Citrix released Public Tech Preview for the new Active Directory + One Time Password based Multi-Factor Authentication solution in Citrix Workspace on Friday, March 22, 2019. For those of you who read my “A closer look at Citrix Workspace and Gateway Service in Citrix Cloud for companies moving off of on-premises StoreFront and NetScaler Gateway”, you may have seen this capability was in development. It is now available for everyone to begin testing and I wanted to do a quick walkthrough for you on how to set it up.
This native MFA capability of Citrix Workspace is big news for some companies. Previously the only way you could use MFA with Citrix Workspace was through Azure AD. This meant Azure MFA in most cases. You could also federate from Azure AD to other IdPs (identity providers) like Okta for MFA if you wished. This new capability is important for a few reasons:
- Companies who don’t have an existing investment in an MFA solution have one instantly now.
- There is no infrastructure required, it is fully cloud-based and talks to your AD via the Cloud Connectors.
- It is built upon RFC 6238. The Time-Based One-Time Password (TOTP) Algorithm is an industry standard.
- It has a self-service onboarding mechanism for your users. You don’t have to pre-enroll users.
How to set it up
Setup is very simple, let’s dive into it:
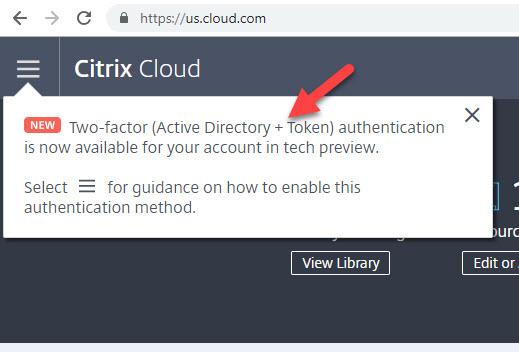
1. When you log into your Citrix Cloud console now, you will see a notification about the Active Directory + Token option like this:
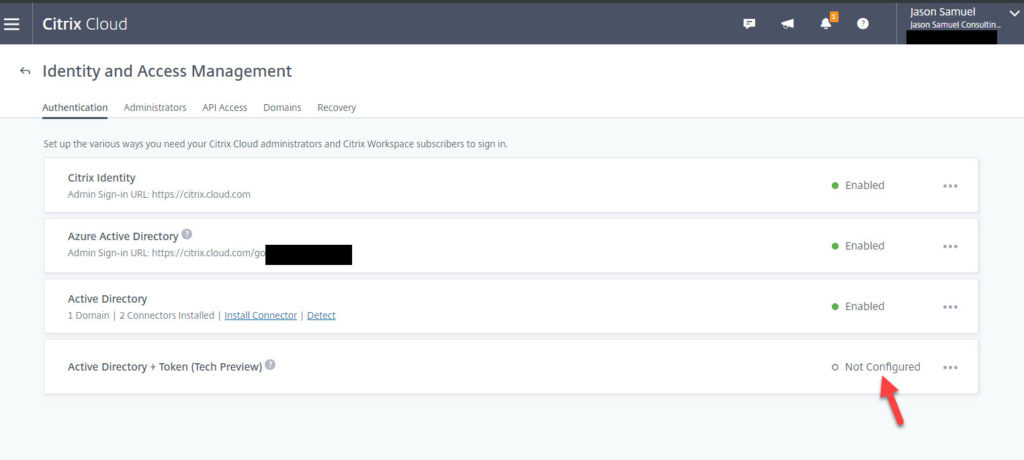
2. When you go to Identity and Access Management, you will see it as an available option to turn on:
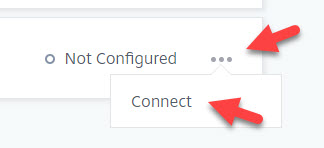
3. Click on the ellipsis (3 dots) next to Not Configured and click Connect:
4. If you already have Cloud Connectors installed, the Connect to Active Directory portion will have a green check mark like this already. You will notice that in the second step it says “Single Device Enabled – Workspace subscribers may enroll one device”. Just hit Save and Finish.
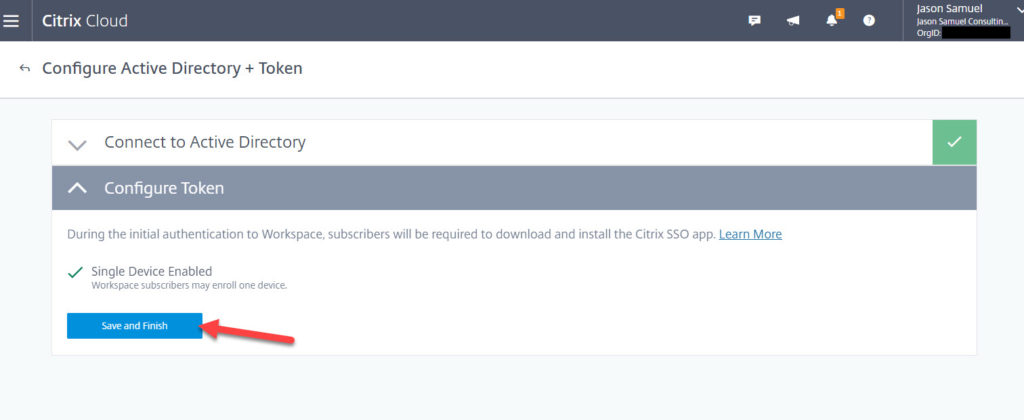
5. At this point, you will see a green banner saying “Active Directory + Token was successfully enabled” and there will be a green Enabled dot next to the option.
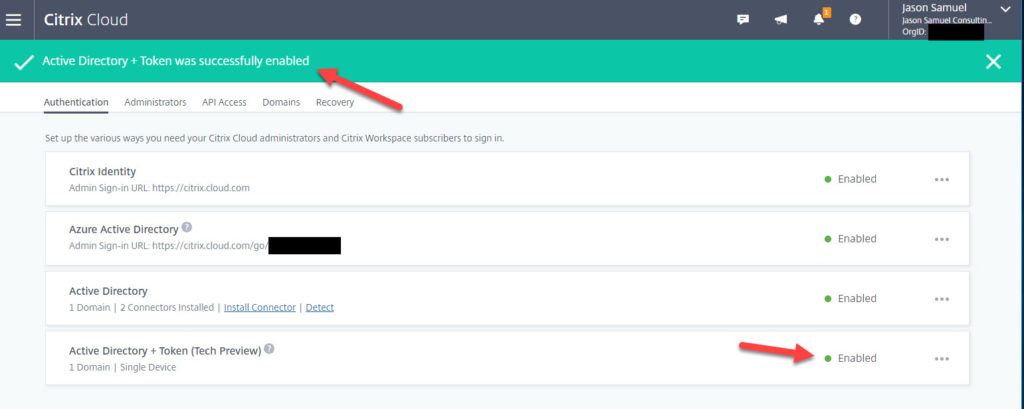
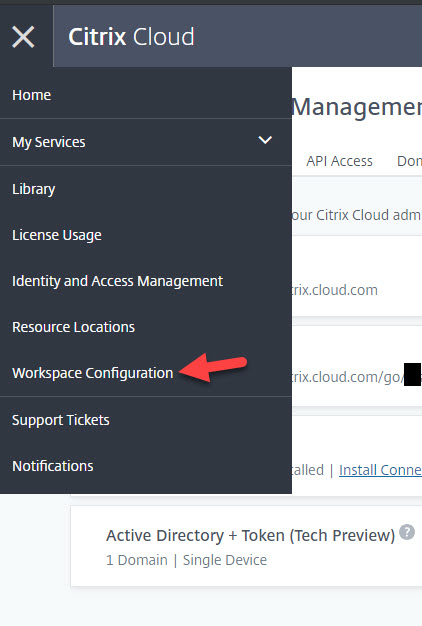
6. Now you need to enable it for use on your Workspace. Go to Workspace Configuration:
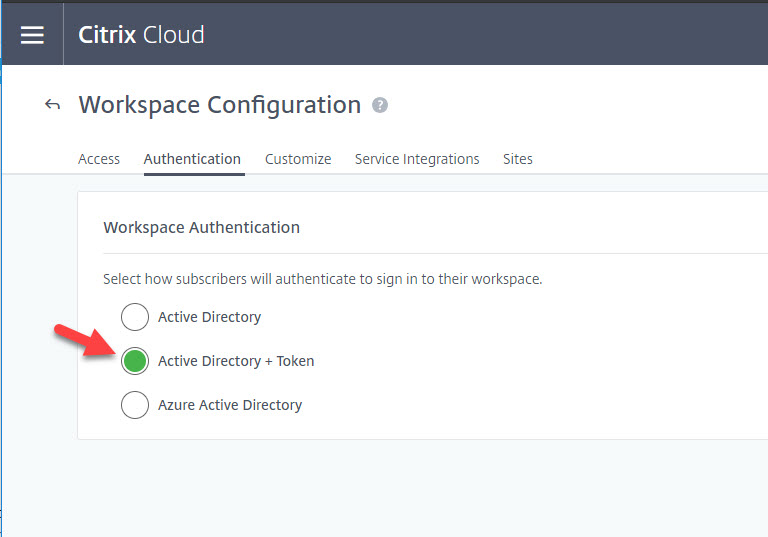
7. I have been using Azure Active Directory. You should now see an option called Active Directory + Token here. Go ahead and click on it:
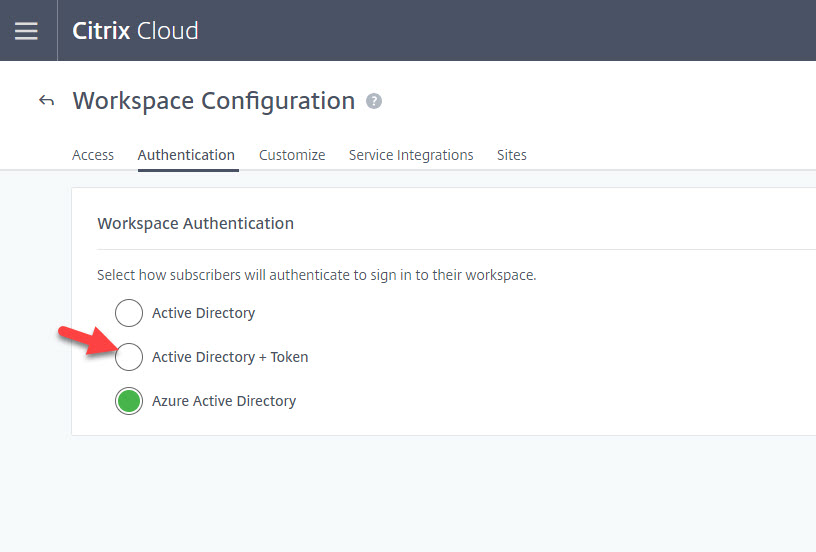
8. Check the disclaimer and hit Confirm:
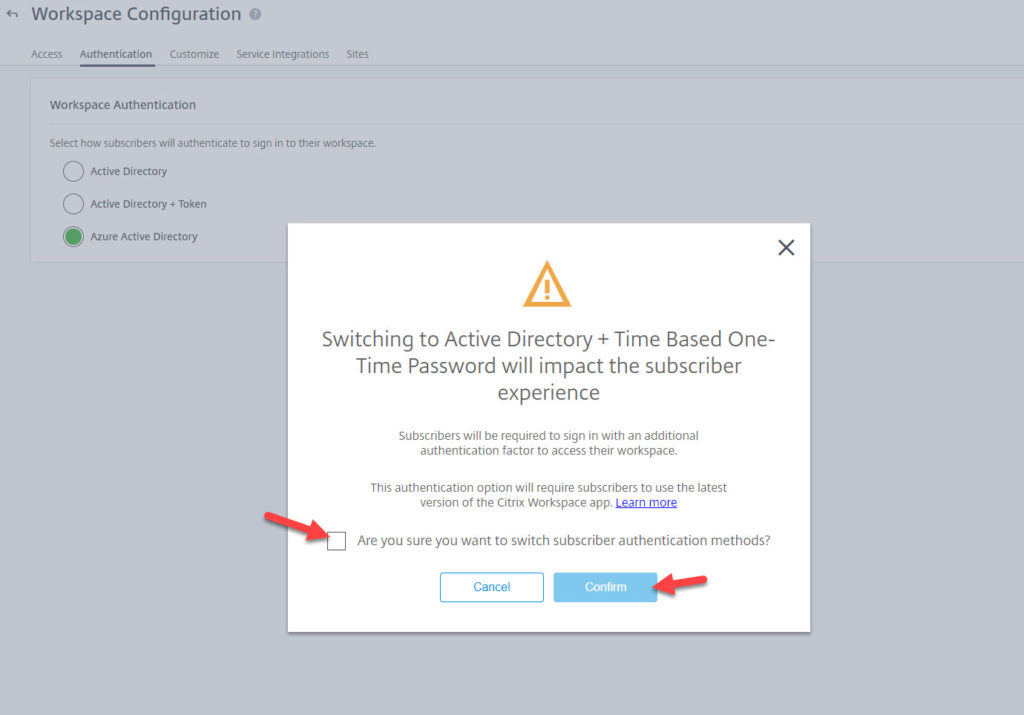
9. Now you should see it has been selected and is green:
10. It will take about 2-3 minutes for Workspace to re-configure itself. If users attempt to hit Workspace during this authentication change time they will get a message saying “You cannot log on at this time”. For this reason, I suggest making this change at a time when user traffic for new launches is low (like around lunch time).

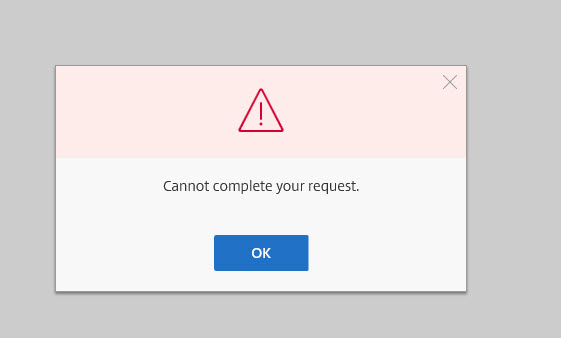
You may also see a message like this saying “Cannot complete your request” during this waiting period if you keep refreshing, it is in the process of reconfiguring the authentication method so just keep waiting a little bit longer:
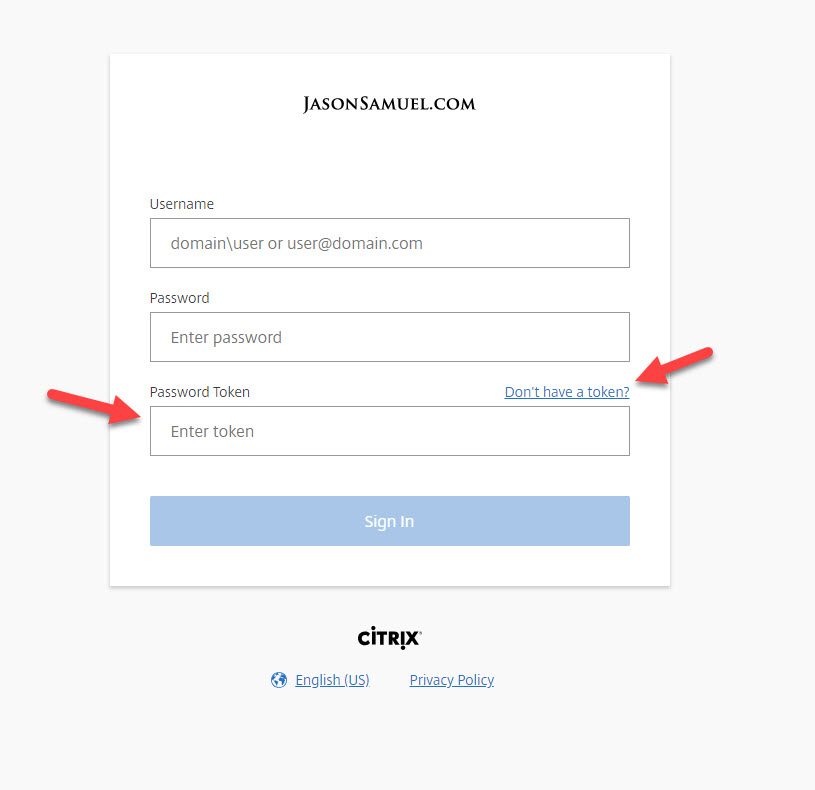
11. After those few minutes the new login screen will look like this. There will be a field for them to enter their Password Token as well as a “Don’t have a token?” link for them to onboard themselves. Note, users can also use this link to re-enroll later if they buy a new device and I have tested this capability successfully already using another device:

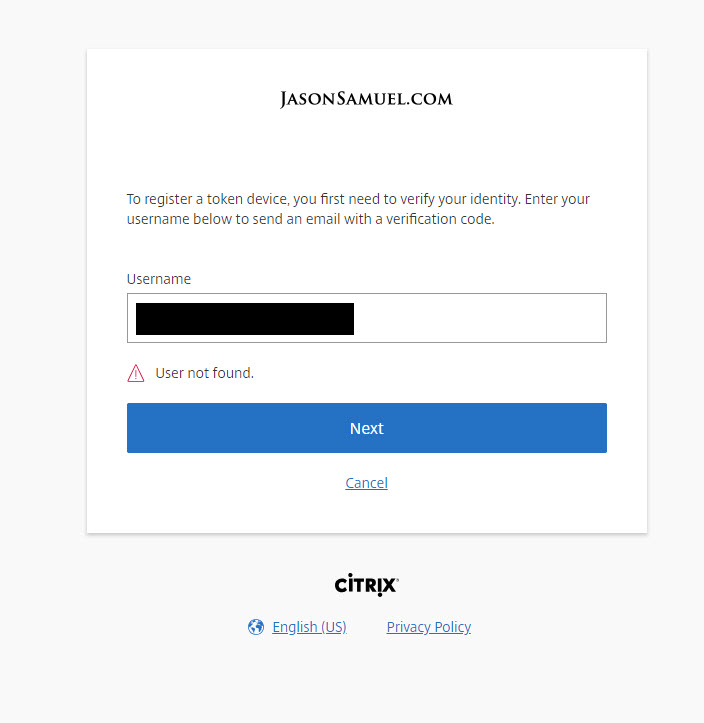
12. After clicking the onboarding link, I am asked to enter my user name from AD or my company email address so I can get a registration link via email:
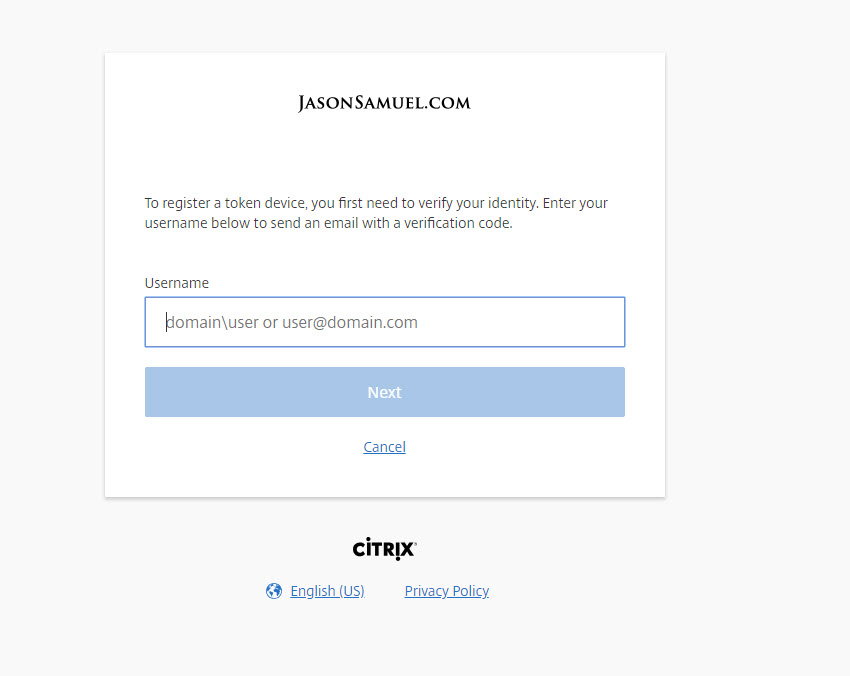
Note, the user cannot just enter a random email address here. It must be the one set in Active Directory for that user. Example, if you type in a Gmail account here you will be presented with this message saying “User not found”:
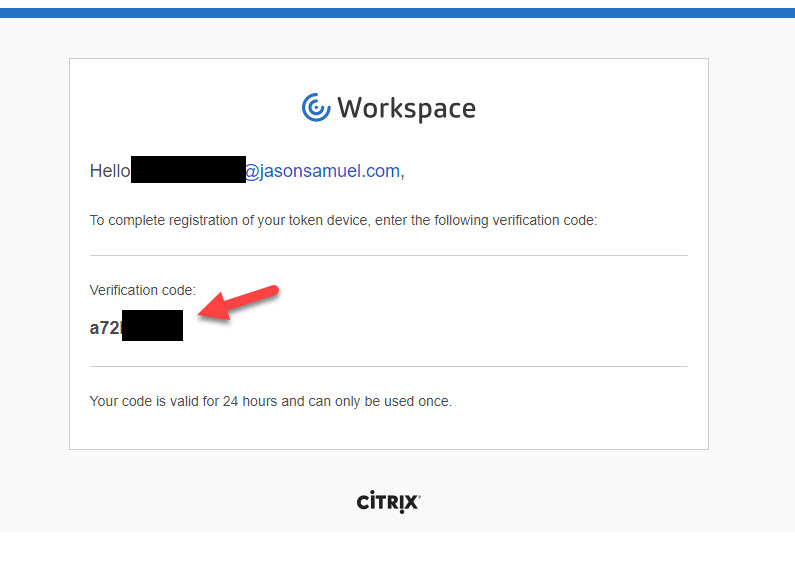
13. The user will get an email like this to “Complete Your Device Registration” as the subject line will say. The verification code is only valid for 24 hours. At this time I have noticed that the email has a default Workspace logo along the top but as this feature goes GA (generally available) I suspect the email will follow your company’s Workspace branding settings. Go ahead and copy the verification code from the email:
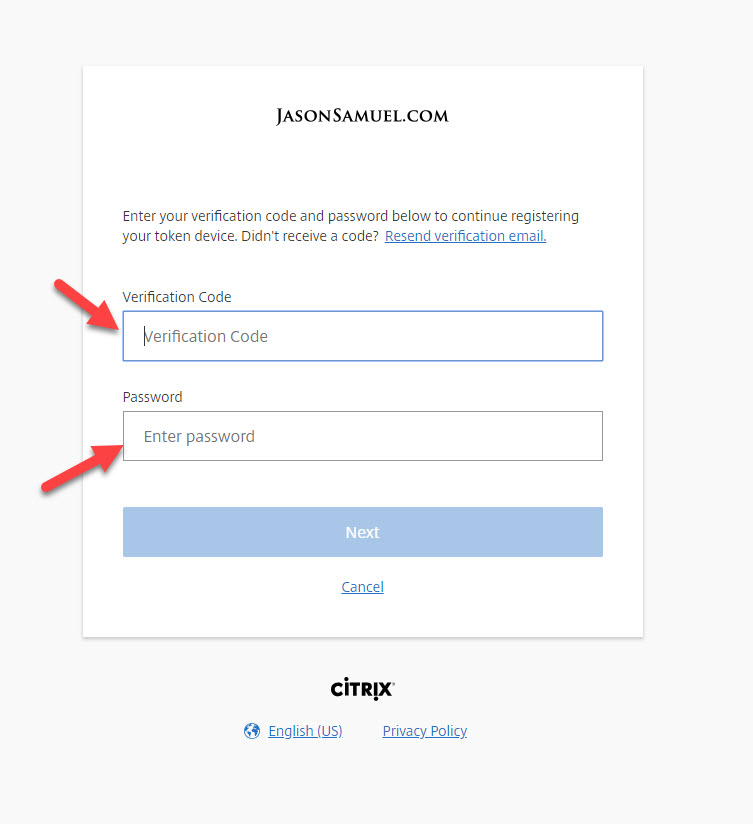
14. If you go back to the Workspace login page you will see this:
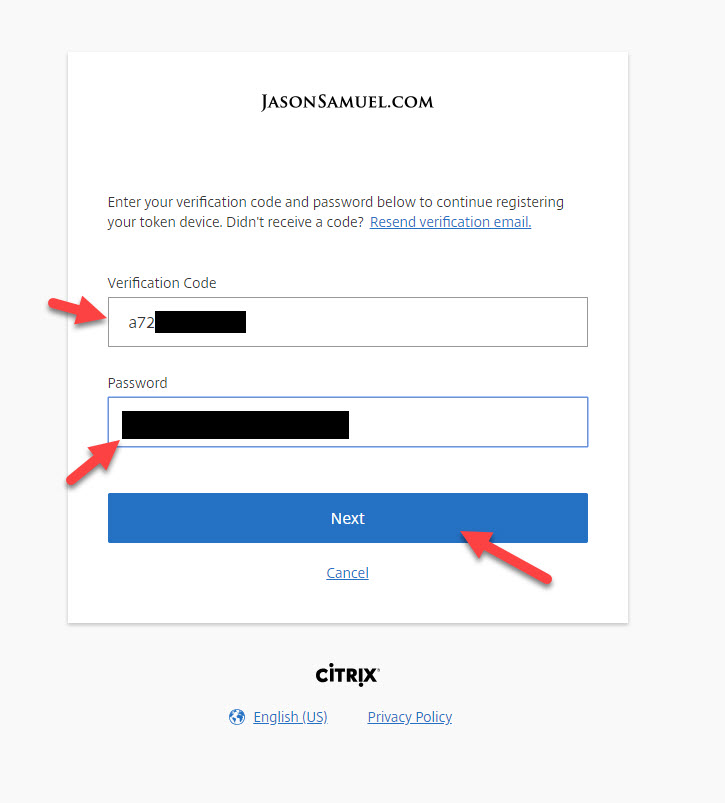
15. Go ahead and copy and paste the verification code and enter your password:
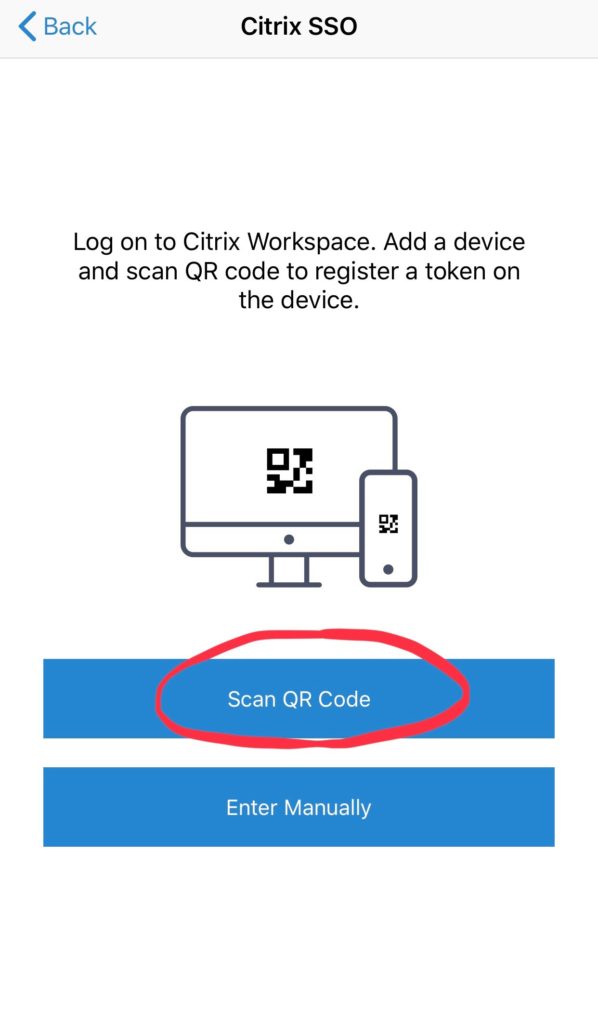
16. On the next screen, your users will be asked to scan the QR code shown on the screen with their phone. They can use the Citrix SSO app, Microsoft Authenticator, Google Authenticator, Okta Verify, Authy, etc. here since they all follow the same RFC for TOTP. There is no benefit in using the Citrix SSO app over the others right now. There is no push authentication mechanism capability so there is nothing proprietary with this solution that is locking you into the Citrix SSO app. You can tell your users to use whichever authenticator app your company recommends.
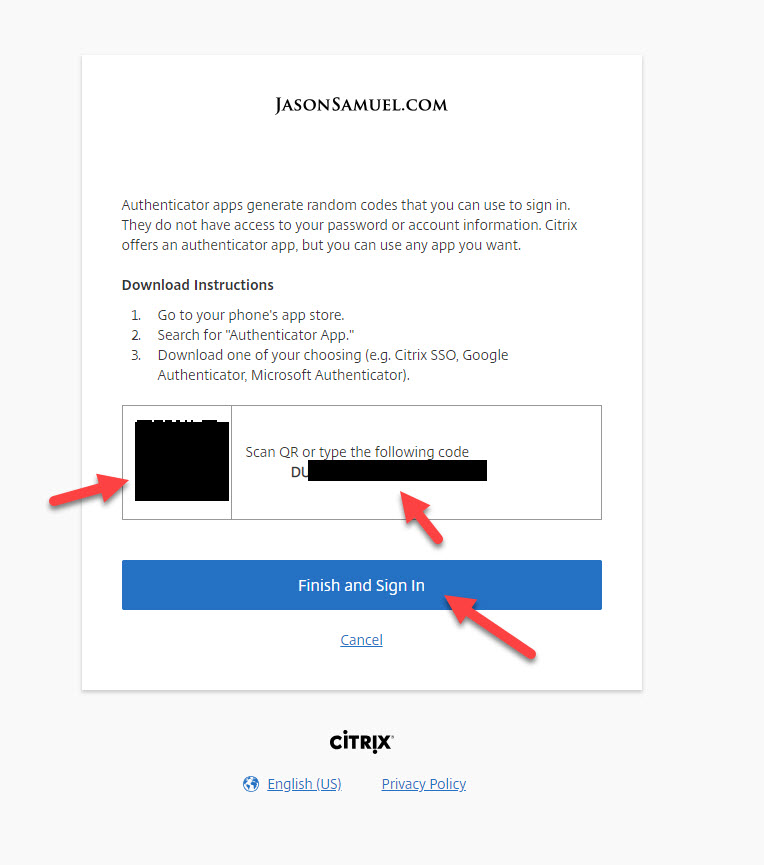
The Citrix SSO app for example:
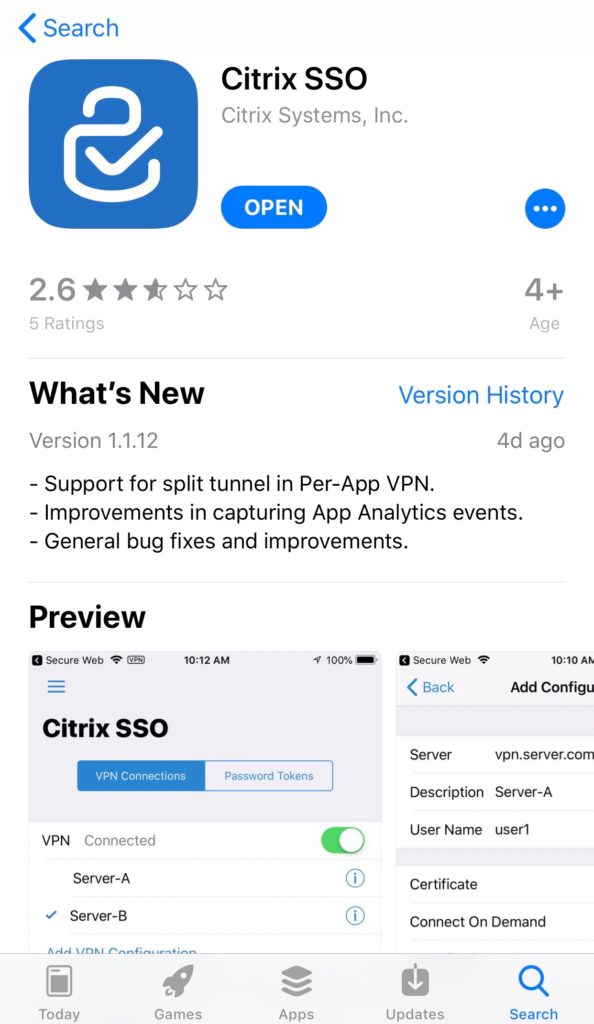
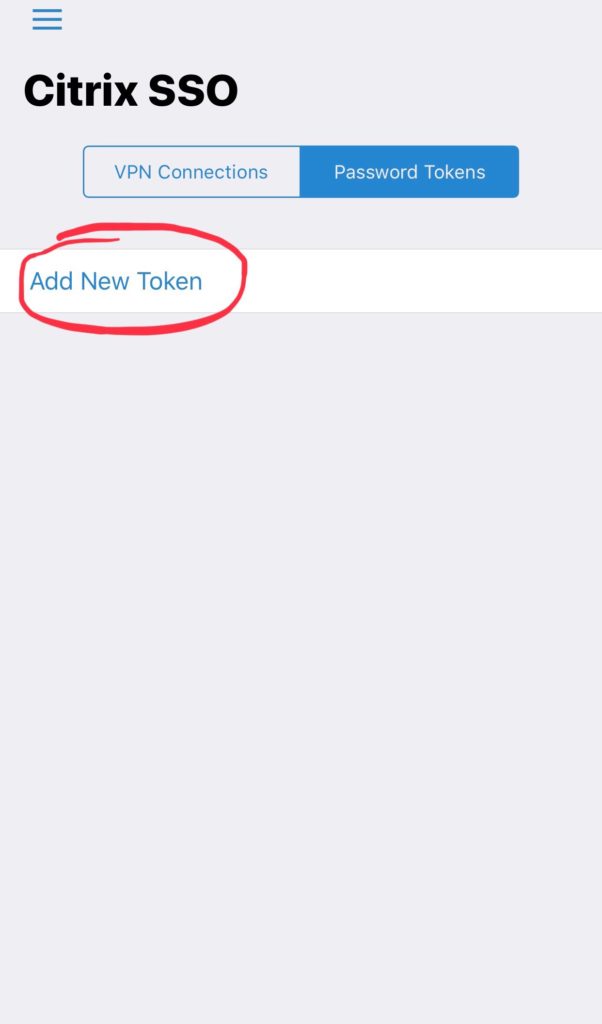
Install it and use the Add New Token option:
30-second countdown TOTP token:
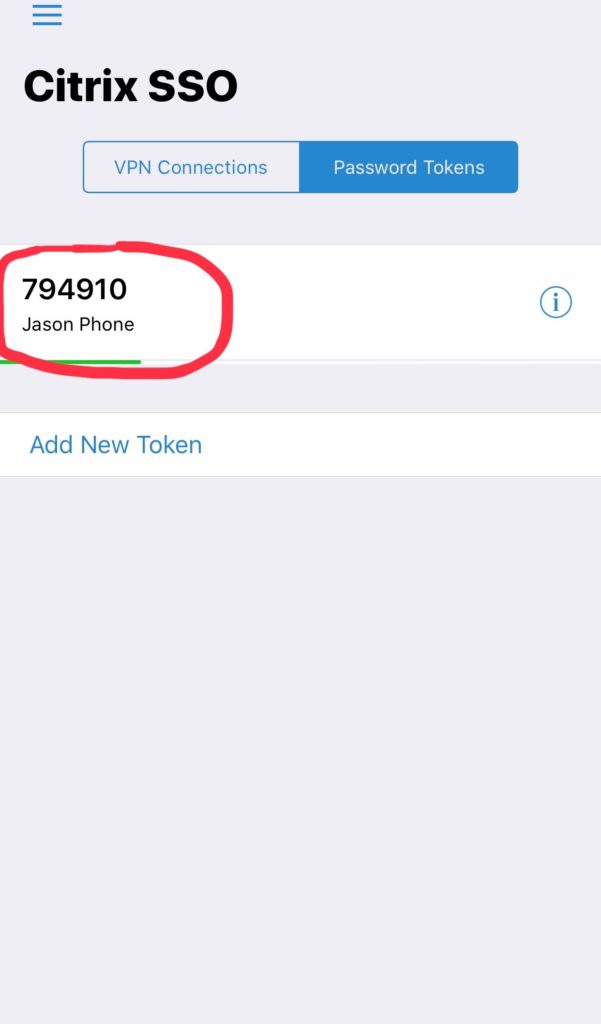
I have currently tested the solution with all the above Authenticators I mentioned and it works just fine. The users will see a new TOTP code every 30 seconds.
17. Immediately after scanning and verifying the TOTP code, you will be logged out of the onboarding session and get a message like this:
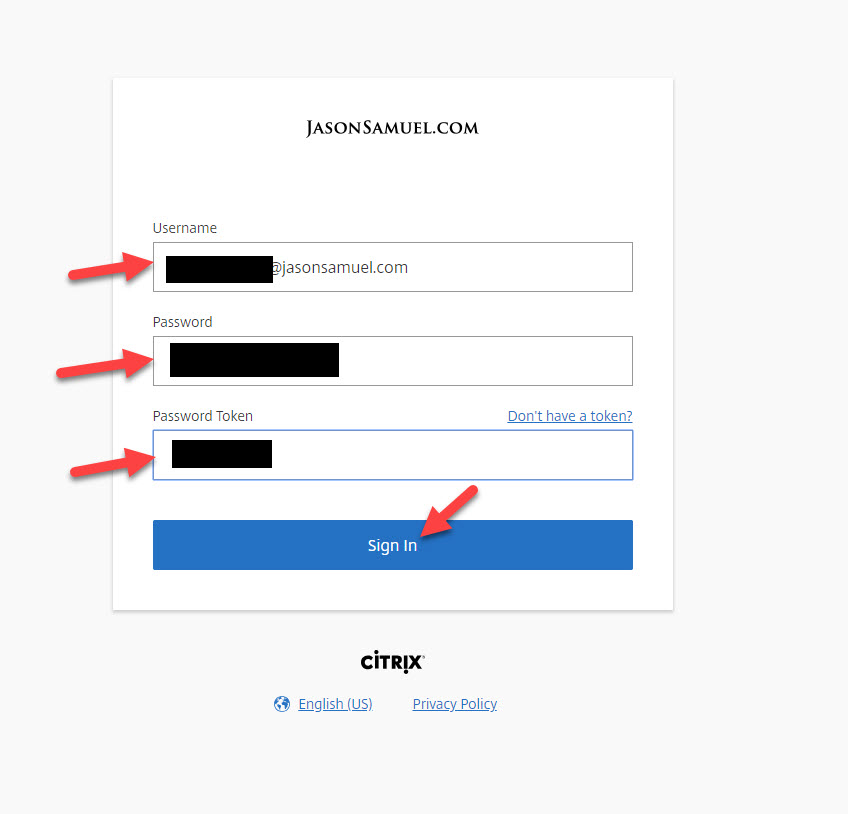
18. Now go ahead and log back in but this time using the TOTP code in your app:
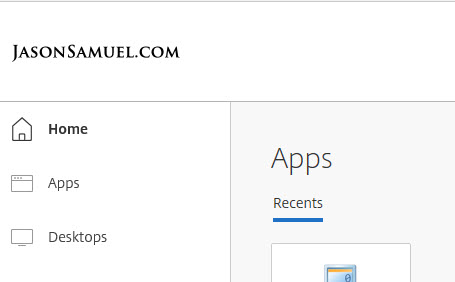
19. At that’s it! You’re logged in and will be presented with your Workspace:
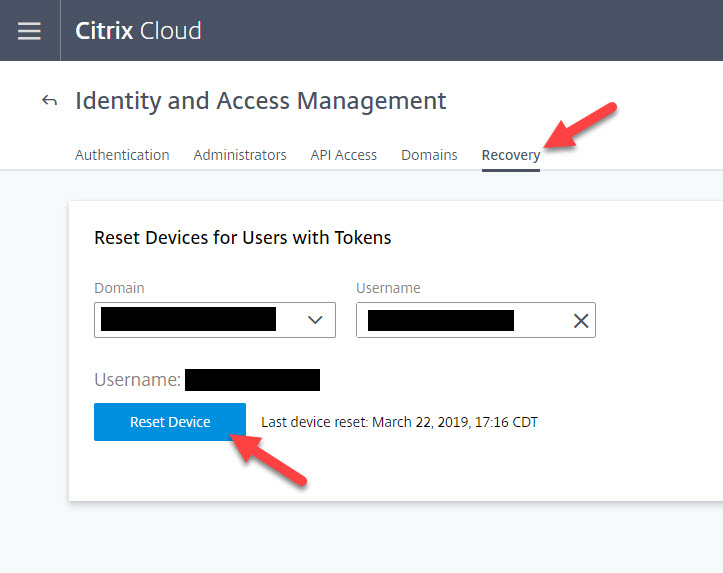
20. If your Service Desk needs to recover/reset a user who has lost their device, they can do this from within the Citrix Cloud console under Identity and Access Management > Recovery:
Final Thoughts
I encourage you to test this new option if you need it. You can test for a period of time on this Public Tech Preview and swing your Workspace auth back over to whatever you had it set to before without issue, just takes a few minutes. Your TOTP token on your phone does not have to be reset and you can use it again for future testing.
On user onboarding, as with many TOTP solutions, you can also enroll multiple devices with the same TOTP token by scanning the QR code with these devices when it is presented on the computer screen. You can also screenshot the QR code for later or save the alphanumeric code that is displayed and enter it manually into your authenticator app of choice later as well. In some organizations, they want to limit TOTP to a single device while in others they are open to having the user choose which device(s) they want to have the TOTP token on. Just something to be aware of.
In the future, I hope to see a big push toward password-less authentication with this solution. MFA alone is a nice step toward better security but I feel going password-less is much better. It would be nice to see the Citrix SSO app have some intelligence and connectivity back to the Citrix Cloud to offer push notifications + biometric or PIN code in the future as an alternative to using commonly exploited/attacked Active Directory passwords.
Another future wish list item would be to be able to use this in nFactor like flows for contextual access like you can on your NetScaler/Citrix ADC today on-premises. I can see companies with existing MFA solutions in place taking advantage of this. Example: If the user is an employee then send them to Azure AD + Azure MFA since I have EMS licenses for them but if the user is a 3rd party contractor/vendor I do not have Microsoft licenses for, then send them to this native Workspace AD + TOTP token option.
Hope this has helped give you an intro to this new multi-factor authentication capability of Citrix Workspace. Please leave a comment below if you have any questions.


Daureo Silva
June 12, 2019 at 12:28 PM
Another top notch post!
phil chivers
February 10, 2022 at 6:09 AM
Nice article that covers an important security subject. If it works with google authenticator, then it should work with the alternative authenticaors (such as safeid authenticator) that make it easier to transfer between devices etc.