A friend showed me a little trick to craft a special email message with the ability to attach any executable and it will go through to the recipient with no issue. You don’t even have to rename the extension from .exe to something else. I said no way, that’s not possible. There are too many layers of email security in place that will quarantine it in a heartbeat. You won’t be able to replicate this, every environment is unique, there’s no way this is possible. Then he pulled out his laptop and actually did it right in front of me. I was floored…
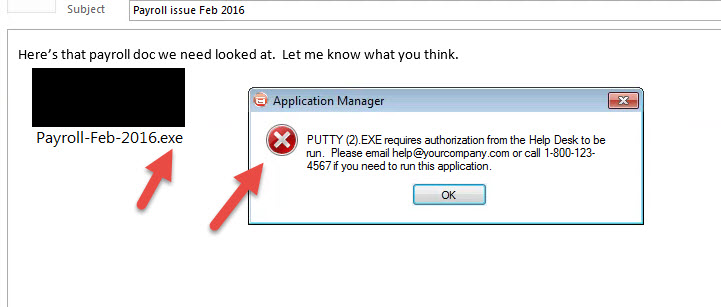
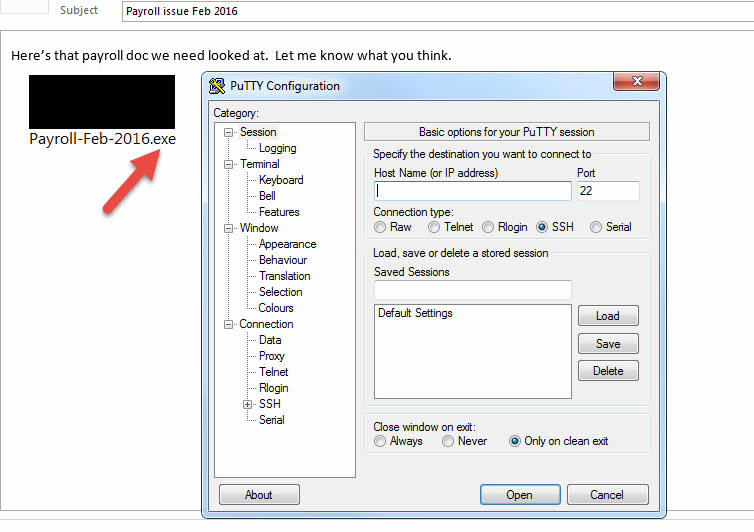
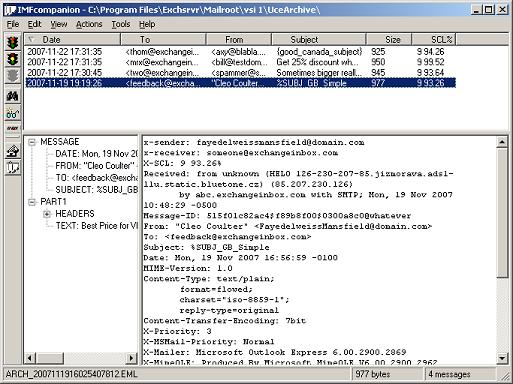
I spent all evening replicating and testing this in my lab through the most popular on premise and cloud based enterprise email systems. I even tested it through 4 different enterprise class spam filters/mail gateways. I decided to use putty.exe for testing since it was small. All I did was rename putty.exe to something a user might want to click on but I left the suffix .exe alone. In every test, the .exe came right through except for one cloud based email provider which stripped out the .exe payload but still left some remnants behind. In all the other tests it was never quarantined or flagged. Just shows up right at the top of my Inbox and I can run the attachment. I redacted some info that might give away how this is done, but here’s the proof:
Mind blowing, isn’t it?
WHY YOU SHOULD YOU BE WORRIED
In an enterprise environment it is the duty of the Information Technology department to protect not only the information but the users, most often from themselves. All it takes is 1 user to click on a phishing email or malware executable and if your anti-virus definitions can’t detect it, it’s going to have full reign of your environment. If you don’t have multiple layers of security on every egress and ingress point on your network, you should definitely be worried. Keyword being multiple. When one is defeated another should hopefully catch it. In this case one or more of those very important layers that all enterprises rely on to protect their email infrastructure doesn’t work against this exploit.
HOW THIS IS POSSIBLE?
I’m not going to disclose how this is possible but I have reached out to security teams at the vendors I tested against to investigate. I’m also reaching out to the spam filter/mail gateway manufacturers that I tested about this and see why they could not detect this. These are some pretty big name products in the industry so I’m honestly shocked this is even possible.
WHAT YOU NEED TO BE DOING
I said to myself the #1 company in almost every enterprise providing email services to people needs to know about this so I set out to report it to Microsoft so they could investigate. What’s funny is when you report a security issue on Microsoft’s website here:
https://technet.microsoft.com/en-us/security/ff852094.aspx
They talk about the 10 Immutable Laws of Security before you send an email to them. A couple of them stood out to me:
Law #1: If a bad guy can persuade you to run his program on your computer, it’s not solely your computer anymore.
Law #8: An out-of-date anti-malware scanner is only marginally better than no scanner at all.
This is absolutely true. For Law #1, it doesn’t matter how much training you give to users, they’re going to do things that don’t fall in line with your IT policy. You can only do so much. There’s a fine line between security and usability. You don’t want to make your systems unusable so the users have to be given a bit of wiggle room to do their daily tasks. It’s just that sometimes even with the least amount of freedom they can get into trouble.
For Law #8, anti-virus should only be one of the layers you are running in your environment. In my opinion you need to be running another layer of security on your system that doesn’t rely on virus definitions like AppSense Application Manager (http://www.appsense.com/products/application-manager/).
Here’s the proof why:
It’s the only thing that blocked the executable from running. Application Manager saw that I was attempting to run this putty.exe process but I am not permitted to since the Application Manager policy does not trust it and it has not been whitelisted. It immediately clamps down on it and prevents execution. It didn’t care what I, the user, was doing on the system. It didn’t care how many spam filters the executable walked right through. It didn’t care if anti-virus caught it or not. All it cared was it was something foreign to the environment and I wasn’t allowed to run it. End of story.
I’ve worked with some large financial institutions and health organizations in my career. They love VDI. Virtual Desktop Infrastructure, especially non-persistent pooled virtual desktops, offer a wonderful cost savings and provide a very measurable level of security. The users are task based shift workers which is the perfect use case for non-persistent VDI. I see them used on kiosks/thin clients in these industries and once the banker or doctor logs out, the virtual desktop image is reset and any manipulations to the system however inadvertent are gone. A malware free clean gold image every time ready for the next user to login.
I’ve talked to some high security organizations where physical security is paramount. Multi-factor authentication is required to do anything, even when on the internal environment. They’ve even taken physical security to the extreme and gone as far as epoxying the USB ports on the PCs. You see what I’m saying about multiple layers of security?
But any day could be a day like I experienced, where several layers of security you thought might be very solid can fail and you’re left with relying on what’s running on your endpoints. What good are smart cards and all the epoxy at Home Depot if the user clicked on an executable in an email you thought they would never be able to receive? Any layers of security you can add to your endpoints should be explored. All it takes is one incident that can change your mind over night.