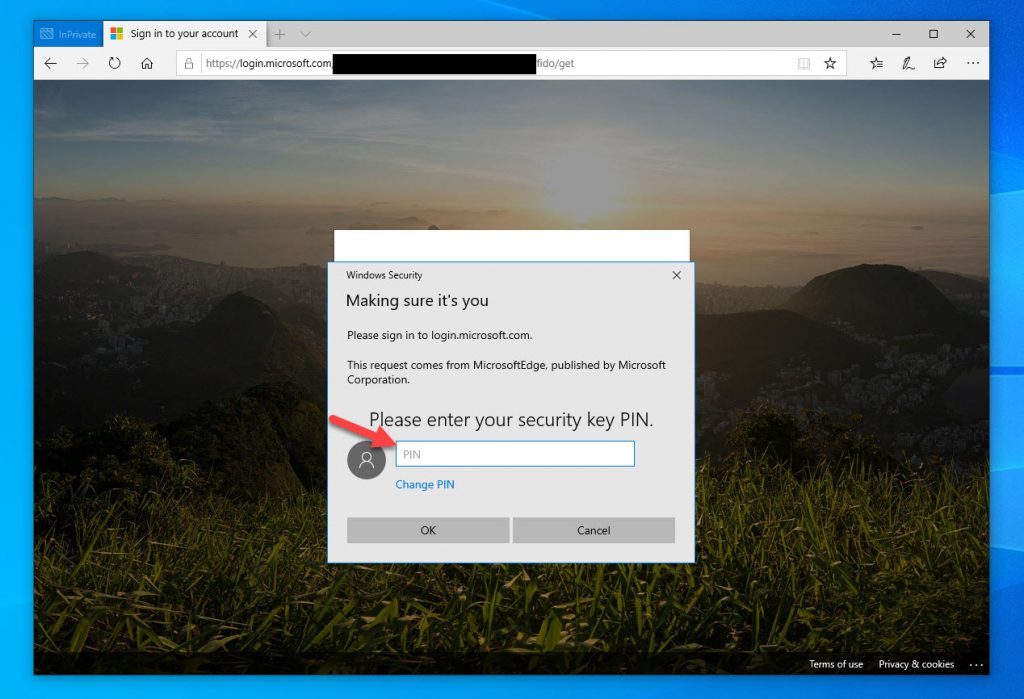
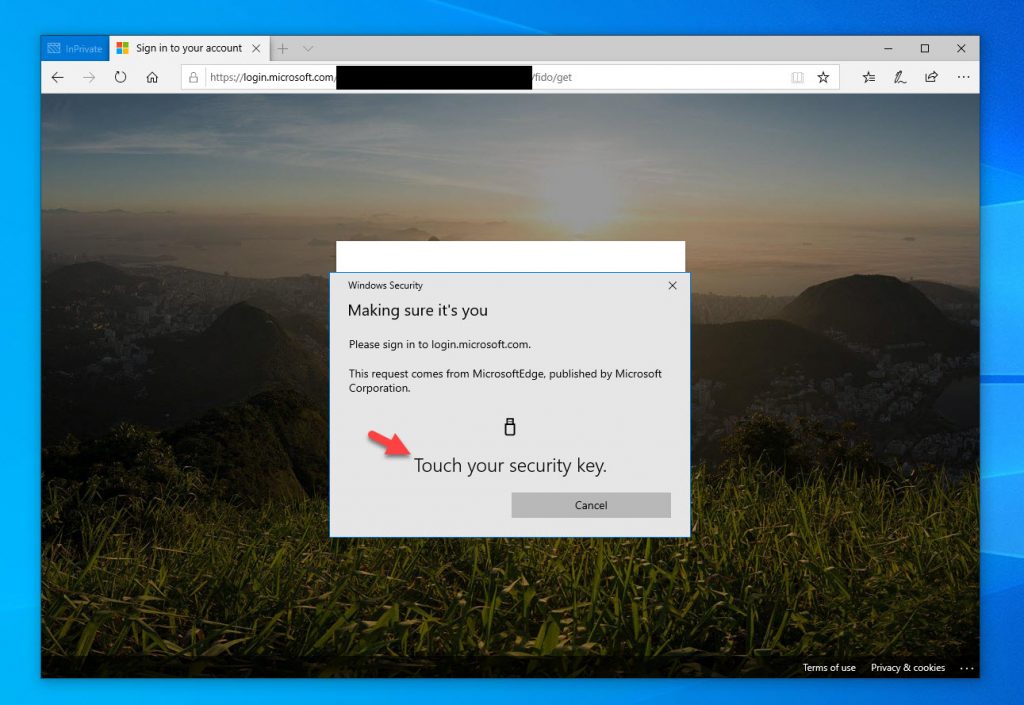
28. Now touch your security key. You have to make sure to do it quickly before it times out on you or you will get kicked back to the PIN page. This is a security measure so you don’t walk away and someone can walk over to your desk and login as you simply by touching your FIDO2 key:
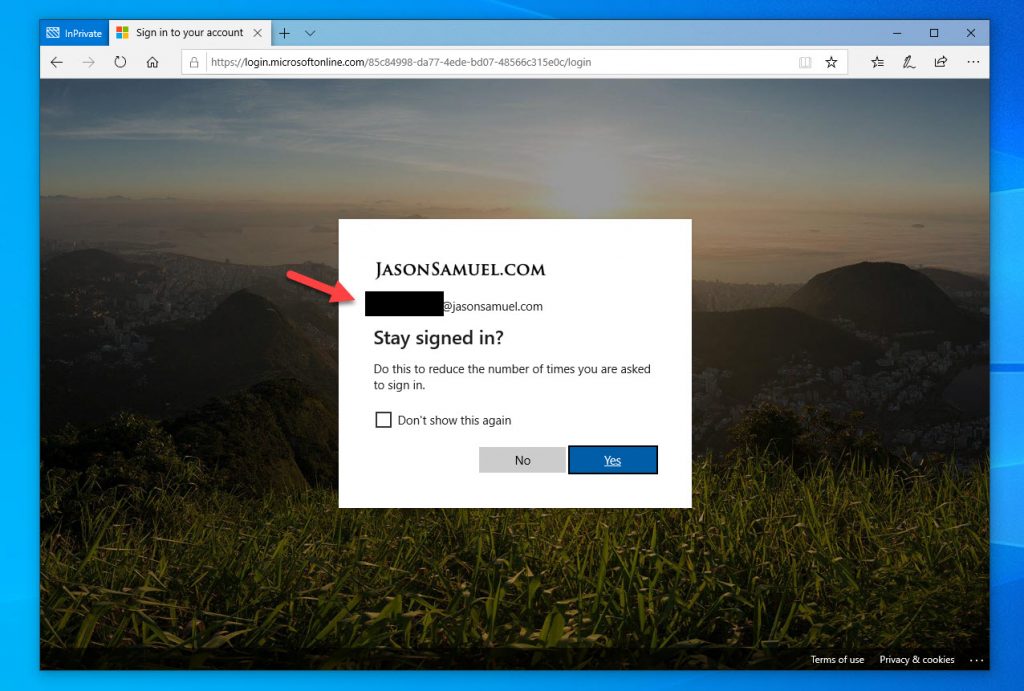
29. Choose to stay signed in or not. Hey look at that, it now sees your email address. That’s the benefit of FIDO2 keys, they know your identity so you don’t have to keep typing in your email address all over the place. It’s both password-less and username-less to a degree. 🙂
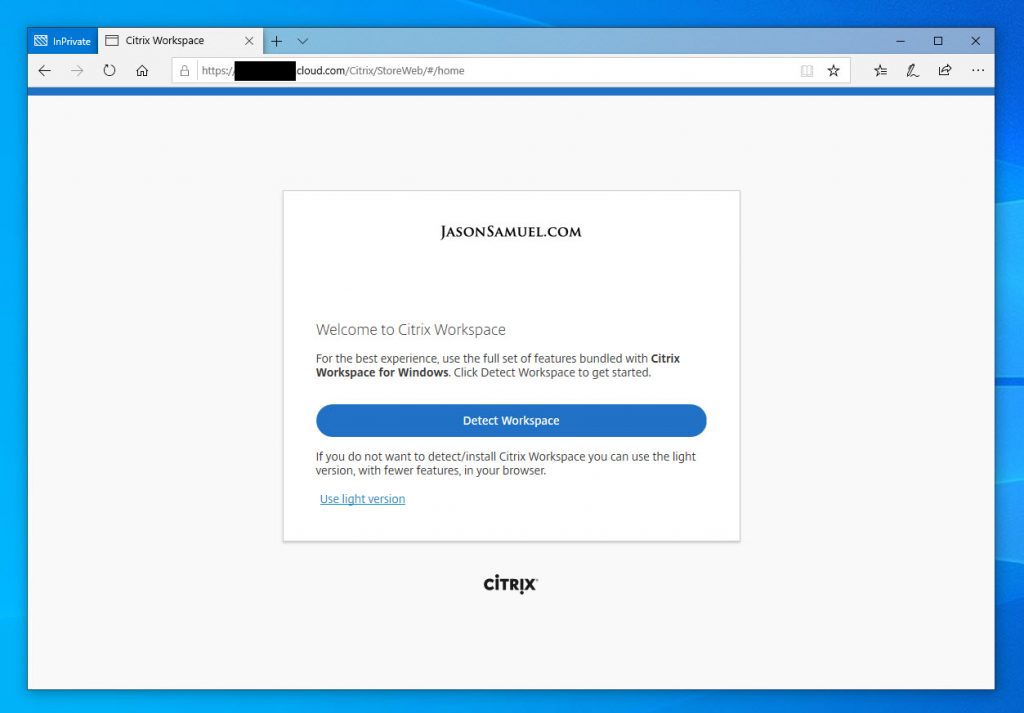
30. Now you will be presented with the Citrix Workspace auto-detect screen (because I’m in InPrivate mode). Just hit Detect Workspace or Use light version so you can use the HTML5 client:
31. And there you go, all your virtual apps, virtual desktops, and any SaaS apps you have wired into Workspace all ready for you to launch. In the case of virtual apps and virtual desktops, these are coming from a Windows OS in your datacenter so you need Citrix FAS to be able to launch and use SSO with them. You can read about how to do that here: How to use Citrix Cloud enabled Federated Authentication Service (FAS) + Microsoft Azure AD + Citrix Workspace for Windows password-less SSO to virtual desktops & apps
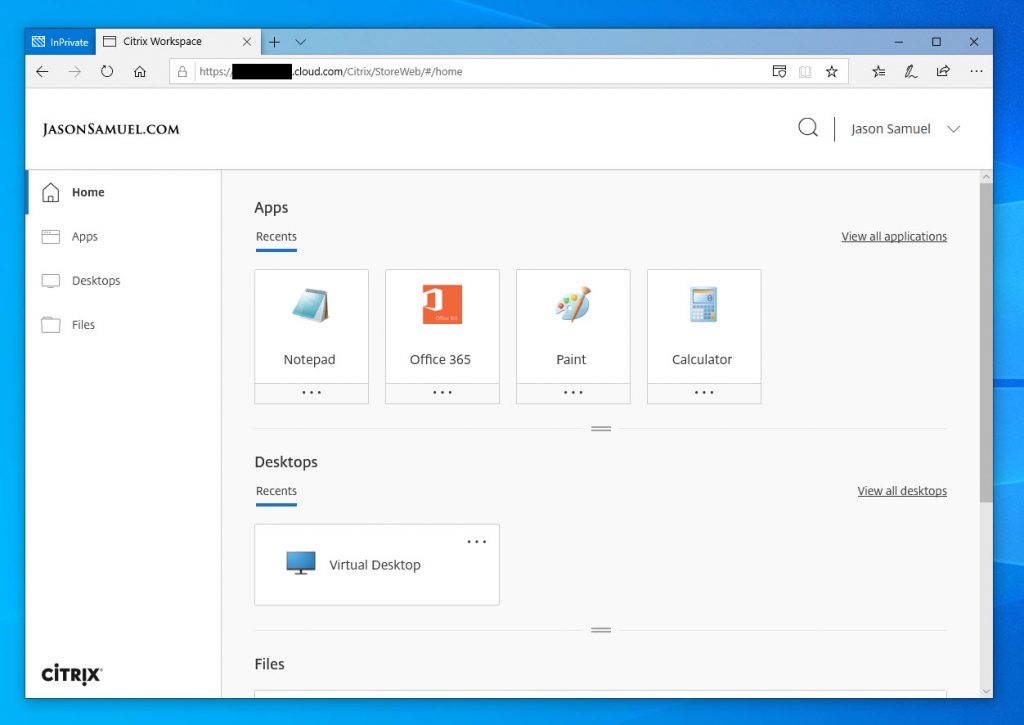
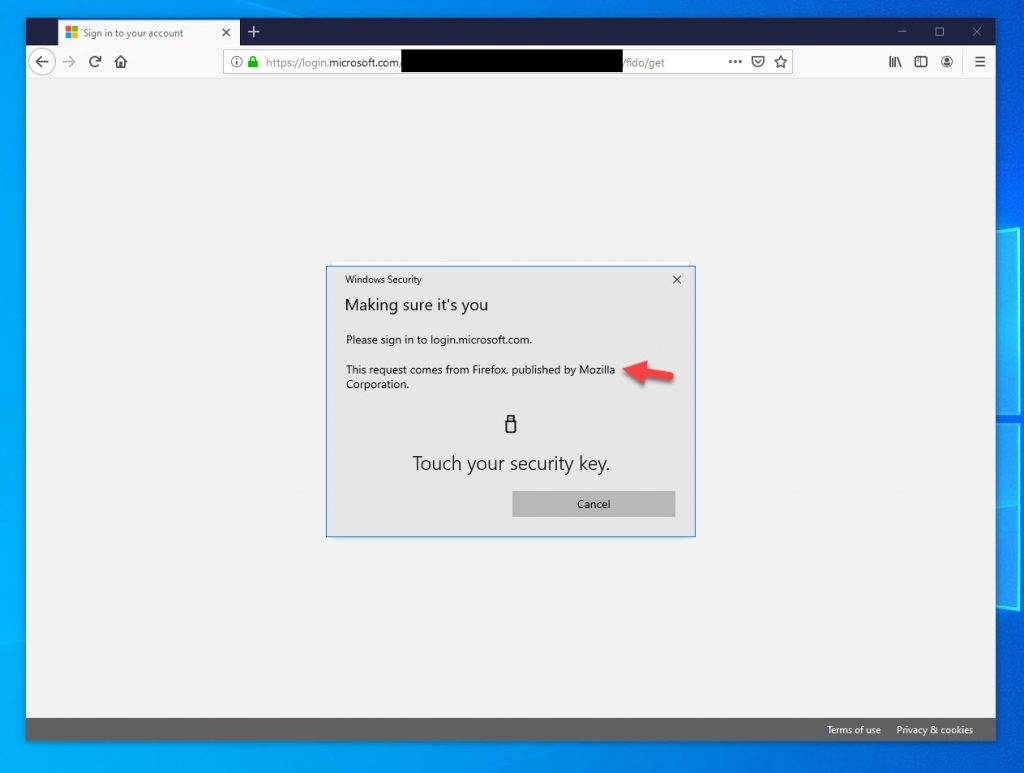
32. In Firefox, the prompts will look slightly different but will function exactly the same (also note it blanks out the Microsoft login background image for some reason):
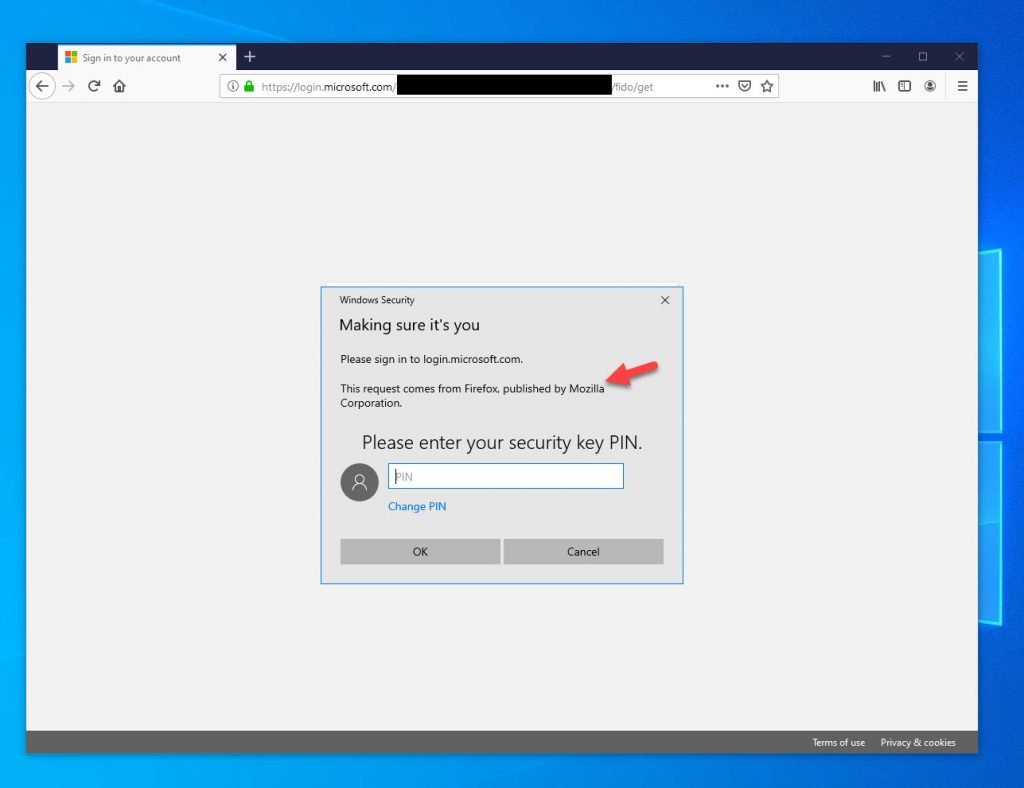
33. In Chrome, the prompts look slightly different as well but will function exactly the same:
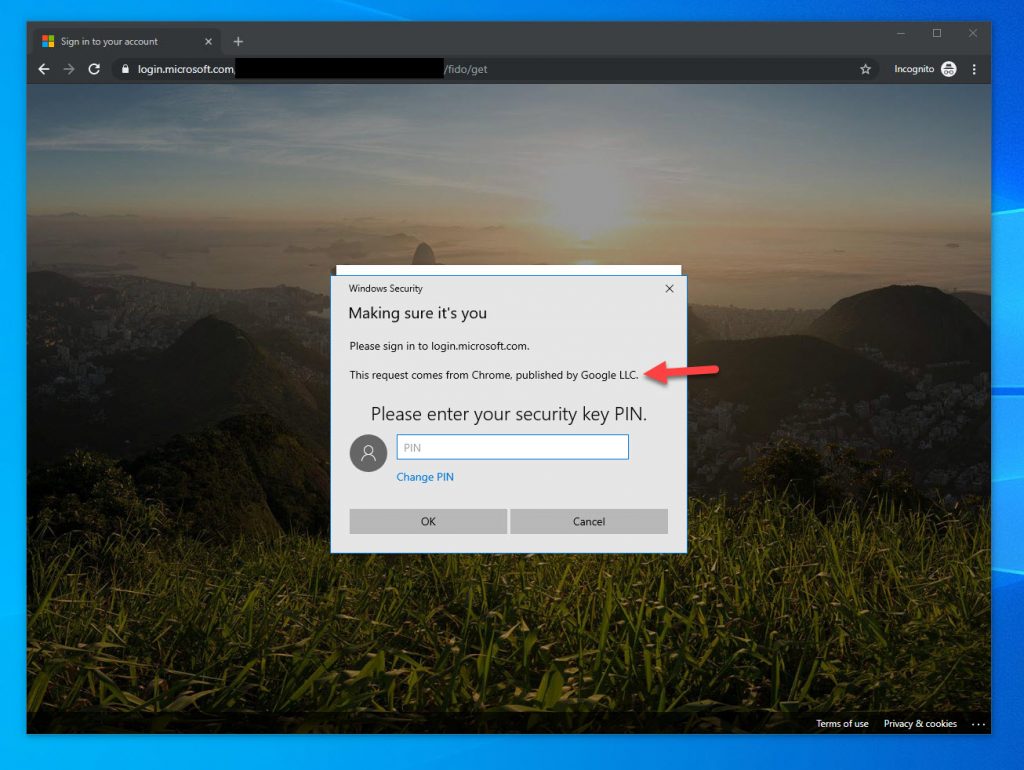
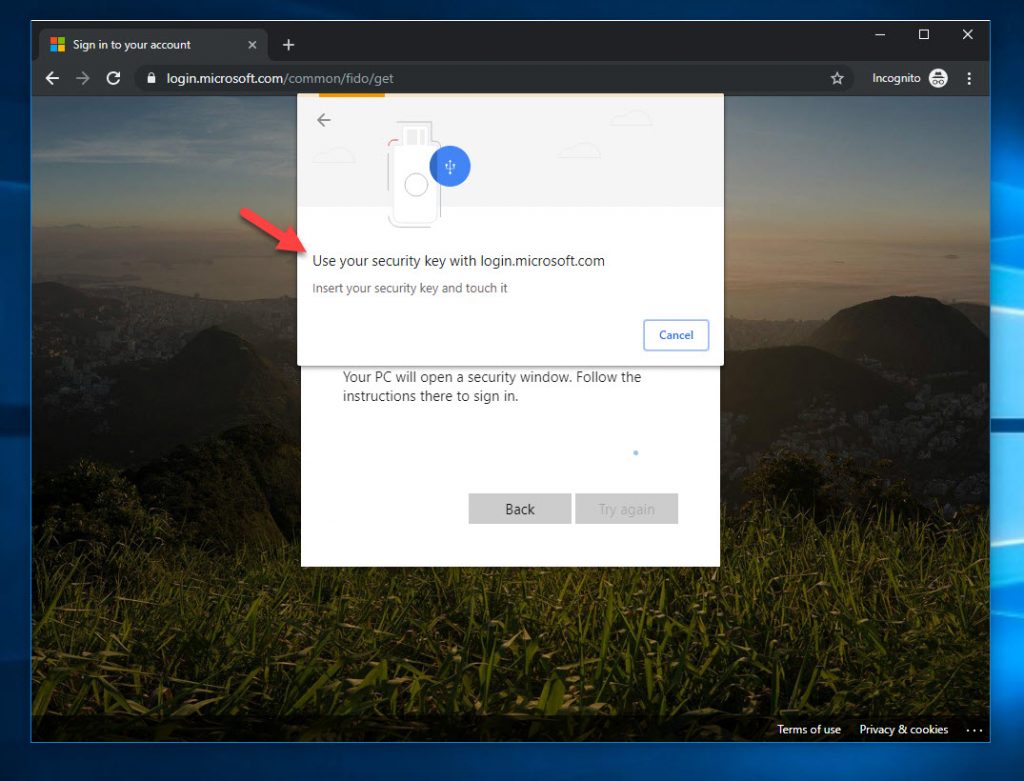
34. If you’re using an older Windows 10 build such as 1803 for example, then the Chrome prompts look very different:
35. If you try Windows 10 1803 with the latest Firefox 69, it won’t give you the FIDO2 option. So your best bet with old versions of Windows 10 is to use Chrome for now. I’m sure Firefox will come up with some code that will have the capability at some point and we’ll see the security key option here:
Testing your FIDO2 security key with Windows 10 logins
You can log in to Windows 10 at the lock screen using your FIDO2 security key but only if it is Azure AD Joined at this time. Hybrid Azure AD Join is not supported right now but I’m sure will be at some point closer to GA release. Most all the computers on my network are Hybrid Azure AD Joined so I’m anxiously awaiting this capability.
On your Windows 10 build 1809 or newer system (preferably 1903 or newer because it adds additional features), you have the capability to use FIDO2 but it requires you to do one of the following:
- Use Intune to enable the credential provider on the Windows 10 lock screen. Meaning you push the capability to login this way from your Azure tenant to your devices. You can do it for all devices or target specific devices using Intune device configuration profiles.
- For non-Intune managed devices, use a provisioning package using the Windows Configuration Designer app
- FIDO 2 security keys ARE NOT a controlled substance, but they will blow your mind and are addicting. Habitual use of FIDO2 security keys is actually good for you!
- If you see anyone actually ingest a FIDO2 security key, you should probably call an ambulance immediately.
- If we can somehow tie authentication to exercise, we would encourage better workplace health for our employees! Should stretching be mandatory before authenticating? I’m liking the idea of wearable FIDO2 authentication devices that track both health and authentication and force you to perform a few physical actions every now and then.
- If FIDO2 security keys WERE actually a controlled substance, this is that one moment where their pharmaceutical properties may actually be advantageous.
- The human body probably isn’t designed to contour for extreme sport FIDO2 authentication. I need to bring my desktop’s USB port closer to me!
There is another method using manual changes to the registry to enable the FIDO2 credential provider on the lock screen as well in a pinch but I’m not sure if that will be used in GA so I won’t list it with the above options.
Once you complete this, you will then see the security key icon under Sign-in options on the lock screen:
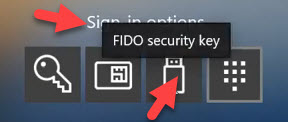
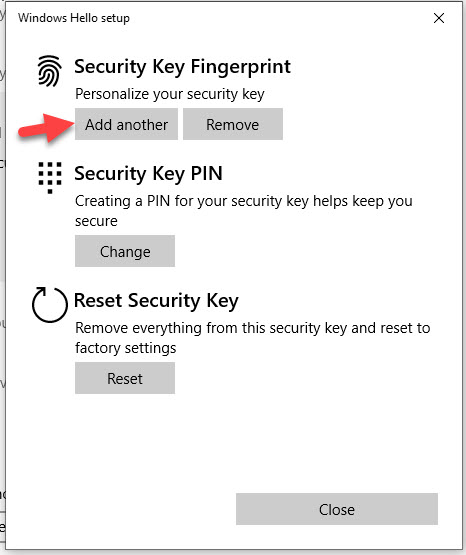
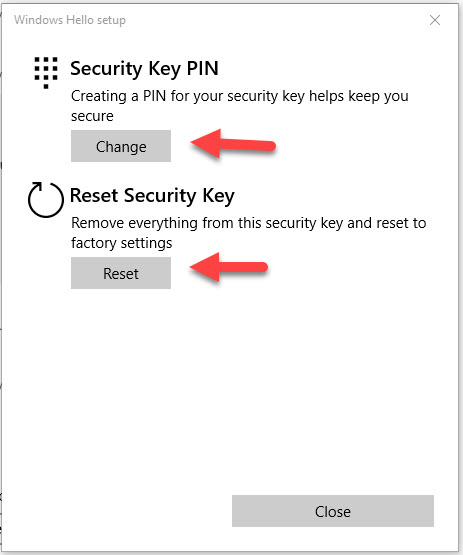
Users can manage the security key PIN or biometric from within Windows 10 itself. On Windows 10 1903 and newer they can go under Windows Settings > Accounts > Sign-in options > Security Key and will see this option to manage their PIN, biometric, or even completely reset the FIDO2 security key:
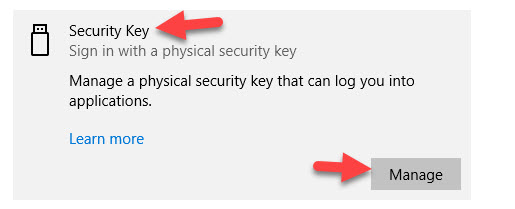
Feitian BioPass example (it has the built-in fingerprint reader):
and you can add as many fingers as you like:
I had to set up a Windows 10 device from scratch to do my Azure AD Join only testing with FIDO2 since everything else on my network was Hybrid Azure AD Joined. At this time, I am not going to do a detailed walkthrough guide on setting this up as I feel like it’s going to probably change closer to GA with more capability and administration options I would like to cover in more detail. It will require a bit of a deeper dive into Intune and Windows 10 device management strategy so best served as a separate guide.
Hidden dangers of using FIDO2 security keys
FIDO2 security keys can get you arrested!
So I tend to get a little excited about new technology and want to share it with people. 🙂 When you go to IT conferences and see your friends you haven’t seen in awhile in-person it’s natural to get excited. From a distance, you may think shouting “Hey! I got something that will change your world!” and pull out a small plastic pill bag from your backpack shaking it in the air like a winning lottery ticket is okay. That’s just a natural human reaction when you’re excited about something after all.
Unfortunately, context is everything, and when this happens in earshot of Event Security you may get some odd looks and possible questions. Do yourself a favor and get a keyring when carrying multiple FIDO2 security keys. Pill pouches are not a good idea.
I also would like to share some of the advice I gave to Event Security while explaining how FIDO2 security keys work:
And just in case you ever find yourself in a predicament over your FIDO2 security key usage and need some proof they are legal, I’m going to leave this right here for you:
FIDO2 security keys can cause bodily injury!
Many of you know how I like to keep my work area. No clutter and no visible wires if at all possible! Which means my desktop is actually behind my desk and mounted off the ground to the desk itself. All that is visible is monitors, keyboard and mouse. FIDO2 security keys being mostly USB based, this poses a challenge as I have to run around in circles around the tight space in between my desk to get to the desktop with the FIDO2 security key sticking out of it and run out the other side to authenticate before the prompt times out on me. Authenticating was starting to feel like driving around in a circle on a NASCAR track at full speed!

After a few days of the increased cardio, I got the bright idea if I just kind of leaned/laid over my desk and reached really hard I could hit the touch sensor and authenticate on the key without all the sprinting.
While I laid on the ground of my office from whatever that sharp pain emanating from my lower back was, I suddenly had a few epiphanies:
An ice pack and an Amazon Prime delivery later, I had something that fits my “no clutter on the desk” needs while preventing FIDO2 related injury. A simple AmazonBasics USB 3.0 extension cable for $8.99 run through my desk’s cable management channels and then 3M double-sided taped to the side of my monitor allows me to use FIDO2 security keys without risk of future injuries! So if you’re ever in the same boat as me, either remember to do some warm-up stretches before authenticating or invest in a nice long USB extender. That Bluetooth (BLE) FIDO2 key from Feitian I mentioned earlier may also be an option for you.
Final Thoughts
I hope this guide has given you a bit of insight into the power of FIDO2 security keys with Azure AD. These should be part of your password-less strategy and will protect Windows 10, SaaS web apps, virtual apps, and virtual desktops as you have seen in my examples above. The technology is new but has immense enterprise backing and gets so many improvements every month, I have a hard time even tracking all the progress! I highly encourage your organization (or just you yourself at a personal level) to go out and buy a FIDO2 compatible security key and see what all the buzz is about. You’ll quickly see this will be part of the future of password-less computing. If you have any questions or comments please leave them below.






Johan Lundberg
October 9, 2019 at 11:48 PM
Hi Jason,
Great article. I got it working on a Mac with security keys too, but was denied when trying to authenticate through a Chrome browser on an Android phone. Did not even work from the Edge browser on Android. Have you tried authenticating on Android or is Microsoft limiting this functionality to desktop browsers only? Have you tried or know of anyone building a native Fido2 authentication client for Android (https://developers.google.com/identity/fido/android/native-apps) to authenticate against Azure AD?
Jason Samuel
October 10, 2019 at 9:30 AM
Thanks Johan. I do not have any Android devices so have not tested it. Android 7.0+ (Nougat onward) is FIDO2 Certified so I’m sure there is a way to make it work. Your Android phone itself can be a FIDO2 security key as of a few months ago (but can only be used with Google services for now): https://fidoalliance.org/news-your-google-android-7-phone-is-now-a-fido2-security-key/
Jeff Brixhamite
November 27, 2019 at 5:38 AM
Hi Jason,
Not all Fido keys can communicate with all android phones. If the key and phone have NFC capability and it is enabled that may be one solution, otherwise the key would need to have a compatible USB connection.